Implementing IT Security Penetration Testing in Higher Education Institute
Full text
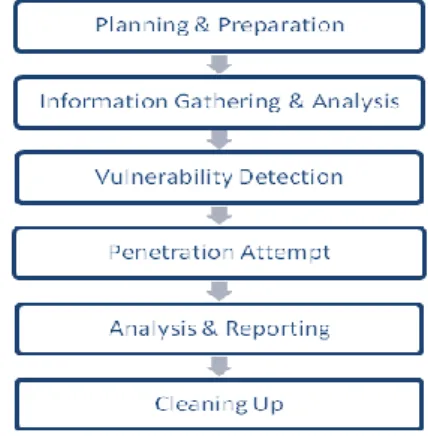
Figure

Related documents
The paper assessed the challenges facing the successful operations of Public Procurement Act 2007 and the result showed that the size and complexity of public procurement,
ings were observed in the renal tissue of the Cis group with significantly increased levels of oxidants and IL-1β, such as wide hemorrhage areas, dilated and congested blood
19% serve a county. Fourteen per cent of the centers provide service for adjoining states in addition to the states in which they are located; usually these adjoining states have
To the finest of our information, this is the first report of the use of PEG-400 and DMAP, DIPEA catalyst for the protection of secondary amine of pyrazole nucleus using Boc..
As reference material, the VTEC values derived from the IRI-2012 model (Bilitza et al. 2014), F10.7 solar flux index and sunspot number as ex- tracted from NASA/GSFC’s OMNI data
To determine whether serum resistance conferred by LOS sialyla- tion in vivo is compromised by decreased lst expression, we as- sessed the ability of P lst-Ng and P lst-Nm to
Our immediate needs for continuation and expansion of the Mobility Assessment Tool dictated support for both desktop computers (running either Windows or Mac OS X) and Apple
Considering only women who received abortion care from public facility where there is shortage contraception supplies in study conducted in two of the region and failing to