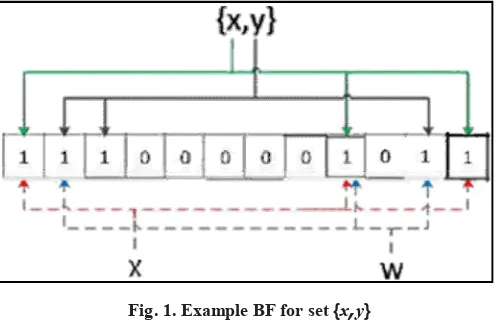
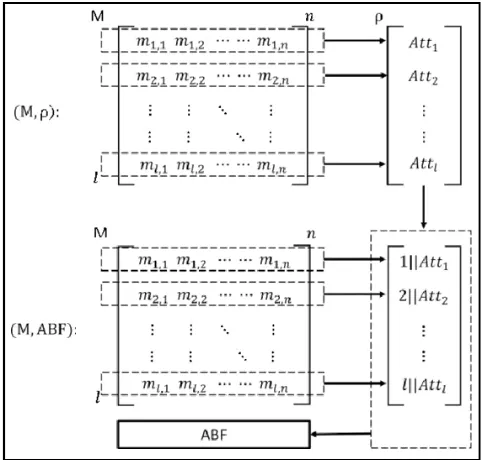
Access control scheme to big data using privacy preserving policy
Full text
Figure
![Fig. 7. Computation time comparison between the ABE in [6] and our scheme (data size: 1 KB, security parameter: 1024)](https://thumb-us.123doks.com/thumbv2/123dok_us/8890967.950701/7.595.309.560.110.503/fig-computation-time-comparison-abe-scheme-security-parameter.webp)
Related documents
In the case of strongly anisotropic coiled fibres this image rotation is not accompa- nied by the polarization rotation [17] and is the only topological effect.. In this section we
Based on it, the essential technology - augmented reality is studied for unmanned fully mechanized longwall face automation production, through the virtual-real combination,
The aim of this research is to propose a model-based test case prioritization technique for regression testing in order to achieve early fault detection so that it is
Oleh itu, dengan adanya kebolehubahsuaian sifat kimia dan fizik cecair ionik melalui penggunaan kombinasi kation dan anion yang pelbagai, secara langsung ini akan memberikan
Identity provider (IP): IP is defined in the claim definition. It possesses knowledge about the subject and transforms it in the form of claims. It will be able to
In this paper we have proposed a test for a unit root in autoregressive moving average time series models based on an instrumental variable estimator. The main advantage of
Since quasigroups in general do not have algebraic properties such as associativity, commutativity, neutral elements, inverting these functions seems to require exponentially
In this paper, a novel configuration of double ridged horn antenna including a five layers polarizer at the horn aperture is proposed providing wideband and dual