Network Anomaly Detection Based on Wavelet Analysis
Full text
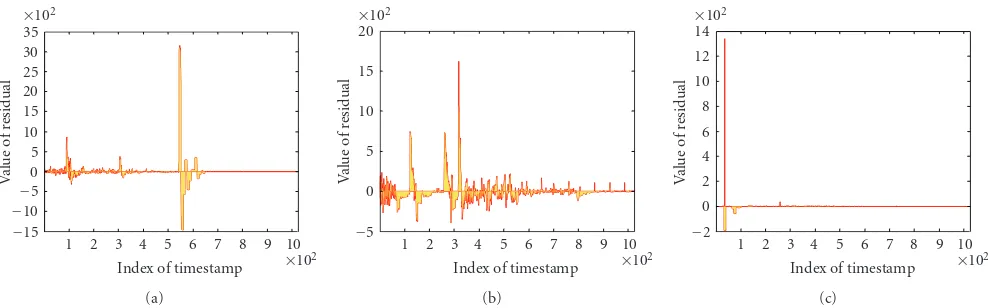
Figure



Related documents
This Code of Practice is a key component of the information security management framework that replaces prior Information Management and Technology security guidance published by
We provide an empirical application of the model, in which we show by means of stochastic dominance tests that the returns from an optimal portfolio based on the model’s
12.1 The Organizing Committee shall establish simplified customs procedures through the customs consultative committee, and details of the applicable custom
Tandberg Data offers a powerful combination to meet the needs of SMBs looking for a tape solution to address the dual demons of rising energy costs and growing data
If you have memory problems or hallucinations and your doctor has pre- scribed you an ‘anti-cholinergic’ medication, there is a chance that these medications can make these
Therefore, a highly important requirement was to develop a performance appraisal instrument that would reflect the way experienced supervisors in the Navy concep- tualized
certified professional Engineers SHOULD all have their personal digital signature in order have their personal digital signature in order to conduct their own professional
Specifically, we find a prediction gain (defined as the ratio of the fraction of predicted events over the fraction of time in alarms) equal to 21 for a fraction of alarm of 1%,