CSEIT1831210 | Received : 20 Jan 2018 | Accepted : 07 Feb 2018 | January-February-2018 [(3) 1 : 821-826 ]
International Journal of Scientific Research in Computer Science, Engineering and Information Technology © 2018 IJSRCSEIT | Volume 3 | Issue 1 | ISSN : 2456-3307
821
Keyword Search On Encrypted Cloud Data Using GDFS
G. Deepika1, N. V. Sailaja2
1PG Scholar (M.TECH), Department of Computer Science and Engineering, VNR Vignan Jyothi Institute of
Engineering and Technology, Hyderabad, India
2Assistant Professor, Department of Computer Science and Engineering, VNR Vignan Jyothi Institute of
Engineering and Technology, Hyderabad, India
ABSTRACT
Cloud computing in any case, individuals can appreciate full advantage of distributed computing on the off chance that we can address genuine protection and security worries that accompanies putting away delicate individual data. For genuine security, “client character ought to stay avoided cloud specialist organization and to ensure protection of information, information which is delicate is to be encoded before outsourcing. Along these lines, empowering a scrambled cloud information look benefit is of awesome significance. By thinking about the extensive number of information clients, archives in the cloud, it is imperative for the pursuit administration to permit multi catchphrase question and give result likeness positioning to meet the powerful need of information recovery look and not frequently separate the indexed lists”. I initially propose an essential thought for the Multi-keyword ranked search in cloud information in light of secure internal item calculation and effective likeness measure of arrange coordinating, at that point can give two fundamentally enhanced MRSE plans to accomplish different stringent protection prerequisites in two diverse risk models.
Keywords: Cloud Computing, Searchable Encryption, Privacy Preserving, Keyword Search, Ranked Search Anonymization, MRSE.
I.
INTRODUCTION
Cloud computing is the since a long time ago imagined vision of figuring as an utility, where cloud clients remotely store their information into the cloud in order to appreciate the on-request great applications and administrations from a mutual pool of configurable registering assets [12]. “Its extraordinary adaptability and financial funds are propelling the two people and ventures to outsource their nearby complex information administration framework into the cloud. To secure protection of information and contradict spontaneous gets to in the cloud and past it [6], delicate information, for example, messages, individual wellbeing records, photograph collections, charge reports, The inconsequential arrangement of downloading every
one of the information and decoding locally is plainly unreasonable, because of the expansive measure of data transfer capacity cost in cloud scale frameworks. Pictures additionally contain valuable and critical data, so proposed framework likewise gives picture labeling in MRSE scheme [1]. Also, besides killing the neighborhood stockpiling administration, putting away information into the cloud doesn't fill any need unless they can be effortlessly looked and used”.
[13]. Archive positioning is accommodated quick pursuit, yet the needs of the considerable number of information records is kept same with the goal that the cloud specialist organization and outsider stays ignorant of the imperative reports, therefore, keeping up protection of information.
Ranked search can likewise richly dispose of superfluous system activity by sending back just the most important information, which is profoundly attractive in the "pay-as-you-utilize" cloud worldview. “For security assurance, such positioning operation, be that as it may, ought not to release any catchphrase related data. Moreover, to enhance item exactness and also to upgrade the client seeking background, it is additionally important for such positioning framework to help numerous catchphrase search[1][2], as single watchword look regularly yields dreadfully coarse outcomes. As a typical practice demonstrated by the present web crawlers (ex. Google look), information clients may have a tendency to give an arrangement of watchwords rather than just a single as the marker of their pursuit enthusiasm to recover the most pertinent information. Alongside the security of information and effective looking plans [6], genuine protection is gotten just if the client's personality stays escaped the Cloud Specialist co-op and the outsider client on the cloud server”.
II.
RELATED WORK
The fundamental point is to discover the arrangement of multi-catchphrase positioned seek over encoded cloud information while saving strict framework savvy security in the distributed computing worldview. In particular "inward item closeness", i.e., the quantity of question watchwords showing up in an archive, to quantitatively assess such likeness measure of that record to the inquiry is utilized as a part of MRSE system. [14]When the advantages of utilizing an open cloud framework are clear, it presents critical security and protection
obstruction to the appropriation of distributed storage (and distributed computing as a rule) is worry over the privacy and honesty of information.
[7] “The paper has characterized and tackled the testing issue of protection saving multi-catchphrase positioned look over scrambled cloud information (MRSE), and builds up an arrangement of strict protection prerequisites for such a safe cloud information use framework to wind up noticeably a reality”.
[6] “The paper tells the significance of ensuring person's protection in distributed computing and gives some security safeguarding advances utilized as a part of distributed computing administrations. From this paper, primary subject taken is of saving protection of information”.
[12] “In this paper, a calculation for mysterious sharing of private information among N parties is produced. Existing and new calculations for doling out mysterious IDs are inspected regarding exchange offs amongst correspondence and computational necessities”.
[10] This fundamental thought is taken however it is for multi-catchphrase raked seek (MRSE plot) in our proposed framework. Plan of secure distributed storage benefit which tends to the unwavering quality issue with close ideal general execution is proposed.
III.
DESIGN METHODOLOGY
Existing System
The accessible encryption has been as of late created as a basic way to deal with empower looking over scrambled cloud information, which goes before the accompanying operations. Wang et al. propose a positioned watchword seek plot which considers the significance scores of catchphrases.
Disadvantages Of Existing System
Due to utilizing Order Preserving Encryption (OPE) to accomplish the positioning property, the current plan can't accomplish unlinkability of trapdoor.
Although numerous hunt functionalities have been produced in past writing towards exact and proficient accessible encryption, it is as yet troublesome for accessible encryption to accomplish a similar client encounter as that of the plaintext look, similar to Google seek.
Proposed System
In this work, we address by creating two Fine-grained Multi-keyword Search (FMS) plots over scrambled cloud data.In this framework, we present the significance scores and the inclination components of watchwords for accessible encryption. The significance scores of catchphrases can empower more exact returned comes about, and the inclination components of watchwords speak to the significance of catchphrases in the inquiry catchphrase set determined via look clients and correspondingly empowers customized hunt to take into account particular client inclinations.
Advantages Of Proposed System
1. Better indexed lists with multi-keyword query by the cloud server as indicated by some positioning criteria.
2. To decrease the correspondence cost.
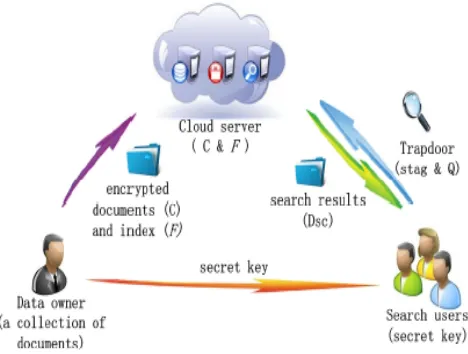
Figure 1. System architecture
The main donations of work are described as follows: 1. Multi keyword rank search
2. Encryptions of data with AES 3. Cloud setup.
4. Greedy Depth First Search technique.
Mrse System
For our life form, we pick the state of mind of blend coordinating, to recognize the correspondence in the midst of pursuit request and information certifications. Especially, we utilize inward information correspondence, i.e., the figure of inquiry watchwords showing up in a report, to assess the likeness of that record to the pursuit question in facilitate coordinating principle. “Each archive is associated with a parallel vector as a sub record where each piece speaks to whether comparable to watchword is contained in the document. The inquiry reservation is likewise portraying as a double vector where each piece implies in the case of comparing watchword shows up in this pursuit ask for, so the similitude could be precisely estimated by internal result of question vector with data vector”. In any case, specifically outsourcing information vector or inquiry vector will encroach record security or pursuit protection.
criteria. CS just sends back best k archives that are most applicable to the inquiry question.
In the longed for living being the stream begins from the client. The client needs to enlist in CSP to get the pleasantries. “When client information is put away in CSS it has no unswerving control above it. Client needs to procure any evaluator called TPA who will consistently check the client information in CSS. The TPA ought to be conceded by the client to check the uprightness for particular information and for an unambiguous time without getting to the correct information. Beneath a calculation is give which portray how the TPA does the audit” [14].
AES calculation is utilized to store the information in encoded shape in cloud server. So when TPA does the review it just gets the bogus impression of unique documents. The qualities on which TPA figures or check the respectability is really the hash estimation of scrambled record ascertained agreeably. Client can whenever allow or repudiate the concession from TPA. Client has the benefit to transfer, download and alter information. Client's alter ask for is additionally served for a particular piece of the document rather than recover the entire file [6].
Algorithms
Setup (1l): A security parameter as info, the information proprietor yields a symmetric key as SK.
Build Index (F, SK): “In view of the informational collection F, the information proprietor constructs an accessible file I which is encoded by the symmetric key SK and after that outsourced to the cloud server. After the record development, the archive gathering can be autonomously encoded and outsourced”.
Trapdoor (W): With t keyword of enthusiasm for W as info, this calculation produces a comparing trapdoor TW
Query (TW, k, I): At the point when the cloud server
positioned look on the list I with the assistance of trapdoor TW, lastly returns FW, the positioned id rundown of best k archives arranged by their closeness with W.
GDFS (IndexTreeNode u)
If the node u is not a leaf node then If Score(Fu, Q) > kth score then
Sort the children of u in descending order according to scores of children
For i=1 to the number of children of u do
GDFS(u.child[i]); End for
Else Return; End if
Else
If Score(Fu, Q) > kth score then
Delete the element with a smallest relevance score from RankedList;
Insert a new element (Score (Fu, Q), u.ID) and sort all elements of RankedList in descending order;
End if Return; End if
Security Analysis
Here we give investigation of the EMRS regarding secrecy of archives and file, trapdoor protection, trapdoor unlink capacity and hiding access example of the inquiry client.
IV.
CONFIDENTIALITY OF DOCUMENTS AND
INDEX
more, the descriptors of the reports are scrambled utilizing CP-ABE strategy. Along these lines, the cloud server can just utilize the list z to recover the scrambled significance vectors without knowing any extra data, for example, the relationship between the reports and the catchphrases. What's more, just the pursuit client with amend quality keys can unscramble the descriptor ABE_i (idijjKijjx) to get the record id and the related symmetric key. In this way, the classification of archives and file can be all around secured.
Trapdoor Privacy
At the point when a pursuit client produces her trapdoor including the catchphrase related token stag and encoded inquiry vector Q, she haphazardly picks two numbers r and t. At that point, for the question vector q, the pursuit client expands it as (rq; r; t) and scrambles the inquiry vector utilizing the mystery key M1;M2 and S. Hence, the question vectors can be very surprising regardless of whether they contain same catchphrases. What's more, we utilize the protected capacity 9 and 0 to enable the pursuit client to process watchword related token stag utilizing the mystery key K9. Without the mystery key M1;M2; S and K9, the cloud server can't attempt into the trapdoor and the pursuit client can add sham numbers to the set Sf to hide what it is genuinely scanning for. Along these lines, the watchword data in the trapdoor is completely disguised from the cloud server in the MRSE and trapdoor security is all around ensured.
Implementation Result
In usage plane the significant benefits are: information security protection shield Examining subtle elements to the information proprietor Review bent mindful information booking as of now we will assess the execution of our anticipated plan regarding the calculation overhead present by every operation. Demand and assets are taken as the processing parameter. At the point when the quantity of solicitations increments in the meantime, it is to check whether they are served to another client or
not, on the off chance that it is served the rank will be expanded.
Keyword Privacy:
In this plan, the secrecy of the record and question are very much secured that the first vectors are kept from the cloud server. What's more, “the inquiry procedure just presents inward item figuring of encoded vectors, which releases no data about a particular catchphrase. Accordingly, the catchphrase security is ensured in the known figure model. Be that as it may, in the known foundation display, the cloud server should have more information, for example, the term recurrence measurements of watchwords”.
V.
CONCLUSION AND FUTURE WORK
In future we need to enhance more on security issues of information stockpiling on distributed storage benefit. On distributed computing this subject isn't debatable to move forward. For actualizing that procedure we increment the layers of verifications. In our future work, we will go around checking the trustworthiness of the rank request in the query item expecting the cloud server is untrusted.
VI.
REFERENCES
[1]. N. Cao, C. Wang, M. Li, K. Ren, and W. Lou, “Privacy-Preserving Multi-Keyword Ranked Search over Encrypted Cloud Data,” Proc.IEEE INFOCOM, pp. 829-837, Apr, 2011.
[2]. Zhihua Xia, Member, IEEE, Xinhui Wang, Xingming Sun, Senior Member, IEEE, and Qian Wang, Member, IEEE, “Secure Ranked Keyword Search over Encrypted Cloud Data”, IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS 2016.
[3]. International Journal of Emerging Technology and Advanced Engineering Website: www.ijetae.com (ISSN 2250-2459, ISO 9001:2008 Certified Journal, Volume 4, Issue 2, February 2014).
[4]. Privacy preserving public auditing for Secure Cloud Storage”, Cong Wang, Sherman S.-M. Chow, Qian Wang, Kui Ren.
[5]. Shiba Sampat Kale et al, / (IJCSIT) International Journal of Computer Science and Information Technologies, Vol. 5 (6) , 2014, 7093-7096
[6]. Kuchi Ravi Kishore, et al International Journal of Computer and Electronics Research [Volume 4, Issue 2, April 2015]
[7]. Li, S. Yu, N. Cao, and W. Lou. Authorized private keyword search over encrypted data in cloud computing. In Distributed Computing Systems (ICDCS), 2011 31st International Conference on, pages 383–392. IEEE, 2011 [8]. Boldyreva, N. Chenette, Y. Lee, and A. O’Neill.
Order-reserving symmetric encryption. In
Proceedings of Eurocrypt'09, volume 5479 of LNCS. Springer, 2009.
[9]. Wang, K. Ren, S. Yu, K. Mahendra, and R. Urs, “Achieving Usable and Privacy-Assured Similarity Search over Outsourced Cloud Data,” Proc. IEEE INFOCOM, 2012.
[10]. Boldyreva, N. Chenette, Y. Lee, and A. O’Neill. Order-preserving symmetric encryption. In Proceedings of Eurocrypt'09, volume 5479 of LNCS. Springer,
[11]. International Journal of Advance Research, IJOAR.org Volume 3, Issue 2, February 2015, Online: ISSN 2320-9194
[12]. C. Clifton, M. Kantarcioglu, J. Vaidya, X. Lin, and M. Y. Zhu, ― Privacy Preserving Data Sharing With Anonymous ID Assignment,‖ ACM SIGKDD Expl
[13]. M. Armbrust, A. Fox, R. Griffith, A. D. Joseph, R. H. Katz, A. Konwinski, G. Lee, D. A. Patterson, A. Rabkin, I. Stoica, M. Zaharia, "Above the clouds: A berkeley view of cloud computing", Tech. Rep. USB-EECS-2009–28, University of California, Feb 2009.