Mathematical Simulation of Self-Similar Network Traffic with Aimed Parameters
Full text
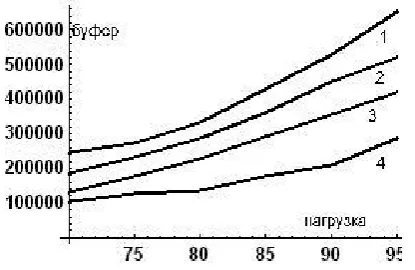
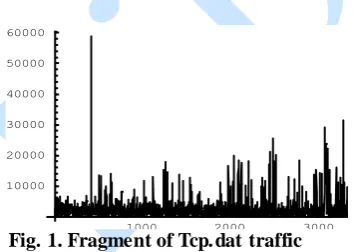
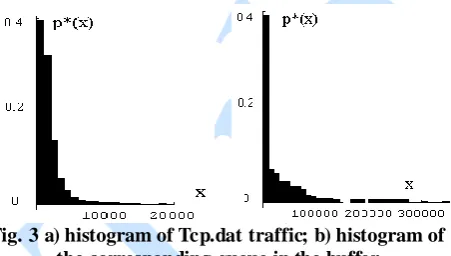
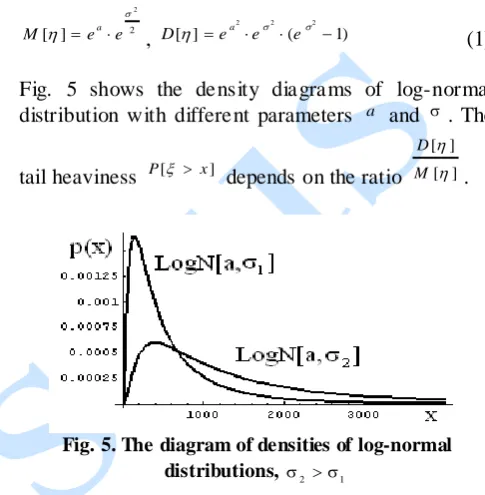
Figure

Related documents
National Conference on Technical Vocational Education, Training and Skills Development: A Roadmap for Empowerment (Dec. 2008): Ministry of Human Resource Development, Department
As can be seen in Table 2, the intervention group showed superior functioning at post-treatment on measures of seven cognitive domains: general cognitive functioning
The National Food Security Act, 2013 lays down the legal entitlement of every school child up to the age of fourteen years to a free, cooked, hot midday
Using text mining of first-opinion electronic medical records from seven veterinary practices around the UK, Kaplan-Meier and Cox proportional hazard modelling, we were able to
• Follow up with your employer each reporting period to ensure your hours are reported on a regular basis?. • Discuss your progress with
The work presented here supports the prevailing view that both CD and IOVD share common cortical loci, although they draw on different sources of visual information, and that
As we have defined, anti-surveillance is described as the actions or manoeuvres that a person carries out in order to get a reaction, and therefore confirm that
1) Thawley SE, Sessions DG, Deddins AE. Surgical therapy of supraglottic tumors. In : Thawley SE, Panje WR, Batsakis JG, Lin- dberg RD, editors. Comprehensive management of head