Peter Rysavy, Primary Contributing Writer
GPRS Network Security
Document Number 12199 Revision 0.4.5
Copyright Notice
This work is protected by the copyright laws of the United States and is the property of AT&T Wireless Services, Incorporated. Copying, reproduction, merger, translation, modification, or enhancement by anyone other than authorized employees or licensees of AT&T Wireless Services, without prior consent of AT&T Wireless Services, is prohibited. All trademarks or registered trademarks are the property of their respective owners.
For questions about this document, please contact:
Bonnie Beeman AT&T Wireless PO Box 97061-6742 Redmond, WA 98073
GPRS Network Security
Contents
1. Introduction...4
1.1. The Need For Security ...4
1.2. Defining and Implementing an Effective Security Policy...6
2. AWS GPRS Security Summary...8
2.1. AWS GPRS Network Architecture...9
2.2. Network Interfaces...12
3. Mobile Station to Network Interface ...15
4. IP Address Management ...18
4.1. IP versus PPP Service ...18
4.2. IP Addresses ...20
5. Internal Network Interfaces ...22
5.1. AWS GPRS Network ...22
5.2. Intercarrier Interface ...23
6. External Network Interface ...25
6.1. Naming (APNs) and Routing ...26
6.2. Frame Relay Connections ...26
6.3. AT&T Wireless Connectivity Option - Frame Relay...27
6.4. Internet Interface ...28
6.5. Virtual Private Network (VPN) Discussion...28
6.6. Managed Internet Connection ...31
6.7. Client VPN Solution ...32
7. GSM/GPRS Mobile Internet Phone...33
8. Enhanced Data Rates for GSM Evolution (EDGE)...36
Appendix A: Data-Security Technologies and Standards ...38
1. Introduction
This document provides a high-level description of the security considerations associated with using General Packet Radio Service (GPRS) from AT&T Wireless Services (AWS). It addresses security concerns and identifies standard and optional solutions to address customers’ security needs.
GPRS is a wireless packet-data data service for Global System for Mobile Communications (GSM) cellular networks. AWS is deploying GSM and GPRS throughout its coverage areas. GPRS security
mechanisms are based to a large extent on GSM security mechanisms, ones that have withstood the test of time and the extremely widespread use involving hundreds of millions of users worldwide.
This document explains the security features of the AWS GPRS service and clarifies how these features would best augment a
company’s security policy to achieve a complete security solution. It is intended for users of wireless data services who may have concerns about the security of their data but who may not be familiar with the various security features, mechanisms and options of the AWS GPRS service. Most of the security mechanisms discussed in this paper will also apply to forthcoming wireless technologies from AWS such as Enhanced Data Rates for GSM Evolution (EDGE) and Universal Mobile Telephone System (UMTS).
1.1. The Need For Security
Many of the ways we communicate today are via relatively insecure channels. For instance, we regularly use non-secure phone lines for voice and modem communication. By contrast the AWS GPRS service offers significant security features that resist attack by a passive airlink eavesdropper or a malicious network user.
Ensuring network security in the modern world is driven by the need to:
• Maintain the confidentiality and integrity of sensitive information
in a distributed network environment
• Protect the identities and information communicated by customers
• Prevent attacks that deny the availability of services
• Prevent fraudulent use of services
• Provide necessary information to defense and law enforcement
agencies
However, securing an organization or company's data network and its various interconnections presents a challenge. Adding remote access using a wireless network adds to the challenge, but this challenge can be accommodated through deployment of security technologies available today.
It should be noted that implementing a security policy requires careful analysis. An organization must understand the technological
considerations of network security and must balance the cost of security measures against its potential benefits. While security measures prevent and/or reduce the risk of unauthorized access, security may also reduce productivity by creating additional processing and work overhead. Security measures may also create expensive administrative and educational overhead, as well as use significant computing resources that require dedicated hardware. For corporate facilities, physical security is usually based on security guards, card-key entry systems, closed-circuit television, and off-limits areas. With these security measures in place, an organization can feel confident that within their physical facilities, assets are protected, and high user productivity is maintained. To extend this physical security model into the virtual world of internal and external networking and Internet access, organizations must decide where to strike a balance between access, productivity, and security measures that may be perceived as restrictive by users of the organization's network. The primary goal of a good security policy and design is to meet security requirements while adding as few restrictions as possible from the network user's perspective. It is of utmost importance for
of access is needed. For example, an organization may need strict protection on its accounting databases, but may need only limited protection on its internal mailing list. The important point is that any decision to invest in security systems must answer two questions:
• How valuable is the information that is being protected?
• What is the perceived level of threat to the information?
Extending a corporate security policy to include wireless data networks requires an understanding of the security features of the wireless data technology, as well as the security provided by networks to which the wireless network provides access.
1.2. Defining and Implementing an Effective Security Policy
An effective security policy is best defined after thorough analysis of an organization's unique security issues. These security issues must be resolved in order to implement an effective security policy:
• Know the company or organization's assets. An organization
needs to understand what they want to protect and what level of access is appropriate. An organization may discover that certain parts of the infrastructure can be left open because there is little cost involved if these parts are somehow compromised.
• Balance the cost of security. Security costs must be in proportion
to the actual dangers; otherwise, the cost could be unnecessarily burdensome to the entire organization. It is also important to understand how technological considerations relate to cost. For example, an organization may not have the capacity or resources to replace legacy systems that may not be supported by their original vendors. In this case, it may not be possible to implement new technical options such as encryption.
• Identify security assumptions. It is inherently dangerous for an
organization to assume that its network is not compromised, that intruders are not very knowledgeable, that they are using standard software, or that a locked room is safe. It is important to examine and justify assumptions; any hidden assumption is a potential security risk.
• Allow for human factors. If security measures interfere with
circumvent them. For example, because automatically generated "nonsense" passwords can be difficult to remember, users often write them on desktops, on the undersides of keyboards, or on other surfaces which can easily be seen by others, and in this way render a password protection measure self-defeating. In order to achieve compliance, users must understand and accept the need for security and, more importantly, security measures must be
reasonable, allowing users to get their work done.
In order to detect security problems, an organization must understand how a system normally functions, how devices are normally used, and what typical behavior to expect. Detecting unusual behavior, tracking this behavior, and logging unusual events, can help catch intruders before they can damage the system.
An organization must create barriers within their system so that if an intruder accesses one part of a system, they do not automatically have access to the rest of the system. Partitioning should be considered in order to provide as much protection as necessary for network
components. Although maintaining a high level of security on the entire infrastructure is difficult, it is often possible to do so for smaller, sensitive components.
Almost any change made to a system can affect security. This is especially true when new services are created. System administrators, programmers, and users should consider the security implications of every potential system change. Understanding the security
implications of a change takes practice; it requires lateral thinking and a willingness to explore every way that a service could potentially be manipulated. Another goal of a good security design and policy is to create an environment that is not susceptible to every minor system change.
It is not the intent of this document to be a complete tutorial on wireless security. Rather, it is intended as a guideline for identifying security considerations when using the AWS GPRS service. There are many good books and Internet-hosted information on the subject of security. For reference, some general information on network security is provided in “Appendix A: Data Security Technologies.”
2. AWS GPRS Security Summary
The AWS GPRS service was designed with security in mind. It is based on GPRS technology, a data service for GSM networks. The GPRS security architecture is comprehensive, proven (since it is based on GSM technology) and does not suffer from the security
shortcomings of some other wireless technologies.
Not only does GPRS technology contain comprehensive security provisions, but AWS has augmented its network with additional security functions. The key benefits of these combined measures include:
• User identities are protected.
• Only legitimate mobile systems can connect to the network.
• All user data transmitted over the airlink is encrypted.
• Encryption keys between the mobile system and the GPRS network
change each time the mobile system connects to the network. This means that even if an intruder were able to determine the key for one session, the key would be useless for subsequent sessions. In addition, the network can update the keys at periodic intervals.
• Customers networks connected to the AT&T GPRS service by
frame relay service are protected against attacks from the Internet. In addition, AWS offers a managed Internet connection that employs virtual private networking (VPN) technology to allow secure communications across the Internet.
• IP addresses, whether for mobile systems or fixed-end systems, are
never transmitted "in the clear" (unencrypted) over the airlink, reducing the risk of attacks on both mobile and fixed-end systems.
The security aspects of the AWS GPRS service, as well as its connections to other networks, are summarized in the following sections entitled “AWS GPRS Network Architecture” and “Network Interfaces”. Subsequent sections of this document elaborate on select topics introduced in these summaries. Customers should be aware that different releases of the GPRS specification incorporate different security features. The current version of the AWS GPRS service is
based on release 98 of the GPRS specification (3GPP Technical Specification 03.60 V7.7.0.) The network will be upgraded to a newer version of the GPRS specification over time, resulting in potential changes or enhancements to security features.
2.1. AWS GPRS Network Architecture
The AWS GPRS service consists of specific network components. To understand the security aspects of the network, it helps to understand the basic network components between which data transfer occurs. It is also important to consider how the AWS GPRS service connects to other networks, such as customer networks and the Internet. It is also important to consider how the AWS GPRS service interconnects with GPRS networks from other carriers. The primary elements of a GSM and GPRS network are shown in Figure 1.
Mobile Switching Center Home Location Register Serving GPRS Support Node Gateway GPRS Support Node External Data Network (e.g.Internet) Base Station Controller Mobile Station Circuit Swithced IP Data Public Switched Telephone Network GPRS Addition Base Transceiver Subsystem Base Transceiver Subsystem Mobile Station Mobile Station Mobile Station Mobile Station GSM Network Visitors Location Register
Figure 1: Components of a GPRS network
The radio interface is between the mobile station and the Base Transceiver Subsystem (BTS). The BTS connects to a base station controller (BSC). The BSC separates voice and data traffic, with circuit-switched traffic directed to the Mobile Switching Center and packet-data traffic directed to the GPRS infrastructure. The Mobile Switching Center handles voice and circuit-switched data
The two key elements of the GPRS infrastructure are the Serving GPRS Support Node and the Gateway GPRS Support Node. The functions of these elements and other GPRS network elements, along with their associated security functions is described next.
• Subscriber Identity Module. One important security mechanism
is the SIM card. This is a small electronic card inserted into the mobile station that contains the user’s identification information. A user cannot gain access to network services (voice and data)
without a valid SIM card.
• Mobile Station (MS): This is the wireless computing device used
to connect to the GPRS network. Examples of MS include a GSM/GPRS mobile Internet phone, a notebook computer
connected to a GPRS modem or a PDA with GPRS modem. The network authenticates the GPRS device (e.g. modem) against credential stored in the subscriber identity module (SIM) card. The network can also optionally request a password from a user. All user data communicated between the MS and SGSN is encrypted. Since an MS can potentially be stolen, it is best to employ a security solution that does not rely solely on the MS hardware. For any sensitive information that can be accessed by applications on the MS, the user should be required to provide a password or be required to use a hardware token. Note also that the GSM/GPRS mobile Internet phone service employs architecture with separate security protocols. These protocols are detailed in the section entitled “GSM/GPRS Mobile Internet Phone”.
• Base Transceiver Subsystem and Base Station Controller:
These elements manage the radio interface, including the control of which MS has access to the radio channel at what time. These elements essentially relay messages between the MS and SGSN, and do not play a role in GPRS security.
• Serving GPRS Support Node: The SGSN manages
communications with an MS, sending and receiving data and keeping track of their location. The SGSN is the equivalent of the Mobile Switching Center for data functions. The SGSN obtains subscriber information from the Home Location Register (HLR) such as what services are available to the particular subscriber. The SGSN registers the MS, authenticates the MS, and encrypts data
sent to the MS.
• Gateway GPRS Support Node: The GGSN is the gateway to
external networks such as the Internet or private customer networks. The GGSN assigns IP addresses, and can also
authenticate users acting as a RADIUS client. If private IP
addresses are used, a server at the GGSN location performs the translation from private IP address to public IP address. Firewalls located at the GGSN also perform a firewall function to restrict
unauthorized traffic.
• Home Location Register: The HLR contains a database of
permanent user subscription information for both voice and data services. It also contains dynamic information about active users (e.g. current SGSN providing serving to a particular MS.) The HLR stores the necessary information to authenticate an MS.
• Visitors Location Register (VLR). The VLR contains a database
of subscription data for users of one (the typical case) or more MSCs. The VLR is used to manage roaming and provides more detailed mobility information on active users within an MSC administrative area.
• Fixed End System (F-ES): This element is the traditional external
data application system or internal network that supports and services application systems. By definition, its location is fixed. An F-ES can be one of many stationary-computing devices, such as a workstation or host computer. The customer maintains the F-ES and its security is the customer’s responsibility. In connecting the F-ES to the AWS GPRS service, the customer must ensure that they have an effective security policy, and that appropriate firewalls have been put in place. As discussed in the section, "External Network Interface" even if using a frame relay PVC to
connect to the AWS GPRS service, IP traffic can reach the F-ES that originates from any GPRS MS, whether or not the IP traffic belongs to the particular customer.
• Firewall: This element is responsible for controlling in and
out-bound network traffic. See Figure 2. Note that the implementation of the firewall is independent of the GPRS specification and will vary depending on GPRS service provider. The firewall function at the GPRS network is usually contained within or at the GGSN. A firewall implemented within the customer’s network operates independently of the firewalls in the AWS GPRS service and therefore is the customer’s complete responsibility.
• Border Gateway: This element is the interface to an intercarrier
network. See Figure 2. It's principal purpose is security. It restricts traffic between carriers to legitimate traffic only, e.g.
authentication of roaming users, user data and exchange of billing records.
• External Data Network: This element is the external networking
solution that covers a wide geographical area and provides a connection between an F-ES and the AWS GPRS service. The most common WAN connection for the AWS GPRS service is a frame relay circuit or the Internet. Security considerations are quite different for frame relay and Internet connections. These differing security considerations are described in the section "External Network Interface".
2.2. Network Interfaces
To further understand the security features of the AWS GPRS service security, we must next examine the key interfaces of the overall
network. Refer to Figure 1 above and Figure 2 below. Note we explore many of these topics in greater detail in subsequent sections.
SGSN
BSC Private IP Network (GPRS Operator 1) BTS
Mobile Station
Mobile Station
GPRS Provider 1
SGSN
BG
BG: Border Gateway
BTS: Base Transceiver Subsystem BSC: Base Station Controller GGSN: Gateway GPRS Support Node SGSN: Serving GPRS Support Node
GGSN, firewall Internet Inter Carrier GPRS Backbone SGSN BSC BTS Mobile Station Mobile Station
GPRS Provider 2
Private IP Network (GPRS Operator 2)
BG GGSN, firewall Private Intranet GGSN Private Intranet
MS to Network Interface
External Interfaces
Intercarrier Interface
Internal Interfaces
User
User Level Security
Application Level Security
User
User User
Figure 2: GPRS Network Interfaces
The summaries of the most important interfaces with respect to security are as follows:
• User Level Security: For a user to gain access to the GPRS
network, the user must have a SIM card for their GPRS device. SIM cards can be further protected by requiring a user to enter a personal identification number (PIN). If the user enters an incorrect PIN more than three times, further attempts are blocked until the user enters a special code that can only be obtained from the AWS customer care department. Note that AWS supplies GSM/GPRS equipment with the PIN function disabled; however the customer can re-enable it. Beyond these measures, customers can further enhance security to protect against lost or stolen mobile equipment with mechanisms such as hardware tokens or passwords at the application level.
• MS to Network Interface: This is an important interface as it
includes the radio interface. When an MS first connects to the network, the SGSN initiates an authentication process where the subscriber’s secret key contained in the SIM card is checked using
a challenge-response mechanism against information stored in the network. Following authentication, the MS and SGSN engage in an exchange that determines an encryption key. (Note that encryption is referred to as ciphering in GPRS technical documents.) This key is different for every data session, and is never transmitted over the air. From that point forward, data communications between the MS and SGSN is encrypted. This interface is described in more detail in the section “Mobile Station to Network Interface.”
• GPRS Internal Network Interfaces: Communications between
GPRS elements occurs over private networks, and AWS takes reasonable precautions to protect these networks against
unauthorized traffic, eavesdropping and denial of service. Portions of the network, such as user data communications between the SGSN and GGSN may even be encrypted. However, customers should not rely on internal security measures of the network to protect the confidentiality of their data. For any sensitive data, customers are advised to add their own security provisions. This interface is described in the section “Internal Network Interfaces.”
• Intercarrier Interface: This is the interface at the Border Gateway
between the AWS GPRS service and other service providers, such as other cellular-telephone companies providing GPRS service and with whom AWS has roaming agreements. These include
companies such as Cingular Wireless and T – Mobile. In some cases, GPRS carriers are linked through a GPRS roaming exchange, a network that links multiple carriers together. The Border Gateway performs a firewall function restricting traffic to authorized communications. Other security functions may be present, but customers should employ their own security provisions for sensitive data. This interface is described in the section
“Internal Network Interfaces.”
• External Interface: This is the interface between the AWS GPRS
service and networks that connect to the customer network where the F-ES resides. The F-ES is part of the customer's network, and its security is the responsibility of the customer. The most common network connections are via a frame relay permanent-virtual circuit (PVC) or via the Internet. AWS has specific service offerings for both frame relay and the Internet. Some security is provided by the
firewall function at the GGSN in the AWS GPRS service, but customers should not necessarily rely solely on this firewall. This interface is described in more detail in the section “External Network Interface.”
3. Mobile Station to Network Interface
This section discusses the security mechanisms between the mobile station and the AT&T GPRS network. These mechanisms include authentication of the mobile station, key derivation, and encryption. Customers should also note that unlike other wireless technologies (e.g. wireless LANs) where an intruder can easily monitor radio communications using commercial subscriber equipment,
eavesdropping on a GSM/GPRS radio signal requires sophisticated equipment. This is due in part to the way GSM networks divide communications into time slots.
During operation, the GPRS network first authenticates the user using a challenge-response mechanism. This GPRS authentication
mechanism is similar to GSM voice service authentication, except that it is conducted by the SGSN (responsible for packet-data service) instead of the MSC (responsible for circuit-switched services such as voice). The SGSN sends a random 128 bit number (the challenge) to the MS which computes a 32 bit response based on this number and its secret subscriber authentication key (called the Ki key which is stored in the SIM card) using a GSM algorithm called A3. The SGSN does the same calculation and matches the response from the MS with its own calculated value, and if they are the same, the MS is successfully authenticated and allowed to engage in further communications with the network. The SGSN obtains the secret subscriber key and random number from the HLR associated with the MS. This
challenge-response mechanism avoids transmitting the secret subscriber key over the radio interface.
Once an MS has been authenticated, the next step is to produce an encryption key. This 64-bit key is calculated by both the MS and the network by applying a key-generating algorithm called A8 to the random number previously used for authentication and the secret subscriber key. Once the encryption key is derived, communication
between the MS and the GPRS network is encrypted using an algorithm called GPRS-A5, a modified version of the A5 algorithm used within GSM networks for voice communication. GPRS-A5 is optimized for packet-data communications. The protocol level that handles encryption is called the Logical Link Control (LLC) layer. LLC operates between the MS and SGSN at layer 2 of the network reference model. See Figure 3. Both signaling (control) information and user data are processed by the LLC layer, and so the network keeps both user data and control information such as a user’s location confidential.
The GPRS process of authentication and encryption differs from CDPD networks. With GPRS, authentication precedes derivation of the encryption key whereas with CDPD, derivation of the encryption key precedes authentication.
Once a user has a GPRS session (referred to as a packet data protocol context) activated, not only does the network protect the
confidentiality of users’ IP data, but also their SMS messages. SMS messages are delivered via the SGSN, using the LLC protocol layer, and so are also encrypted.
GSM RF MAC LLC SNDCP IP GSM RF
MAC Frame Relay Frame Relay
LLC TCP/UDP IP Layer 2 TCP/UDP IP Layer 2 IP Mobile Station Base Station Subsystem Serving GPRS Support Node Gateway GPRS Support Node
SNDCP: Subnetwork Dependent Convergence Protocol LLC: Logical Link Control RLC: Radio Link Control
MAC: Medium Access Control GSM RF: GSM Radio Frequency Layer
BSSGP: Base Station Subsystem GPRS Protocol GTP: GPRS Tunnel Protocol
RLC RLC Relay BSSGP BSSGP Layer 1 Layer 1 Layer 1 Layer 1 SNDCP Relay GTP GTP Encrypted Communications
Figure 3: GPRS Protocols
To further enhance security, the network can re-authenticate an MS, and also derive a new encryption key at periodic intervals. The operator controls how often this happens based on current security needs.
Neither the secret subscriber key, nor the encryption key are ever transmitted over the radio link. All that is transmitted is the 128 bit random number, which by itself is useless to an eavesdropper. At the MS, both the authentication response and the encryption keys are computed within the SIM card which physically restricts information about its contents. Details of the A3, A8 and GPRS-A5 algorithm are deliberately not made publicly available to further increase the security of GSM and GPRS networks.
Even before encryption begins, the network protects a user identity by assigning temporary user identification. The user’s actual International Mobile Subscriber Identity (IMSI), which identifies the user account, or any information allowing somebody to derive the IMSI easily are not normally communicated over the air in clear text. This protects users from eavesdroppers who might identify a user’s account information or location prior to the start of encryption.
There is one additional level of authentication that can optionally be invoked between the MS and GPRS network. The network can request that the user enter a password. The network forwards the password to the GGSN which acting as a Remote Authentication Dial-In User Service (RADIUS) client, submits the password for authentication to a RADIUS server. This form of authentication is available for customers using either GPRS IP or PPP services.
Customers should be aware that the MS does not explicitly authenticate the GPRS service. But the fact that the network can calculate the A8 encryption key, indicating knowledge of the Ki key, does provide a level of indirect authentication.
4. IP Address Management
Before examining other aspects of the AWS GPRS service, it is important to have an understanding of how the network manages IP addresses, as this has security implications.
There are two items to consider. One is the difference between IP and PPP service. The other is how the network manages IP addresses.
4.1. IP versus PPP Service
Most customers use an IP-based service. This means that the AWS GPRS service assigns an IP address to an MS, and then transports IP datagrams between the GGSN and the MS, with the GGSN acting as a gateway to external networks. In this case, the network manages how IP datagrams are routed to users and with which external networks an MS can communicate. This is explained further in the next section, “IP Addresses”.
An alternate form of service is PPP service, where instead of
transporting IP datagrams, the network transports PPP frames between the MS and GGSN. The purpose of the PPP service is to either allow the customer to manage their IP addresses, or to allow the customer to use other networking protocols such as Novell IPX or AppleTalk.
The GGSN can terminate the PPP connection, or can extend it using tunneling protocols such as Layer 2 Tunneling Protocol (L2TP) to external networks, including customer networks. In such a case the PPP connection would terminate in a customer network. Using L2TP, the GGSN is the L2TP Access Concentrator (LAC) and the customer premise equipment is the L2TP network server (LNS). The LNS is likely to be supplied by AWS. See Figure 4.
GSM RF MAC
LLC SNDCP
GSM RF
MAC Frame Relay Frame Relay
LLC TCP/UDP IP Layer 2 TCP/UDP IP Layer 2 Mobile Station Base Station Subsystem Serving GPRS Support Node Gateway GPRS Support Node
PPP: Point to Point Protocol SNDCP: Subnetwork Dependent Convergence Protocol LLC: Logical Link Control RLC: Radio Link Control
MAC: Medium Access Control GSM RF: GSM Radio Frequency Layer
BSSGP: Base Station Subsystem GPRS Protocol GTP: GPRS Tunnel Protocol
L2TP: Layer 2 Tunneling Protocol RLC RLC Relay BSSGP BSSGP Layer 1 Layer 1 Layer 1 Layer 1 SNDCP Relay GTP GTP
Encrypted Communications L2TP
IP Layer 2 Layer 1 PPP Relay PPP
Figure 4: PPP Service with L2TP Connection to Customer Site
If using IP protocols in conjunction with the PPP service, the customer network is responsible for assigning an IP address to the MS as part of establishing the PPP link. The customer also has the option of
authenticating the user using the Challenge Authentication Protocol (CHAP) or Password Authentication Protocol (PAP), as both authentication protocols are options with PPP.
The PPP service is relatively secure as it limits user data
communications to the exchange of PPP frames with the customer network. Any communications between the MS and the Internet has to be via the customer’s network. In addition, the L2TP protocol itself has security features, including data encryption.
As for specifying the type of service (IP vs. PPP), a customer must first order the appropriate service. For establishing connections, the Access Point Name used (APN) determines the type of service. When an MS requests data service (by establishing a packet data protocol context), it specifies the APN it wishes to use.
4.2. IP Addresses
The following discussion applies to IP service, and not the PPP service discussed in the prior section. AWS offers three types of IP addresses: public, private and customer supplied. Public means that the network assigns the MS a temporary IP address from a pool of public IP addresses owned by AWS. These addresses remain the same for user IP datagrams both inside and outside the AWS GPRS service. In contrast, with a private IP address (as defined by Internet RFC 1918), the AWS network assigns the MS a temporary private IP address that it translates to a public IP address at a server residing between the GGSN and the external network.
There are two types of proxy servers and two address translation servers used in the GPRS network. One proxy server is the WAP gateway which is used to support WAP browsers, primary in handsets. Another proxy function is performed by the Optimization Server which provides proxy services as part of it compression function for web traffic and a variety of other common Internet based applications like FTP.
A Network Address Translation (NAT) Server provides private to public address translation and a few other services. NAT services support many common VPN tunnels and nearly all common Internet services. A Network Address and Port Translation (NAPT) server, which is optionally paired with the Optimization Server, is used to provide highly efficient address utilization for a sub-set of common Internet services and applications (primarily HTTP). With NAPT, multiple mobile stations share the same public IP address. What differentiates the mobile stations is their port numbers. Contact AT&T Wireless Services Customer Care at 1-866-293-4634 for the currently
supported applications. Internet RFC 3022 describes NAPT functionality.
Public addresses may be better suited for some applications such as certain virtual private networking software (e.g. IPSec) that embed the client IP address in the data payload.
The GPRS specification allows for both fixed and dynamic IP addresses. However, the American Registry for Internet Numbers (ARIN) which is the IPv4 address assignment authority, no longer allows static IP addresses for wireless data services. AWS currently only offers dynamically assigned IP addresses. This means customers cannot employ firewalls that filters incoming traffic based on the static IP address of the MS unless using customer-supplied addresses
(discussed at the end of this section.)
If the customer is using a public IP address, the customer’s MS is more vulnerable to attack from the Internet. For this reason, customers should disable any services (e.g. file sharing) on the MS and should consider personal firewall software. Note however that if a customer has obtained a fixed-end connection (either Frame Relay or Managed Internet option) from AWS, a service option is to disable routing of traffic between the MS and the Internet. This does not prevent communication to the Internet via the customer network, but such communication is then under the customer’s control. This security option is also available for private IP addresses.
For private addresses, AWS uses the 10.0.0.0 network.
If the customer is using a private IP address, the customer’s MS is less vulnerable to attack from the Internet. The NAPT Server scans
incoming data addressed to an MS and only allows the traffic when the source address and port (UDP or TCP) number matched previously sent outgoing data. This means any communication must be initiated by the MS. The network only allows IP traffic associated with specific applications, determined by the port numbers used. A similar process occurs with the proxy servers (WAP and Optimization Server).
The net result is that it is more difficult, but not impossible, for
attackers to target an MS since their traffic is more likely to be blocked than with a public IP address. Nevertheless, customers are still advised to disable services such as file sharing on the MS and to consider personal firewall software. Also, WAP, NAT or NAPT servers do not protect against unauthorized traffic when an MS has previously been compromised and has unauthorized (e.g. virus or worm) software resident.
With customer-supplied addresses, AWS uses a block of IP addresses from the customer for assignment to the customer’s mobile stations. These requires prior arrangement with AWS, and these must be valid public IP addresses.. AWS does not advertise these addresses to the Internet. This approach requires that the customer connect their network to the AWS GPRS service using either a frame-relay or managed Internet connection. The benefit of this approach is that customers can filter incoming traffic from MS based on their IP address.
5. Internal Network Interfaces
This section briefly examines the interfaces of the AWS GPRS service and their security functions. These include the portions controlled by AWS and the interface to other GPRS service providers.
5.1. AWS GPRS Network
AWS makes security a high priority, and employs various mechanisms beyond those specified in the GPRS specifications to protect customer data, customer networks, customer mobile stations and its own
network.
As discussed in the prior section, “Mobile Station to Network Interface”, GPRS technology provides for authentication and encryption between the MS and SGSN. See Figure 1 and Figure 2. Since the SGSN is geographically centralized to cover regional service
areas, user data is protected over these large areas. Private circuits are used to connect base station controllers to the SGSN.
Communication between the SGSN and GGSN occurs over an IP network. User data is tunneled between these nodes using the GPRS Tunneling Protocol. See Figure 3. GTP does not provide any security mechanisms. Instead, some security is provided by the underling IP network being a private network.
Other nodes such as the HLR which contains subscriber information are protected by only being accessible through SS7 signaling networks which are not publicly accessible.
AWS also maintains firewalls that restrict unauthorized traffic in its connections to other networks, such as customer networks, the Internet, and other carriers. Any customer traffic directed at GPRS network elements is discarded.
Although the network employs various means of protecting against unauthorized traffic and eavesdropping, customers with sensitive applications should employ security measures of their own.
5.2. Intercarrier Interface
Inter-service provider (i.e., Intercarrier) security is of concern when an MS travels to a different carrier's GPRS network and attempts to access the AWS GPRS service. What are the security implications of an MS operating in this fashion and of the wide-area connection between carriers? First, GPRS carriers must have roaming agreements in place for data service. Second, GPRS carriers must have their networks interconnected, either through direct links or via an interconnecting network sometimes referred to as a GPRS Roaming Exchange (GRX). See Figure 2. The node that interfaces to the GRX or other carriers is called the Border Gateway, whose principal function is to block unauthorized traffic. The type of traffic that is allowed includes user data communications (carried by the GTP Tunnel Protocol), domain name service queries, routing protocols (e.g. Border Gateway Protocol) and signaling protocols. However,
customers should not make any security assumptions about the privacy of their data when intercarrier connections are involved as multiple entities are involved, and this portion of the network is likely to change over time.
When an MS is operating in a visited carrier’s GPRS network, the SGSN in the visited carrier’s network serving area authenticates the MS using the same mechanisms as discussed in the section, “Mobile Station to Network Interface”. The difference is that the visited
carrier’s HLR does not contain the subscription information, and so the SGSN obtains this information from the HLR in the subscriber’s home network. This process is similar to when a voice subscriber roams into a different carrier’s network.. Once authenticated, communications is encrypted between the MS and the SGSN as previously discussed. In the situation where an AWS GPRS service customer is operating in another carrier’s area, the PDP context that is activated is between the MS and the home network GGSN. In other words, the customer uses their existing access point names (APNs). The result is that the IP address allocated to the customer will be from the same pool as if they were in their home carrier’s network. All data to and from the MS will be routed via the home network GGSN, and any security provisions (e.g. whether or not data can be routed to/from the Internet) will apply. In addition, all of the customer’s services (e.g. NAPT, NAT,
Optimization Server, WAP Gateway, Portal) will remain accessible. The advantage of this approach is that a user has a consistent
experience with the same security provisions regardless of where they obtain GPRS service.
In the future, it might be possible to access other APNs (such as direct Internet service via the visited carrier). This may have implications on security that customers will need to consider.
Customers should also be aware that to obtain GPRS service from a carrier in a different area (e.g. overseas), they can obtain service directly from that carrier. This will involve getting a SIM card from that carrier for their equipment. Once using that SIM card, all security functions will be handled by that carrier and their subscription to the A&T Mobile Internet Service (along with any of their security provisions and fixed-end connections) will not be in effect.
6. External Network Interface
This section describes the security aspects of the interface between the AWS GPRS service and external data networks. It is through the external network interface that customers connect their networks to the AWS GPRS service. The three principal types of connections include frame relay connections, managed Internet connections and normal Internet connections. See Figure 2 and Figure 5. The difference
between the two types of Internet connections is that with the managed Internet connection, AWS provides a virtual private network service to secure communications between the AWS GPRS service and the customer network. This service is called the Wireless Connectivity Option Managed Internet Service (WCO Managed Internet Service). With normal Internet connections, user data is routed across the Internet and any additional security is the customer’s responsibility.
AT&T GPRS
Network Internet
AT&T Frame Relay Network
Customer C Network Customer A
Network
VPN Tunnel Customer B Network
Figure 5: Different types of External Network Connections
Frame relay connections can be obtained directly from AT&T Wireless Services or from other frame-relay service providers. The AT&T service is called Wireless Connectivity Option Frame Relay (WCO Frame Relay). The following sections discuss the security aspects of the three types of connections, including a general discussion of VPN technology. First we briefly discuss naming and routing.
6.1. Naming (APNs) and Routing
Within a GPRS network, an external network with which the MS can communicate is referred to by an Access Point Name (APN). When establishing a data session (Packet Data Protocol context), the MS specifies an APN. The APNs available to an MS are part of the
subscription profile. The APN also determines certain routing options. One option, if the customer is using either a frame relay connection or WCO Managed Internet connection, is whether or not the MS can communicate with the Internet. If Internet communication is not allowed, then packets addressed from the Internet addressed to the MS or sent to the Internet from the MS are discarded at the GGSN. The only exception are packets associated with the managed Internet connection itself (a VPN tunnel). A customer specifies this security option at the time they order service.
Customers should also be aware that any MS operating in the AWS GPRS network can send IP packets to any customer site connected via frame relay or a managed Internet connection. Finally, routing rules in the AWS GPRS service prevent an MS from communicating with another MS.
6.2. Frame Relay Connections
Frame relay connections are considered the most secure external network connection as they employ links (called permanent virtual circuits or PVCs) that are relatively private.
The AWS GPRS service connects to a variety of external networks, including those operated by frame relay network providers, as shown in Figure 5. Frame relay is a packet-oriented communication method used to connect computer systems. The frame relay network is often called a fast-packet switching network. Tasks such as error checking, packet sequencing, and packet acknowledgment are handled by the end systems involved in transmission rather than by the network itself. This allows the frame relay network to operate at much higher speeds than older packet-switched networks such as X.25.
Frame relay provides an increased level of security when compared to the public Internet. Frame relay PVCs are almost like leased lines
between the customer’s premises and AWS. Frame relay networks are operated by service providers in such a way that there is neither any open access to individual PVCs, nor is there access between one PVC and another even if they share the same physical circuit.
Firewalls in the AWS GPRS service prevent data communications between the Internet and any customer frame-relay PVC. Firewalls and physically separate networks also prevent any MS or customer’s frame relay connection from reaching GPRS infrastructure equipment. Customers can obtain frame-relay connections from a variety of
providers, including AT&T Wireless. The AT&T Wireless frame-relay service is called AT&T Wireless Connectivity Option - Frame Relay and is discussed in more detail in the next section.
6.3. AT&T Wireless Connectivity Option - Frame Relay
Customers can purchase frame relay service from AWS for their fixed-end connection. There are many advantages to obtaining service from AWS, including a single service provider for both wireless and fixed-end connections, faster time to provision, faster time to resolve any problems and a highly dependable network.
A frame-relay connection requires a private line from a customer’s router to the AT&T Frame Relay Network. A local exchange carrier usually provides this line. See Figure 6.
F R S w itc h
F R S w itc h P V C
A T & T F r a m e R e l a y N e t w o r k C u s to m e r F r a m e
R e la y P o r t D L C I
A W S F r a m e R e la y T 1 P o r t D L C I = 1 0 0
R o u te r
L A N
A T & T P r iv a t e L i n e ( L E C P r o v id e d )
1 . N e t w o r k A c c e s s :
A d ig it a l “ lo c a l lo o p ” L E C c o n n e c t i o n t o t h e A T & T F r a m e R e l a y s w it c h . E it h e r a 5 6 k b p s o r T 1 c o n n e c t io n
2 . P o r t :
A p h y s ic a l c o n n e c t io n to a s w itc h in th e A T & T F r a m e R e la y n e t w o r k . F u lly s u b s c r ib e d s p e e d s o f 5 6 k b p s t o 1 . 5 4 4 M b p s
3 . P V C :
A lo g i c a l c o n n e c t i o n
b e tw e e n p o r t s w it h a g u a r a n t e e d m in im u m p e r f o r m a n c e , o r C I R
N e t w o r k A c c e s s
C S U /D S U
R o u te r
A W S M D - I S
C S U /D S U
B o t h e ll W A A N D /O R A l le n T X W i r e le s s C u s t o m e r C o n n e c t iv i t y
D e m a r c a t io n P o in t
Figure 6: WCO Frame Relay Connection
6.4. Internet Interface
The AWS GPRS service has a routed connection to the Internet, as shown Figure 2. One can think of the GPRS network as a wireless extension of the Internet. As such, the AWS GPRS service can route traffic between a MS and an Internet host. An Internet host can be any Internet reachable system, whether Internet Web server, File Transfer Protocol (FTP) site, or private corporate system.
6.5. Virtual Private Network (VPN) Discussion
A virtual private network is a method to ensure private transmissions over public networks. A VPN establishes a secure tunnel between its endpoints. Each endpoint authenticates the other endpoint, forwards traffic to authorized services, and encrypts and decrypts
communications. A VPN typically encrypts the IP packet (or other network layer protocol), adds a special header and encapsulates all this information in a new IP packet. There are a number of “off-the-shelf” solutions that allow an organization to implement a VPN. A VPN approach is particularly effective when connecting to a fixed-end system via the Internet. With a frame relay fixed-end connection, there is less need to employ VPN technology.
In looking at VPN technology, realize that there are two typical scenarios in which a VPN is used, as shown in Figure 7. In one scenario an organization links two separate networks over the Internet (e.g. remote office to central office) or links its network to a strategic customer’s or partner's network. This is commonly called a “server-to-server” or “network-to-network” approach. The VPN software which makes this possible needs to be installed at both locations, either as part of the firewall, part of the router, or behind the firewall, in a separate security server.
Internet
Server-to-server private communications
Client-to-server private communications
Figure 7: Examples of two types of virtual private networks
The other scenario is for remote workers who want to access their organization’s network using their mobile computer. Here the VPN software still resides at the organization's point of connection to the Internet as in the case of a server-to-server VPN. What is different is that a mobile computer runs client software that implements the VPN protocols. This is a client-to-server VPN or remote access VPN. The distinction between a server-to-server VPN and remote access is important because some VPN products emphasize server-to-server communications while other VPN products emphasize remote access.
Many major firewall products now provide VPN support. In addition, a variety of other companies now have VPN offerings. Not only are companies offering VPNs, but also the standards underlying VPNs are beginning to mature, (e.g. IPSec, Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP) and SOCKS). Some VPN products today are implemented in separate servers behind the router but once standards are finalized, expect to see VPN capabilities as yet another router or firewall feature.
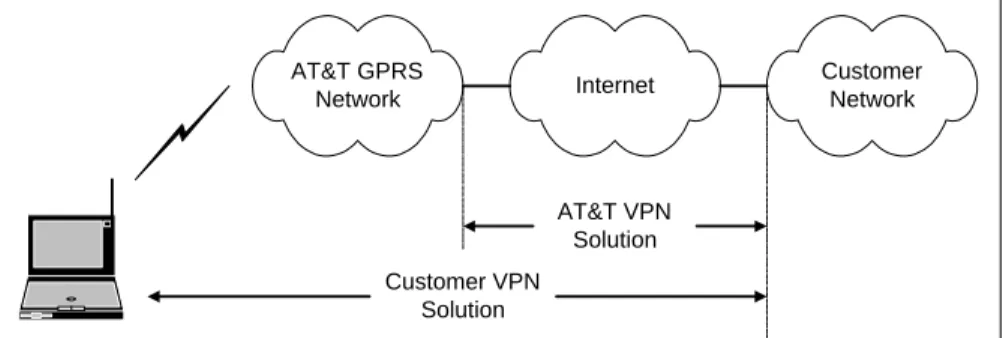
There are two fundamental ways of applying VPN technology to the AWS GPRS service. One way is to use a VPN service from AWS called Wireless Connectivity Option Managed Internet Service. The other way is to independently implement a VPN solution. These two approaches are shown in Figure 8.
Internet Customer Network AT&T GPRS
Network
Customer VPN Solution
AT&T VPN Solution
Figure 8: AT&T VPN solution vs. customer VPN solution
Implementing a customer-installed VPN solution provides security all the way from the MS to the F-ES, including authentication, encryption and data integrity, and it provides complete control of the connection. But additional system development is required and there is
communications overhead via the wireless connection. In contrast, using the AWS VPN solution provides a secure tunnel through the Internet between the AWS GPRS service and an organization’s network with much less system development. In the future, AWS may also offer a client VPN solution to customers.
A discussion of each approach is presented in the following two sections.
6.6. Managed Internet Connection
AWS provides a service called the Wireless Connectivity Option Managed Internet Connection. This connection is for communications between the customer MS and their fixed-end systems across the Internet, secured using virtual private networking technology. There are two scenarios. In one, the customer provides their own Internet connection. In the other, AWS provides the Internet connection using a digital subscriber line (DSL).
In both scenarios, AWS installs a VPN Server at the customer location which is preloaded with a shared key. An identical shared key is preloaded on a VPN server within the AWS GPRS service.
Authentication of the shared key by both the customer VPN server and the AWS VPN server allow for a secure tunnel to be created between the two servers, based on the IPSec family of protocols. The triple DES (Triple Data Encryption Standard) algorithm encrypts the data. DES is classified as a 56-bit encryption algorithm. 3DES adds even more security to the DES algorithm by performing the encryption function three times with different subkeys. Figure 9.
I n t e r n e t
C u s t o m e r S i t e
R o u te r
L A N
2 . M a n a g e d IP S e c T u n n e l
A s e c u r e tu n n e l b e tw e e n c u s to m e r s ite r o u te r a n d A W S r o u te r in A lle n T e x a s
C S U /D S U
R o u t e r C S U / D S U
G P R S N a t i o n a l D a t a C e n t e r
W i r e le s s C u s t o m e r C o n n e c t i v i t y
V P N S e rv e r B a c k U p V P N S e rv e r
V P N S e r v e r
A l l e n T e x a s
M a n a g e d I P S e c T u n n e l
1 . V P N S e r v e r
A h a r d w a r e V P N s e r v e r s p e c ific a lly d e s ig n e d fo r a n IP S e c T u n n e l. A n u n iq u e s h a re d k e y w ill b e p r e lo a d e d w h ic h w ill e s ta b lis h a n e n c r y p te d tu n n e l w ith th e A W S n e tw o r k
Figure 9: Managed Internet connection provided by AWS
A WCO Managed Internet connection can also serve as a redundant connection to the WCO Frame Relay connection. The customer’s router will be configured to automatically fail-over to the redundant
connection should the primary frame-relay connection fail, and to switch back to the primary connection when the frame-relay connection is restored.
6.7. Client VPN Solution
The most secure architecture is one that spans from the user to their network, since this will provide the greatest number of options for authentication, authorization, data integrity, and encryption. It also ensures secure communication all the way from the MS to the fixed-end system. This is possible by implementing a VPN solution that includes VPN-client software on the mobile computer and VPN-server software on a security gateway, which may be part of or separate from existing firewalls or routers. See Figure 10. With this approach, a customer is not dependent on any security mechanisms within the AWS GPRS service. This approach allows a customer to use the Internet for secure fixed-end connections.
Wireless IP, Internet, company firewall
Secure tunnel or channel
Corporate network Security gateway
Host or Server Security
client
Figure 10: Secure tunnels or channels for end-to-end security
For this approach to work, it may be necessary to configure existing firewalls to pass VPN traffic. Customers should realize that this approach does add overhead to communications, which can reduce throughput. With this approach, data over the radio interface is encrypted both by the VPN and again by the GPRS network, which some customers may find desirable, and others may find redundant. This approach also requires that customers administer the VPN client software on the mobile station.
A customer-implemented VPN is worth considering especially if an organization is already using a particular VPN product to support remote employees. In such a case, the same VPN product may be an option for AWS Mobile Internet users. In the future, AWS itself may provide specialized support for particular client VPNs. Contact AWS for current information.
7. GSM/GPRS Mobile Internet Phone
The Wireless Application Protocol (WAP) is an industry standard developed by the Wireless Application Protocol Forum
(http://www.wapform.com), with the objective of bringing Internet content and data services to digital wireless terminals such as mobile telephones. GSM/GPRS Mobile Internet phones from AWS include WAP microbrowsers that allow customers to interact with Internet content, or to access applications and data on their private intranets. This AWS service is currently based on version 1.2 of the WAP standard. This service is similar to the prior AWS PocketNet service which used CDPD wireless technology and communications protocols developed by OpenWave.
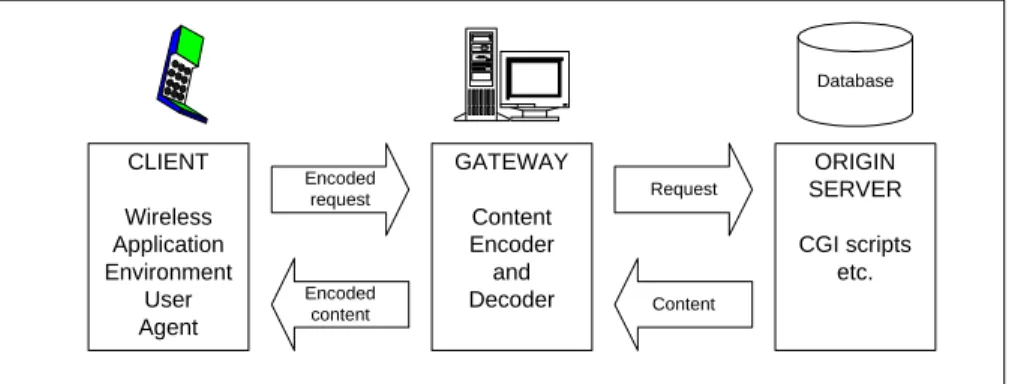
Because the GPRS WAP phones transmit information via the GPRS network, security native to GPRS technology protects users, including authentication of the GPRS phone and encryption of the radio link. WAP consists of a set of protocols between the client and a gateway, and a separate set of protocols between the gateway and what is called the origin server, as shown in Figure 11. The gateway is owned and operated by AWS. The communication between the WAP client and the gateway is optimized for the wireless medium while
communication between the gateway and the origin server is based on standard Internet protocols.
CLIENT Wireless Application Environment
User Agent
GATEWAY Content Encoder and Decoder
ORIGIN SERVER CGI scripts
etc. Encoded
request
Database
Content Request
Encoded content
Figure 11: WAP architecture
WAP provides a flexible security infrastructure. The key element of WAP security is a security protocol called Wireless Transport Layer Security (WTLS), which operates between the WAP client and the WAP gateway. WTLS is based on the industry-standard Transport Layer Security protocol, which is the Internet Engineering Task Force (IETF) adaptation of Secure Sockets Layer (SSL), a security protocol developed by Netscape to secure communications between web browsers and web servers. See “Appendix A: Data Security Technologies” for more details about SSL.
WTLS, which operates above the transport protocol layer, is optimized for wireless connections. It offers the following features: data integrity, privacy through encryption, and mutual authentication between the terminal and origin server. WTLS also offers protection against denial-of-service attacks. See Figure 12.
GPRS
Network Internet
WAP Gateway
Secure connection using WTLS
Origin (Application) Server
Secure connection using SSL
Figure 12: WAP Security Architecture
WTLS supports public key certificates for authentication. Encryption algorithms include RC5 with 40, 56 or 128 bit keys, DES with 40 and 56 bit keys, triple DES, and IDEA with 50, 56 and 128 bit keys. To ensure messages have not been tampered with, WTLS supports message integrity algorithms such as SHA and MD5.
Between the gateway and origin server, SSL can be used to secure communications. The gateway acts as a proxy on behalf of the WAP phone, relaying messages to and from the phone. SSL includes both authentication and encryption mechanisms. Encryption methods over SSL include DES, Triple-DES and RC4. SSL version 3 and TLS provides support for authentication of both client (which is the WAP gateway in the case of WAP applications) and the server using public keys and X.509 digital certificates.
At the gateway, data is decrypted from WTLS and re-encrypted using SSL. AWS protects this portion of the communications at the gateway with physical security. In addition, firewalls limit access to the WAP gateway. The net result is a secure connection all the way from the WAP phone to the Web server, as shown in Figure 13. Customers can also install a WAP gateway within their own network, though this requires additional arrangements.
Radio Interface IP WDP WTLS WSP WAE
Mobile Station WAP Gateway
Layer 1, 2 IP WDP WTLS
Layer 1, 2 IP TCP SSL/TLS
Origin Server
Layer 1, 2 IP TCP SSL/TLS HTTP GPRS Network
HTTP: Hypertext Transport Protocol SSL: Secure Sockets Layer TLS: Transport Layer Security
WAE: Wireless Application Environment
WTP WTP
WAE
WSP Relay
HTTP
WDP: Wireless Datagram Protocol WSP: Wireless Session Protocol
WTLS: Wireless Transport Layer Security WTP: Wireless Transport Protocol
Figure 13: WAP Protocols
Additional security may be required, depending upon the type of data a customer transmits with a WAP-capable phone. For example, if the transmission contains sensitive financial information, a dedicated, frame relay link to the AWS GPRS service might be appropriate. The customer firewall needs to be configured so the WAP gateway can communicate with the web server hosting the WAP application, which will typically resides behind the corporate firewall or in a demilitarized zone.
8. Enhanced Data Rates for GSM Evolution (EDGE)
EDGE is a new radio technology that will significantly enhance the data throughputs of GPRS networks. It consists both of a new modulation method and new ways of encoding data at the physical layer to maximize performance. It also includes a method of
dynamically adapting the modulation and encoding to respond to radio conditions that may vary moment by moment due to interference and
varying signal strength. The net result is peak raw throughputs in excess of 384 Kbps and average user throughputs of 80 Kbps.
From a security standpoint, EDGE networks will employ all the same mechanisms of GPRS networks. EDGE is a physical layer technology only, and since security methods are implemented at higher protocol layers, the security of an EDGE network will be identical to a GPRS network. Customers can architect their security solutions today using GPRS, and easily migrate to EDGE in the future.
Appendix A: Data-Security
Technologies and Standards
This section provides a brief overview of some of the security
technologies, protocols and standards in use today that are relevant to wireless-data networks.
A3, A5, A8 Algorithms
These algorithms are specific to GSM and GPRS networks, and their functions are described above in the section “Mobile Station to Network Interface”. A3 is used to authenticate a mobile station, A8 to derive an encryption key, and A5 to encrypt communications. Details of these algorithms is deliberately restricted.
Authentication
Authentication is a process to confirm the identity of an entity. It often entails a private key (secret number) and calculations performed against this value. With a private key system, both parties would share the same private key. With public key systems, there are both private and public keys.
A digital signature can be encrypted in a message to provide
authentication of the sender's identity. For example, with public key cryptography, Alice signs a message by doing a computation that involves both her private key and the message itself. The output of this computation, the digital signature, is attached to the message. To verify the signature, Bob does another computation that involves the message, the purported signature, and Alice's public key. If the results properly hold up in a simple mathematical relationship, the signature is verified as authentic; otherwise, the signature may be fraudulent or the
message may be altered, and they are discarded. Messages can also be authenticated using a session key that was created from a shared secret key.
Certificates
Certificates are digital documents that associate an individual or other entity with a public key. This allows other parties to verify with a high degree of confidence that the individual or entity is who they claim to be. This can be important when providing access to particular
computing resources or information, or for e-commerce transactions. The most commonly used format for certificates is defined by the International Telecommunications Union (ITU) X.509 standard. Certificates are validated at the time they are used by sending messages to trusted certificate authorities. Certificate authorities are either private or public systems, and must be able to authenticate themselves before their responses can be trusted.
The AWS GPRS service does not use certificates, but since it is an IP network, digital certificates can be readily employed over the network for purposes of authenticating both mobile users as well as fixed-end services.
DES and AES
DES is the Data Encryption Standard, an encryption block cipher defined and endorsed by the U.S. government in 1977 as an official standard. Since then, DES has become the most well known and widely used encryption system in the world.
DES is a secret-key system; when used for communication, both the sender and receiver must know the same secret key. This secret-key is used to both encrypt and decrypt the message. DES is designed to be implemented in system hardware, is relatively fast, and works well for bulk encryption of large amounts of data. DES and Triple-DES are two cryptographic methods available for SSL.
DES uses a 56-bit key. This size key is suitable for much of business communications, but is becoming vulnerable. Triple-DES is a method that improves the strength of DES. Triple-DES can be implemented in several different ways, one way is to encrypt the data three times using three different keys. The U.S. government is now using Triple-DES. The National Institute of Standards (NIST) is in the process of establishing an encryption standard called Advanced Encryption Standard (AES) to replace DES . AES will be more secure than DES, and is intended to be the U.S. encryption standard for the next several decades.
Diffie-Hellman Key Exchange
The Diffie-Hellman key agreement protocol allows two users to exchange a secret key over an insecure medium without requiring either user to know a prior secret-key. It is different than public-key cryptography. This method is used within CDPD networks between the mobile-end system and the mobile-data intermediate system to create a session key that is used for encrypting data communications. This method is not used in GPRS networks.
Encryption and Key Management
Encryption is the first step in the process of cryptography and involves transformation of data into a form that is unreadable by anyone
without a secret decryption key. Its purpose is to ensure privacy by keeping the information hidden from anyone for whom it is not intended, even those who can actually see or capture the encrypted data.
In a multi-user environment, encryption allows secure communications over an insecure channel. In a simple example, Alice wishes to send a message for Bob's eyes only. To keep the message secure, Alice encrypts the message (called plaintext) with an encryption key, and the encrypted message (called ciphertext) is sent to Bob. Bob, who knows the secret key, decrypts the ciphertext and reads the message. An
eavesdropper may either try to obtain the secret key or to recover the plaintext without using the key. Traditional cryptography is based on the sender and receiver of a message knowing and using the same secret key. The main problem with this method is getting the secret key to both the sender and receiver without diversion to an intruder. GSM/GPRS, which use a shared secret key approach, solves this problem by the distribution of secret keys in the subscriber identity module. The session key is calculated from this secret key.
In 1975, public-key cryptography was invented by Whitfield Diffie and Martin Hellman to solve the key management problem. This method of encryption uses the concept of a pair of keys, one public and one private key. The public key is made public by distributing it
widely; the private key is never distributed and is always kept secret. The need for each person to share secret information is eliminated; all communications involve only public keys, and no private key is ever transmitted or shared. Now, when Alice wants to send a private
message to Bob, she looks up Bob's public key in a directory, uses it to encrypt the message, and sends it off. Bob then uses his private key to decrypt the message and read it. No one can decrypt the message without Bob’s private key, thus eliminating the requirement for complex key management schemes with private key systems. However, public-key cryptography does require a public-key infrastructure (PKI) so that users can securely and reliably obtain public key information. Such infrastructure is not yet broadly available.
Firewalls
A firewall is a system or a group of systems that enforces an access control policy between multiple interconnected networks. A firewall protects the network from unauthorized access while its connected to other networks. This is especially true for public networks, such as the Internet. All traffic in and out of the network goes through the firewall. Only the authorized traffic defined by the security policy can pass. The firewall itself must be highly resistant to penetration.
The importance of a firewall becomes apparent when one considers that the AWS GPRS service can connect to many other networks, including other GPRS networks, customer networks, value-added