Approaches to IT Security in Small and Medium Enterprises
Full text
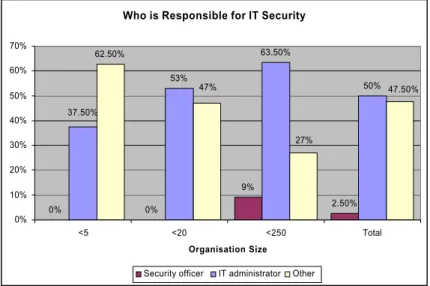
Figure



Related documents
innovation in payment systems, in particular the infrastructure used to operate payment systems, in the interests of service-users 3.. to ensure that payment systems
The application of solid state faults current limiter (SSFCL) in power system offers an active way to overpower faults current and result in significant saving in
Fidelity Freedom K® Income Fund FFKAX Target Date Fund Fidelity Freedom K® 2010 Fund FFKCX Target Date Fund Fidelity Freedom K® 2015 Fund FKVFX Target Date Fund Fidelity Freedom
Least square-support vector (LS-SVM) method for modeling of methylene blue dye adsorption using copper oxide loaded on activated carbon: Kinetic and isotherm study. Removal of
Large investment banks, institutions & hedge funds spend millions of dollars each year on developing pair trading programs and the application of them, they know it’s crucial
Display Experiment Neatly Data: Tables Charts Graphs..
Share of the value of reported total exports of other business services and computer and information services, selected countries, 1995 and 2002 .... Growth of the value of exports
We here report the results of this post hoc gender analysis aimed to evaluate in the PROXIMA SAA population (i) the association between gender and presence of perennial or

