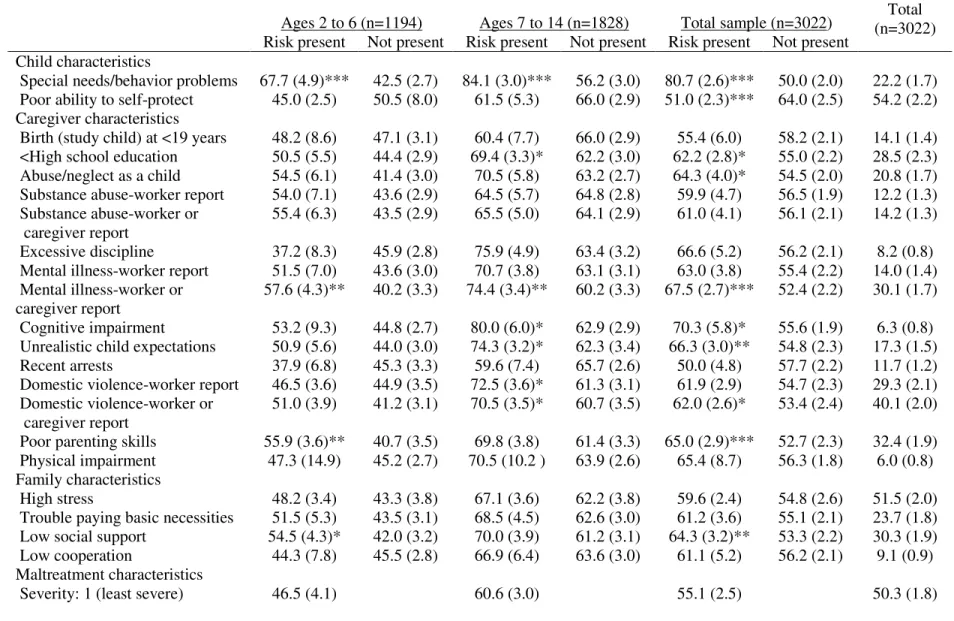
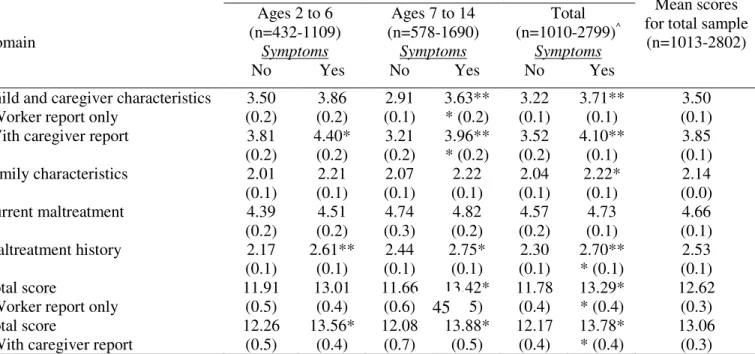
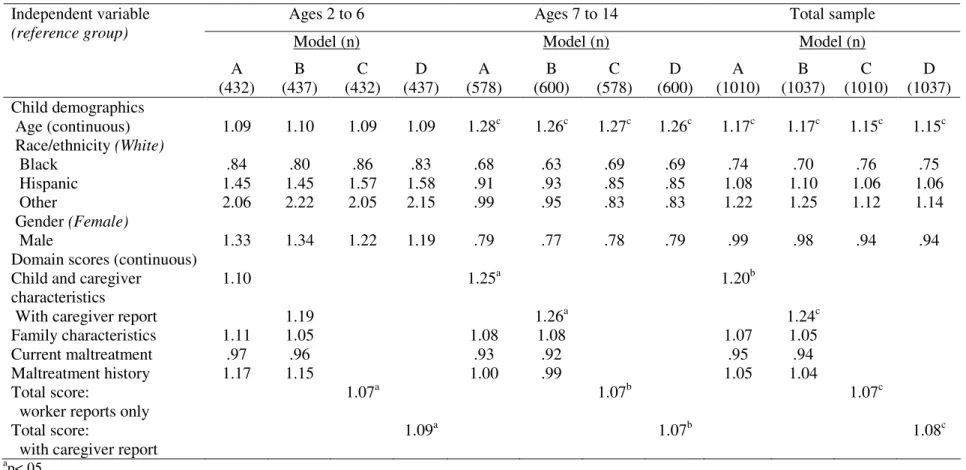
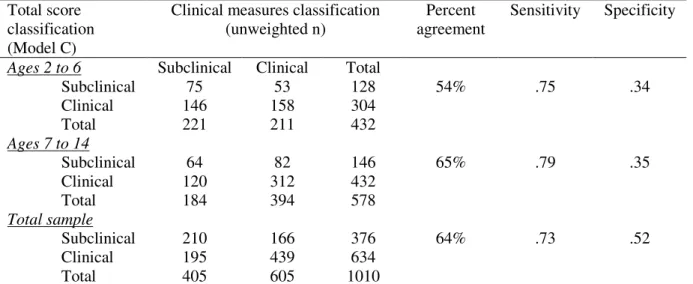
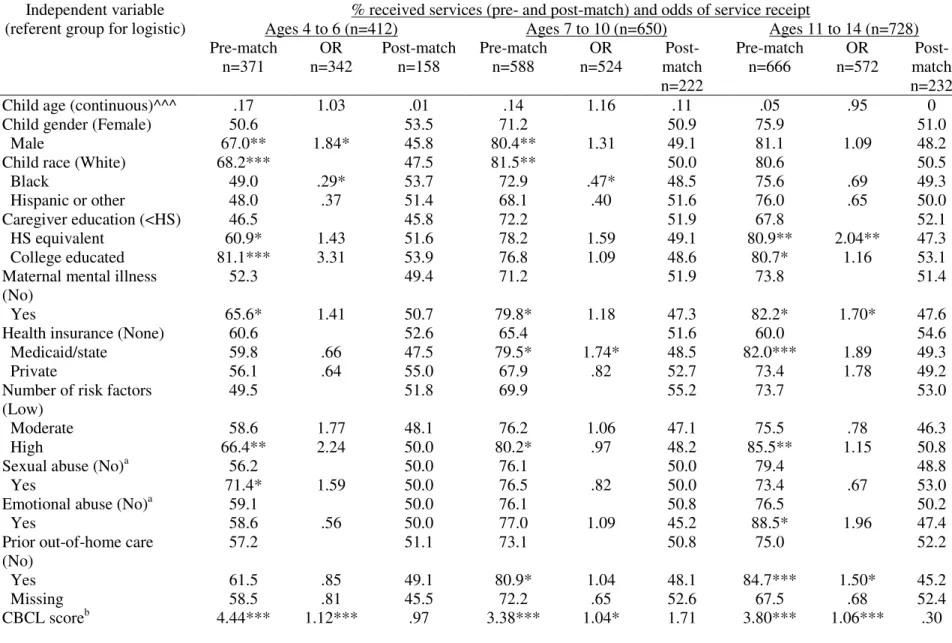
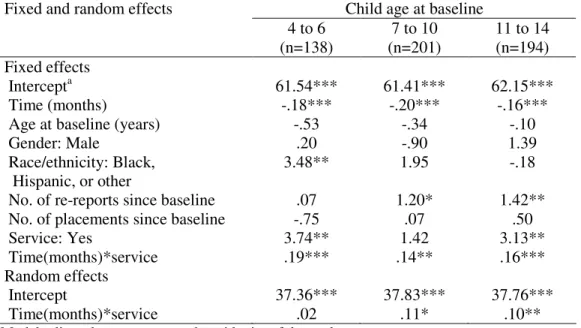
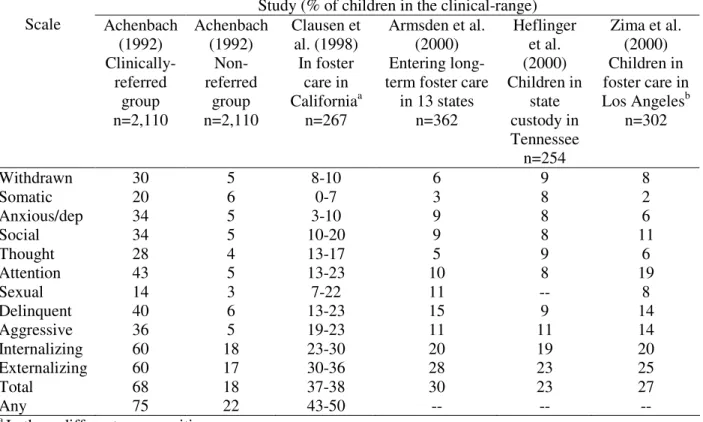
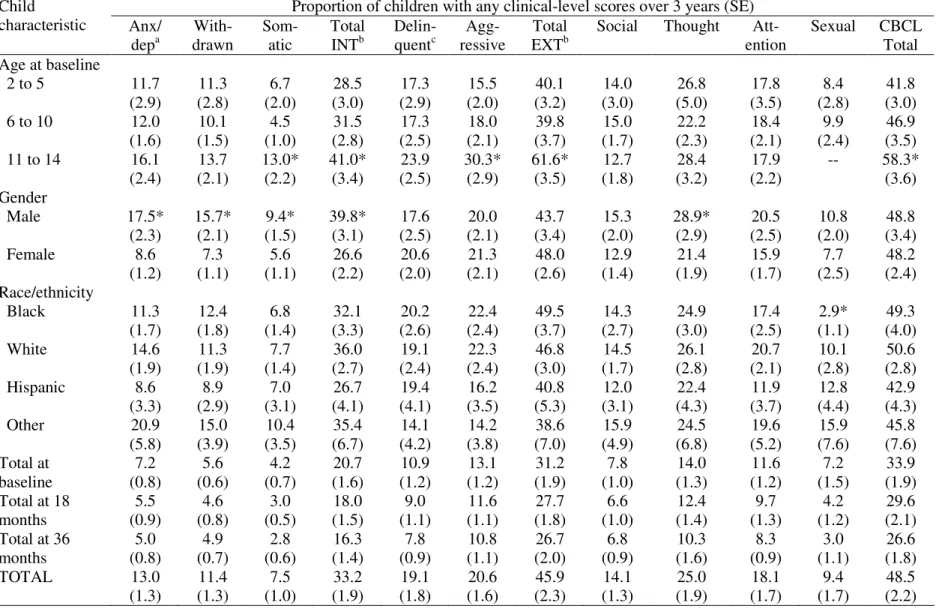
Identifying and meeting the needs of maltreated children with mental health problems
Full text
Figure
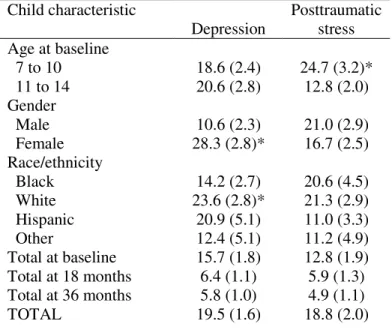
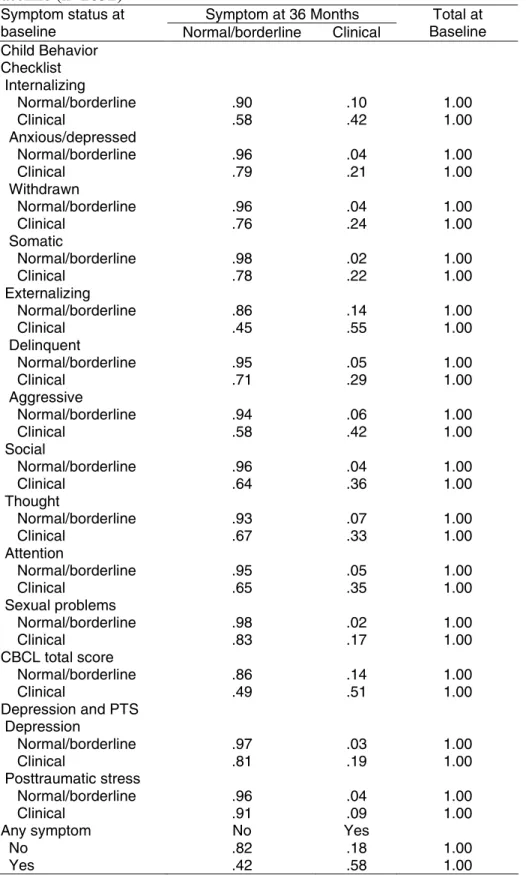
Outline
Related documents
PVC (vinyl) reference Seat 110TA8632 ACCESSORIES COMPLETE SEATS PVC (vinyl) reference.. Static
The case study of the course Communication and Organizational Development for engineering students illustrates, though, that even with large group study courses the application
The mean score obtained will be used as a measurement to determine the level of consent a qualification description of the Malaysian Qualifications Framework which may be proposed
In more detail, these authors identi- fied twelve crucial criteria concerning BIID (or apotem- nophilia): age at onset, advanced age at desire, disclosure to family and doctors,
Namely, spermine amount per calorie was significantly associated with supply of many Mediterranean diet foods, such as olive oil, fruit, seafood, cheese, and wine, relative
prices, the exchange rate, a contemporaneous and lagged unit labour cost term. suasarized in a first period moving average, a money term proxying
More precisely, after incorporating structural change, the speed of convergence at regional levels is faster than at the country and industry levels, which shows that struc-
This analysis can be done through various computing software such as Data Mining or Machine Learning techniques [28]. TCPDump, Wireshark, TCPFlow, TCPTrace, OllyDbg, IDA Pro,