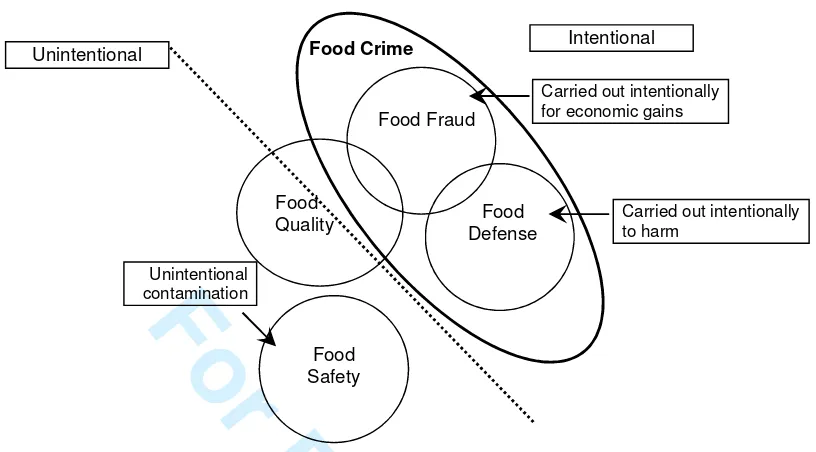
Food fraud: policy and food chain
Full text
Figure




Related documents
When applied to airfoil ice accretion shapes, the properties of the codebook vectors and the statistical nature of the SOM methods allows for a quantitative comparison
Using output from Algorithm ENUM, we also investigated the effect of varying instance sizes, for six different types of optimal stable matchings (balanced, sex-equal,
Distribution: England, Ireland, Isle of Man Notes: added by Buhl and O'Connor (2008). Platygaster (Platygaster) sterope
• Does individual hospital’s quality of care improve in relation to new treatment goals. • Does individual hospital’s quality of care
In view of the methodologically-driven and discourse-analytical aim of this article, I will restrict myself to the fields of spatial sciences, eco-semiotics and urban
Performance and emission characteristics like brake thermal efficiency, brake torque, brake specific fuel consumption, NO x , particulate matters, CO 2 , smoke emissions have
387 A similar thing happens to the Visigoths – as such, they come up when the Hunnic power shift takes place, and Jordanes narrates their exploits in the Roman Empire up to the
This paper presents piloted flight test results of a sliding mode fault tolerant control scheme implemented on the Japan Aerospace Exploration Agency’s MuPAL- α research