Stonesoft 5.5. Firewall/VPN Reference Guide. Firewall Virtual Private Networks
Full text
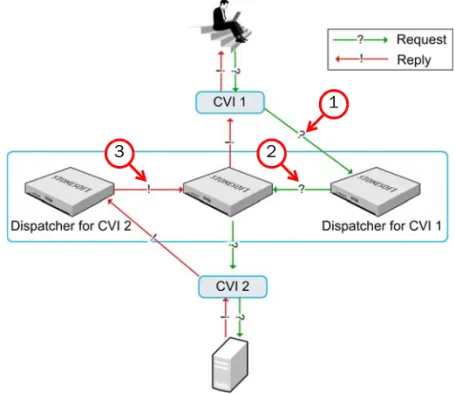
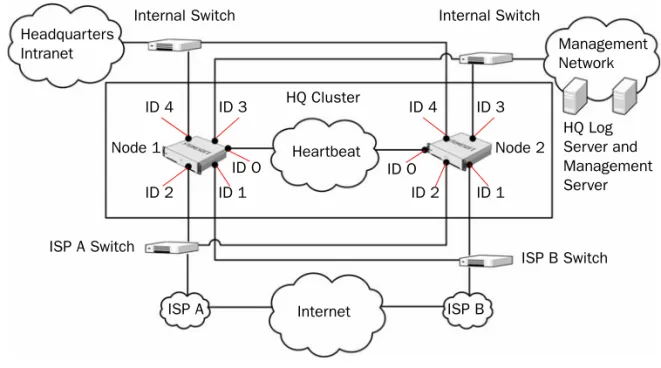
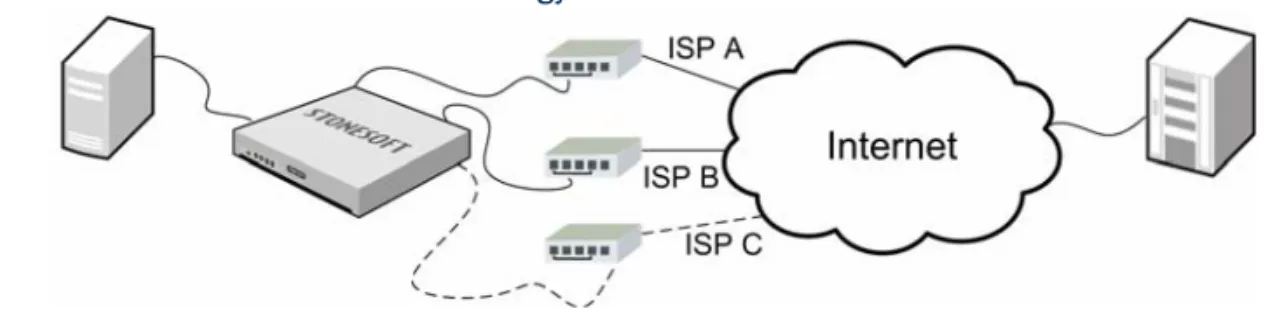
Figure



Related documents
During the thesis work, I measured six different parameters: the number of emergency processes, hash table entry number, caching replacement policy, cache entry
Parr and Shanks [18] classify ERP implementations to three broad categories (comprehensive, middle road, and vanilla) and according to them ERP implementations differ with respect
However, despite the increasing use of English and translations in Spanish-language newspapers – particularly from the Transition Period on – the dominant language of publication
Als we de voorgaande hoofdstukken goed hebben bestudeerd en door veel oefenen de nodige vaardigheid hebben gekregen, moeten we nu in staat zijn, een vakkundige tekening te maken.
In just 9 months of part-time classes at Shillington, I was able to conceptualise and design my very first cookbook which was published by Random House in 2014.” SNEH ROY IS A
Electron micrographs of mannonamide aggregates from water (a-e) or xylene (f): (a and b) details of aged fiber aggregates of D-mannonamide 2 negatively stained
If for any reason the Artist is unable to take possession of sold Works and arrange transportation to the non-local buyer, the Artist and Buyer may make arrangements with OSA
• Our goal is to make Pittsburgh Public Schools First Choice by offering a portfolio of quality school options that promote high student achievement in the most equitable and