Achieving Security for Data Access Control Using Cryptography Techniques
Full text
Figure

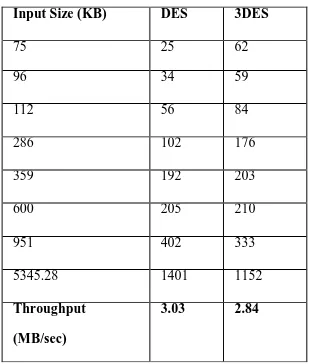
Related documents
096-2561-73 Plated Scout with O2/LEL/CO/H2S/PID sensors, internal pump, probe, 10' tubing, rechargeable Li-Ion battery w/ charger, foam lined hard case, calibration kit.
[87] demonstrated the use of time-resolved fluorescence measurements to study the enhanced FRET efficiency and increased fluorescent lifetime of immobi- lized quantum dots on a
The PROMs questionnaire used in the national programme, contains several elements; the EQ-5D measure, which forms the basis for all individual procedure
The implementation strategy in the Revised Plan draws on international experience in building high speed rail systems and has been tailored to address the unique circumstances
The summary resource report prepared by North Atlantic is based on a 43-101 Compliant Resource Report prepared by M. Holter, Consulting Professional Engineer,
Taking all the variables together, the producer most likely to have voted yes in the 1997 referendum (i) was an older individual with more years of experience growing cotton,
This study determined whether there was a significant relationship between teacher effect data in middle school mathematics and a teachers years of experience and whether there was
En efecto, así como los libertarianos ven en cual- quier forma de intervención del Estado una fuente inevitable de interferencias arbitrarias –con la excepción de aquella acción