Secure Communication Based On Authentication Techniques Using NIDS
Full text
Figure

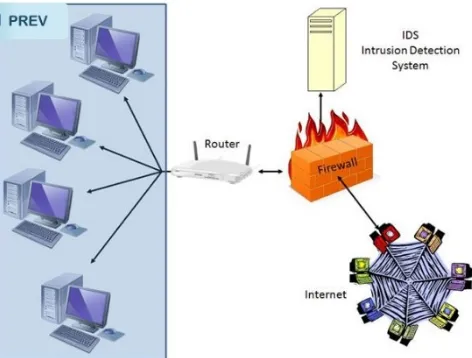
Related documents
A su vuelta de Valladolid, Egidio, el 6 de junio de 1555, pocos meses antes de fallecer envió desde Sevilla una carta al rector en la que traslucía que
There is need for a transformative program of research focused on graduate education that is based on theoretically-grounded models of transdisciplinary teaching and learning,
Development quarterly wage file to determine if there is an employer. If an employer exists, then the collection is staged to Pending Wage Attachment. If the debtor does not offer
The results show that the cement slurry has steady performance for high temperature, adjustable thickening time, less fluid loss, good settlement stability, and high compressive
Abbreviations: ABO-I AMR, ABO blood type incompatibility–related antibody-mediated rejection; ALC, alcoholic liver cirrhosis; CI, confidence interval; CTP, Child-Turcotte-Pugh;
Spin-polarised total density of states plot for Fe(111) surface with and without using.. Hubbard+U correction (U =
ON-Q* SilverSoaker* Antimicrobial Catheters are impregnated with silver on both the inner and outer surfaces of the catheter. The silver acts as the antimicrobial agent by releasing
Perseus, a Greek hero, with the help of Hermes and Athena, slew this dreadful monster.. Her mes lent him his magic hat and winged sandals Athena lent him her