Secure and Trusted Information Brokering In Cloud Computing
Full text
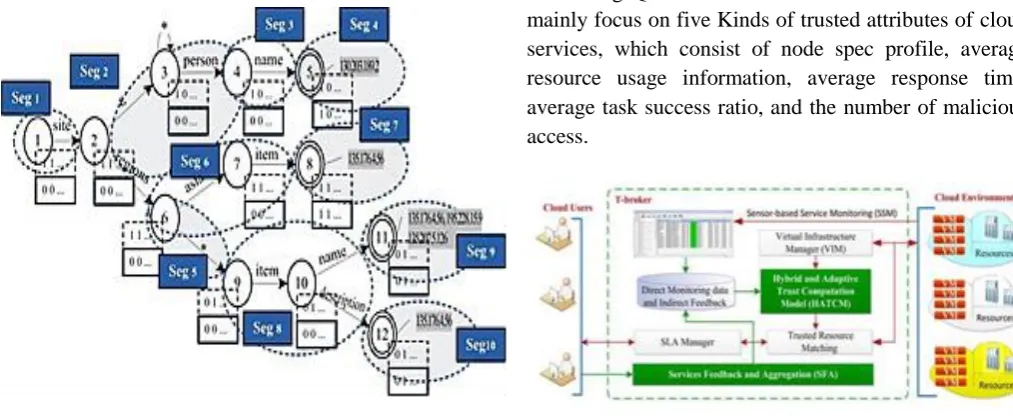
Figure



Related documents
So make sure that you have adequately researched the market and know the market value of the position you are negotiating, not just for women in similar positions, but for both
In this manuscript, an Economic production quantity (EPQ) model have been formulated for deteriorating items under partial trade credit policy with crisp and fuzzy demand.. Then
Although Federal Reserve Chairman Ben Bernanke said in mid-September the downturn was “very likely over,” he added that “it’s still going to feel like a very weak economy for
•Work on developing your own 6 station circuit •Be able to use the couch to 5k app to carry out sessions to improve cardiovascular fitness •Be able to carry out a range
The status review also pointed out that, as regards people with concurrent mental illnesses and drug or alcohol problems, there is a big gap between the recommended
The R&D elasticities computed in this study indicated that when the government invests ten per cent of the rice subsidies in R&D expenditures focussed in rice
The regression extends the specification in Grinblatt and Keloharju (2001) by adding a herding variable and by interacting the regressors with individuals’ IQ scores.
After controlling a variety of feeder cattle characteristics and market and sale conditions, we estimate the price premiums for preconditioning (vaccinations and minimum 30