Certificate Based Encryption for Securing Broker-Less Publish/Subscribe System in Wireless Network
Full text
Figure
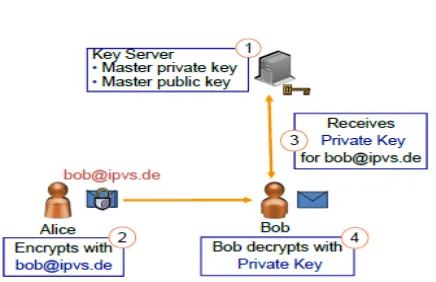


Related documents
rication of structural components made from the magnesium alloy is described in [26]. In recent years, the modeling of superplastic forming has been widely used in order to optimize
Further- more, we compared our approach with two different base lines: (i) a method exploiting only the frequency of semantic relations of length 1 within linked data (no heuristics
Recently, methods to assess the similarity of utilisation distributions have been developed and have been used to visualise and compare patterns of similarity in space use over
Assim, para compreender a dimensão duchampiana na produção do autor catalão, especialmente nos romances Aire de Dylan e Historia abreviada de la literatura portátil , é
educators choose to utilize the museum to supplement their curricula?” The research is funded by the Andrew W. Mellon Foundation and is being facilitated by staff members of
Also, considering the crime of rape during conflict from the viewpoint of a legal professional, Interviewee 16, a male lawyer, emphasized that the government should pay
It is vital that partners provide UWS with the necessary information (eg. timesheets, expenses, progress reports, dissemination information) in a timely manner