The Basics of Wireless Local Area Networks
Andreas Johnsen
Student at Mälardalens högskola ajn05012@student.mdh.se
+46 712345678
ABSTRACT
This paper is written as a brief education about the basics of wireless local area network (WLAN). Definition and functionality is explained as well as advantages and disadvantages of WLAN compared to local area network (LAN). Three of the most successful and commonly used WLAN standards are presented and the development behind them. One of the biggest contributions of this paper is security of WLAN. It is shown why this is a big issue and how it is possible to tackle it with two popular security standards.
INTRODUCTION
When notebook computers became popular, many people dreamed about walking around the office with their computers as they were wireless connected to the internet. It didn’t take long for various groups to accomplish this goal and soon companies decided to have a wireless LAN standard.
Wireless LANs are increasing more and more in popularity, almost every company and every home have or can access a wireless Network (this isn’t totally true in continents like Africa). The 802.11 standard, which we will talk about in section 3, are causing revolution in computing and Internet access. Airports, shopping malls, train stations, hotels and universities are rapidly installing it.With wireless networks like WLAN comes great benefits and risks compared to LAN. To be able to understand the benefits and risks it’s crucial to understand how WLAN works in basics.
Wiring a network can be a very costly and time consuming operation. To be able to create a wireless network is a great advantage for companies because its very affordable compared to wired networks. It also gives a great flexibility for the clients that are using the network because it’s accessible from anywhere within the network area. The biggest risk with WLANs is the problem with security, for companies and organizations these risks are vital.
In section 1 we are going to define what a WLAN is and talk about how it works. We are also going to take a closer look at the advantages and disadvantages of WLAN in section 2. In section 3 and 5 we are going to look at the most common WLAN- and security standards.
1.
What is WLAN and how does it work?
A Wireless local area network (WLAN) is two or more computers that can communicate with each other by radio frequency. This allows the users within the network to share and access data, applications, internet etc. The biggest difference between a wired and wireless network is that you don’t need a physical connection to be able to connect a wireless network. This means that if you don’t have this in mind when building a wireless network almostanybody can access it. Another difference is that WLANs is much slower than LANs, today WLANs typically works up to 54 Mbps whereas LANs often work up to 1000 Mbps. There are a lot of different wireless technologies but most of the wireless LANs uses a standard created by the IEEE committee that’s called 802.11.
To be able to connect to a wireless network you need a wireless network interface card (NIC). These network cards are built in different forms and interfaces to suit different devices. PCI (Peripheral Component Interconnect) cards and USB adapters are the most common for personal computers. Today its most commonly that a wireless NICs are already built in when buying a computer or PDA (Personal Digital Assistant).[7]
Now we are going to look at the two main structures of wireless network.
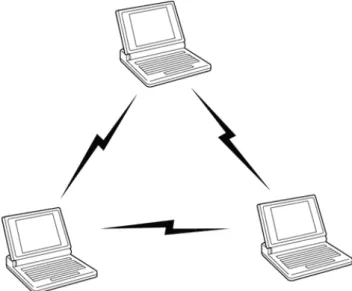
Ad hoc networking is the simplest form of wireless network, also called peer-to-peer. It’s basically when a couple of computers are communicating directly to each other in a mesh topology. It’s easy and fast to set up such a network for file transfers or LAN games and such, but it’s only for temporary purposes.
Figure 1: Model of the Ad hoc network
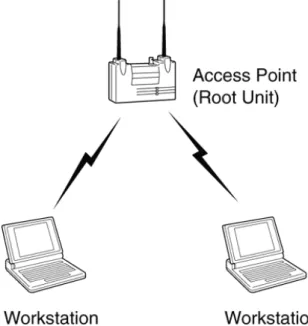
Infrastructure model is a network built on a base station called the access point (AP), where all the communication between network cards goes through. This access point is normally physically connected to the wired network and works as a bridge between the wired network and the remote computers.
There are mainly two different types of access points with different functionality, thick and thin access point. Thick APs are fully functional and can handle all processes by them selves. Thin APs only include antenna and radio so they rely on other controllers.[3][8]
Figure 2: Model of the Infrastructure
2.
Wireless vs. wired network
Wireless advantages:• Mobility- wireless LAN allow users to connect to the network from anywhere in the organisation, without having to find a specific place, thereby increasing the productivity.
• Reliability- Wireless LANs provide few wires and connectors which provide fewer problems for users and network administrators.
• Easy installation- Wireless LANs doesn’t need expensive and time consuming wire installation. This is of great significance in particular buildings.
• Scalability- It’s easy to configure a wireless LAN to different amount of users.
• Affordability- A wireless LAN is much cheaper than a wired LAN, especially in environments where frequently moves and modifications occur.
• Small ad hoc systems are very easy and quickly created. Wireless disadvantages:
• Security is one of the bigger problems in wireless network, its relative easy for outsiders to access or at least try to access a wireless network because no physical connection is needed. In wired networks the “intruders” has to overcome the initial problem of how to physically connect to the physical wires.
• Distance from connected devices to the access point is of great significance. Because of the frequency used in WLANs, distance between access point and devices are very limited. The distance also has big effects on the speed of the communication. In bigger building the range of the signals won’t be sufficient and additional access points have to be purchased. These costs can quickly become large.
• Wireless networks are very slow compared to wired networks. Wireless networks typically work in 1 up to 54 Mbps whereas wired networks work up to several Gbps. [4]
3.
Wireless LAN standards
As mentioned before soon after notebook computers got popular people was working on wireless networks. This work rapidly let to wireless LANs being marketed by a variety of companies. The trouble with this approach was that no two LANs were compatible with each other. Finally the industries decided that a wireless LAN standard would be a great idée. The IEEE committee that standardized the wired LANs was now upon the work of a standardized WLAN. The standard they came up with was named 802.11 and a common nick for it is Wifi (wireless fidelity). The name 802.11 comes from the LAN standards that had numbers like 802.1, 802.2 up to 802.10.
Now they were up to many challenges that had to be met. Firstly they needed to decide a suitable frequency band to operate in. This is not a trivial problem, dealing with the fact that radio signals have a finite range and that the users privacy had to be taken in thought. Limitations of battery and human safety also had an effect of choosing right frequency.
At the end the frequency was chosen to be 2.4 GHz. This frequency is the same as in microwave ovens which means that the energy of these signals on this frequency is easily taken up by water. Water molecules are dipoles’ meaning that it’s positively charged at one end and negativity charged at the other end. When exposed to microwaves the alternating electric field makes the molecules to align and rotate to the field, this creates friction and thereby heat.
This frequency was actually perfect for the job because almost nothing was used on that frequency and signals had short range which is desired in wireless LAN (otherwise it would not be a local area network). There are though a couple of apparatus that operate with 2.4 GHz frequencies as microwave oven, cordless phones and Bluetooth devices, so the access point should not be placed near these apparatus. These devices can cause radio frequency interference if they are to close to each other. Another challenge was that it was important to make 802.11 to be compatible with Ethernet. It should be possible to send IP packages over wireless LAN in the same way a wired computer sends an IP package over Ethernet.
There are some differences with Ethernet and WLAN that had to be dealt with by the standard. Computers on the Ethernet always listen to the ether before trying to transmit because only if the ether is idle the computer tries to transmit. Trying to do this on WLAN is not working quite well. I will show this in an example.
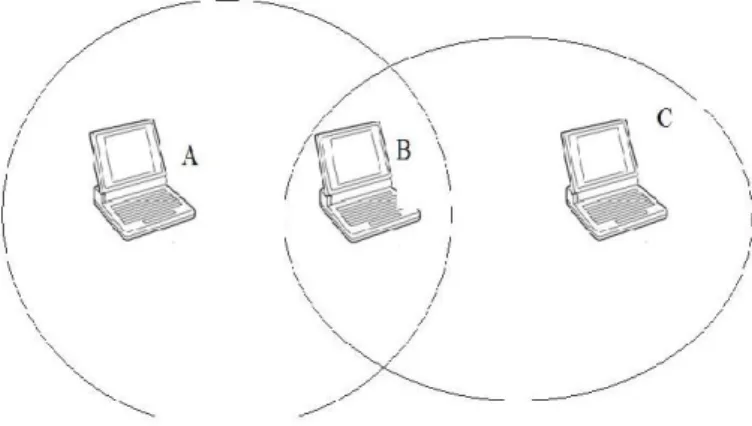
Take look at figure three, now suppose that computer A is transmitting to computer B who is within the range. Now suppose that computer C wants to transmit to B so therefore C listen to the ether to find out if someone is already communicating. But C is not within the range of A so C will not understand that A is transmitting to B. C will start transmit to B and the transmission will not succeed.
Figure 3: Wireless network where two computers are out of range of each other
This problem can be solved by sending some small information frames (“package”) called RTS (Request to send) and CTS (Clear to send) before starting the actual information transmission. The model here is that when computer A wants to send information to another computer B, it has to send a RTS frame to it. This frame contains of the information that A wants to send data to B and the length of data that will eventually follow. When B receives and accepts this package it will send a CTS to A. The CTS package contains of information that A is now allowed to transmit data to B and it also contains the data length that will be received, copied from the RTS frame. [3]
Now we look back at the problem explained above. Although C will not hear the RTS package sent from A to B, C will eventually hear the CTS from B and see the length of data that’s wanted to be transmitted. C will then be silent for the time it takes to send that amount of data. Though we have taken these precautions, collision can still occur. If A and C wants to transmit data to B and simultaneous sends a RTS, it will cause a collision and packages will be lost. In this case when a transmitter is unsuccessfully, in other words, a CTS hasn’t been heard in an expected time interval, it waits a random time and tries again. Another problem that had to be dealt with is that radio signals can be reflected of solid objects. This means that one signal can be received multiple times along multiple paths, called multipath fading. This problem can be solved by “frequency hopping spread spectrum”. If using a wide frequency band you can use it to prevent multipath fading. If the transmitter hops from frequency to frequency decided by a pseudorandom number generator used to produce the sequence of frequencies, and the receiver stay synchronized in time with the transmitter, they will hop to the same frequencies at the same time. By using this method to communicate, the receiver will be able to ignore reflected signals. Reflected signals always have longer paths than the direct signal,
so when the reflected signals arrives to the receiver the frequency has been changed and the signal is ignored. This method is also applied on Bluetooth. [3]
After some work the committee came up with a standard in 1997 that had solved these and other problems. This 802.11 standard supported speeds up to 2 Mbps which was almost directly complained that it was to slow. This resulted in two different developments within the committee, in 1999 two new standards emerged, the 802.11a and 802.11b standard.
• 802.11a: The 802.11a standard operates in the 5 GHz band and runs at speed up to 54 Mbps. Higher speeds are possible up to 23 meters and lower speed at 50 meters. Four, eight or up to twelve channels can be used and this makes 802.11a suitable for enterprise solutions needing bandwidth and high speeds.
• 802.11b: The 802.11b standard uses the same frequency as the original standard (2.4 GHz) but uses different modulation technique to achieve a nominal transfer rate of 11 Mbps and tree channels. Higher speeds are possible up to 30 meters and slower speeds up to 75 meters but these ranges vary. 802.11b devices are popular for home users and business because they are affordable and available.
To make things more complicated a never standard has been developed by the 802 committee and that standard is 802.11g.
• 802.11g: This standard uses modulation technique of 802.11a but operate in the frequency band of 802.11b. So it operates in 2.4 GHz with three channels and speeds up to 54 Mbps. It has backward compatibility with 802.11b so older devices can still be used with the new standard. The range is better than 802.11a but still have the speeds of 802.11a. [2][8]
4.
Security threats
Security as mentioned before is a big issue and this issue can be divided into two types: active and passive threats. Passive threats are when individuals try’s to gain information from the network for their own benefits. Passive threats can also give material for future active threats. Active threats are when an intruder manipulates and modify the data or traffic in the network. We will now look at the most common passive and active threats. Passive threats:
• Eavesdropping: This isn’t a threat only to wireless networks it’s a very old and common threat. Basically Eavesdropping is when the intruder listen to things he or she shouldn’t listen to.
• Traffic analysis: For some intruders information about if any massages are being sent, who’s the sender and the receiver, the size of the message and on what frequency it is sent, is enough. This threat when the intruder only wants information about the traffic in a network rather than the actual information being sent is Traffic analysis.
Active threats:
• Masquerade: If an intruder gets information (maybe thru Eavesdropping) about a user’s authentication data, like username and password. It is possible for the intruder to connect to the network and act as a trusted user. This threat is called Masquerade or “spoofing”.
• Authorization violation: This threat can equally be done by an intruder as well as a trusted user. In a network there are often services and resources that are only intended for a number of users in the network. If the threat comes from an intruder it is similar to Masquerade, an intruder that has joined the network has already violate his or hers authorization. A trusted user could also try to access these services and resources though he or she isn’t authorized. The trusted user could do this by active attacks or if the network has lack of security.
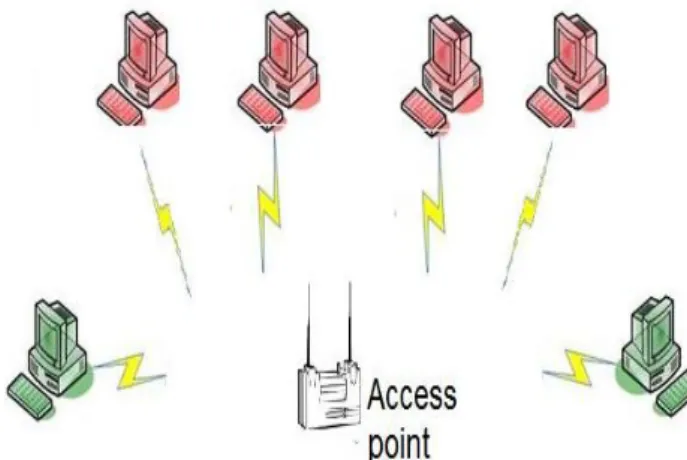
• Denial of service (Dos): Dos attack is when someone tries to prevent or reduce normal use of communication services. This can be done by sending data to devices within the network to cause overload of traffic in the system. If the network fills up with “garbage” data eventually the network will slow down or even crash. In wireless networks Dos attacks can be done by interference of radio signals.
• Modification or forgery of information: An intruder creates new information as a trusted user in the network or modifies or even destroys data being sent. [2]
Figure 4: Model of a Dos attack, intruders (red) overwhelming an access point with traffic blocking authorized users (green)
5.
Security standards
As described before, to get access to a wired network one has to physically get in contact with the wires of the network. This issue has never been posed as a significant problem because organizations and companies often have a sufficient physical security. But with wireless LANs it is a fact that radio signals are going outside the walls of companies and even crossing others. So with this in mind physical security is pretty much irrelevant to
piggybackers (A piggybacker is someone who’s using a wireless network without the subscribers permission). Anybody within the geographical network area can listen to the traffic and even make traffic in the network if it’s not secured and encrypted. Lack of knowledge when setting up these wireless LANs will probably result in that someone nearby will use it without permission. Today almost all access points include Wired Equivalent Privacy (WEP) encryption and very often it’s turned on when distributed.
WEP basically works like this. When turned on the NIC encrypts the frame body (“package” to be sent) including the CRC (Cyclic redundancy check, a method used to check if any data has been corrupted when transferred) for each 802.11 standard frames before transmission, using a stream cipher called RC4. When the encrypted frame has arrived to the receiving station, an access point or another wireless NIC, it is decrypted. This means that 802.11 WEP only encrypts data between 802.11 stations, so when a frame enters a wired place of a network, WEP no longer applies. WEP has a specified shared secret 64-bit key that is used to encrypt and decrypt data. The transmitter uses a key to encrypt the data and the receiver must use the same key for decryption, so each radio NIC and APs must be manually configured with the same key.
In the encryption process WEP prepares a “seed” by joining together the shared secret key supplied by the user and a random generated 24-bit initialization vector called the IV that is changed for every transmitted frame. Then WEP inputs the “seed” into a pseudo-random number generator (RC4) that produces a keystream that’s equal to the length of the frames payload (body) and an additional 32-bits integrity check value (ICV). The check value is for ensuring that a transmitted frame hasn’t been manipulated or changed somehow. The receiver of the frame recalculates the check value and if nothing has been changed it should match the check value sent in the frame. If the check values don’t match the receiver simply reject it.
Before the transmission starts WEP combines the keystream, with the payload and ICV through a bitwise XOR figure 5 shows this process which produces the encrypted data. Now WEP includes the IV without encryption within the first bytes of the frame body that now is encrypted. This is then transmitted to the receiver who uses the IV along with the shared secret key, supplied by the user of the receiver station, to decrypt the payload of the frame. [6]
But in the beginning of 2001 WEP became highly criticized. Several serious weaknesses emerged by cryptanalysts and the result is that a WEP connection can be cracked with easily founded software within minutes.
One problem with WEP is that the IVs are only 24 bits long and eventually WEP will use the same IV for different data packets. For large and busy networks this reusing for IVs will result in transmissions of frames that have keystreams that are very similar. If collecting enough frames with the same IV one can determine the shared secret key, i.e., the hacker can decrypt any frame transferred. [1]
A new security standard that solved the problems with WEP had to be created, and it sure did.
WPA is abbreviation for Wi-Fi Protected Access, which is a security standard that can be cracked like WEP if using a weak password, like a dictionary word. But if using a password long enough with random letters, makes WPA virtually uncrackable. WPA has the same purpose as WEP, to encrypt the traffic in WLANs and keeping the information in the network secured from intruders. WEP uses a statical key for encryption which is not the case with WPA who uses a dynamic key. WPA has a system that distributes keys to all units within the network which means that keys to encrypt data can be changed in intervals. This makes it much harder for intruders to crack the network. Also WPA uses a better algorithm for encryption than WEP, this algorithm is called Michael.
Although WPA is a much more secure and improved standard compared to WEP there has been some furhter development of the WPA standard.
WPA2 is as mentioned a further development of WPA where some parts has been improved. The main advantage of WPA compared to WEP is that the units them self’s can exchange new encryption keys dynamically. WPA2 has taken this advantage further by thru a four step process the transmitter and the receiver identifies each other and agrees an encryption key that only last for one moment. This means that there can be several keys within the network at the same time. Also WPA2 better supports roaming between APs. This means that it is possible the move in a bigger WLAN that contains of several APs. When the connection changes from one AP to another within the network the connection won’t be cut. [5][9]
There are a lot of things that can be done to have a more secure Wireless LAN, so here come practical steps that should be done.
• Devices with WEP security should be upgraded to WPA if possible.
• Access points can be configured to only permit devices with a recognized MAC (Media access control) address. Every NIC has an individual physical address called a MAC address. These addresses can be stored in a list supported by the AP, called the Access Control List (ACL). Then only devices with the specific MAC addresses will be accepted by the AP.
• APs are delivered with default username and password that are widely known and must be changed to provide a secure network.
• Access points SSID (Service Set Identifier) are often by default set to be broadcast. SSID is a wireless method that identifies or names an individual network. Broadcast of the SSID should be set of when possible.
• When networks are not used for a longer period of time the access points should be turned of.
• Firmware of wireless devices should be updated as it develops.
• Maximum numbers of clients should be set on APs.
• Disable the ability to log in and manage APs wireless. If considering these points when creating a WLAN it’s a good beginning of a secure network.
SUMMARY AND CONCLUSION
The technique of radio singles isn’t a modern and new technology but combining computer communication with radio signals to create a computer network is. It has been a great success because of some great advantages though there are some disadvantages that have to be met, like security. A WLAN can operate in two different models, ad hoc networking and an infrastructure system. Infrastructure is the most common way to build a WLAN but an ad hoc system is very useful when a temporary WLAN is wanted. Three of the most common WLAN standards are 802.11a, 802.11b and 802.11g. The 802.11b standard is the most used standard because of its affordable and available. It doesn’t support high speeds like 802.11a and 802.11g but it has a good range. It has been shown that the popular security standard WEP isn’t a sufficient way to secure a WLAN. A new more developed standard WPA is a much more secure standard as long as you use a good password.
REFERENCES
[1] Miller, Stewart 2003, Wi-Fi Security, McGraw-Hill Professional, 9780071410731.
[2] Neeli, Prasad 2005, 802.11 WLANs and IP Networking: Security, Qos, and Mobility, Actech house, Boston,London, 9781580537896.
[3] Tenenbaum, Andrew 2003, Computer networks, 4th edition, Pearson Education international, New Jersey, 0-13-038488-7.
[4] Truelove, James 2002, Build Your Own Wireless LAN, McGraw-Hill Osborne, 9780071380454.
[5] Pagani, Margherita 2005, Mobile and Wireless Systems Beyond 3G: Managing New Business Opportunities, IRM Press, 9781591405450.
[6] Jim Geier , 802.11 WEP: Concepts and Vulnerability, Wi-Fi planet.(10-10-2008)
[7] Becta, Wireless local area network.(09-10-2008)
http://foi.becta.org.uk/content_files/corporate/resources/technolog y_and_education_research/w_lans.pdf.
[8] Daniel Jönsson ,WiFi IEEE 802.11, omWLAN.se. (28-10-2008) http://www.omwlan.se/artiklar/wlan/WiFi.aspx.
[9] Daniel Jönsson, Kryptering I WLAN, WEP, WPA, WPA2, omWLAN.se. (28-12-2008)
http://www.omwlan.se/artiklar/saekerhet/Kryptering-WEP-WPA-WPA2.aspx.