CLOUD COMPUTING IN MOBILE AND ITS SECURITY
Full text
Figure
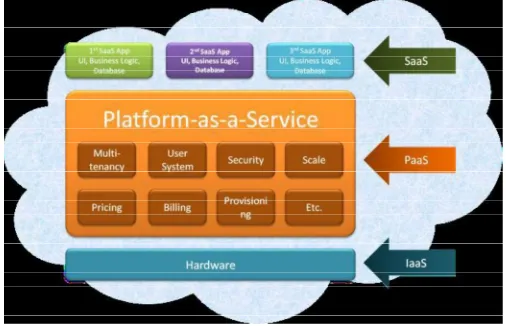
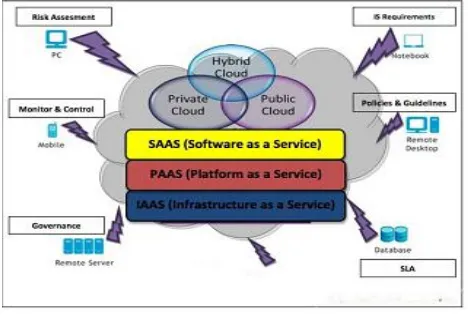
Related documents
1 M.Sc of Health, Safety and Environment Management, Department of Health, Safety and Environment Management, Faculty of Health, Kashan University of Medical Sciences, Kashan, Iran•
But even when integration needs outstrip the scope of IFS Financial Connector or the SAP functionality in question is too old to support Web services, IFS Applications is structured
Samples were consolidated by hot press (HP) or Spark Plasma Sintering (SPS). HP samples were heated to a temperature of 850 °C and held for 60 minutes, and remained under a
Be trained in an LPS class (as specified for Categories I, II, and III: Residents, Professional Staff With Admitting Privileges, and Professional Staff Without Admitting Privileges,
In the context of the WFD, one emphasis is on river networks, flexible additive models are another set of statistical tools that are gaining widespread use in the
(Without these two items, the collection/test will not be performed). 3) You must sign an Employee Consent Form, such as Appendix F, in order to proceed with the test. 4) You
Raw Materials Procurement and Logistics Proprietary, Software-Based Raw Materials Cost Optimization Scrap Management and Preparation Semi-Finished and Finished Material
According to the case-law of the European Court of Human Rights (hereinafter: Court) Article 1 protects only existing property and does not grant right to regain property