Information Security Management: Password Security Issues
Full text
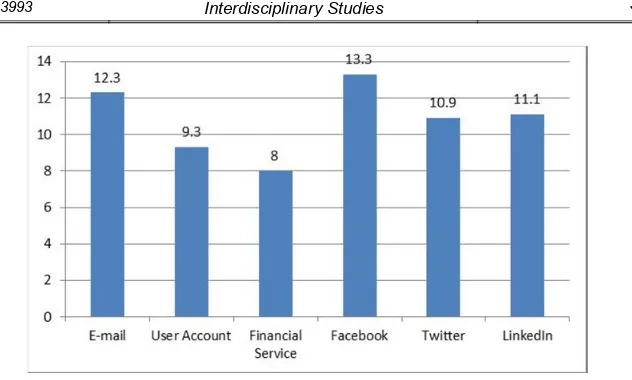
Figure



Related documents
As a consequence in the past fi scal year GEA Group’s order intake fell by 1.1 percent year- on-year (excluding the Thermal Engineering Division, which is characterized by large
Upon employment, the long-term care facility shall: (a) Notify the employee of the requirements of this section and request that the employee agree to be immunized against
For example, deep cryogenic treatment (DCT) improves wear resistance of tool steels; but, for cold work Cr8Mo2SiV and Cr12MoV tool steel specimens, Li et al.. (2010) reported
Neither of the two companies regard the capability to integrate the product into the sporting event, the possibility to achieve a competitive advantage in the market place, the
Personal profiling, individual coaching and mental training (mindfulness) as well as lectures, new knowledge and relevant exercises are the elements that will enhance
The National School of Government will be an important enabler to the implementation of human resource development/training policy in the Public Service through the provision
touring to ARKEN Museum for Moderne Kunst, Copenhagen, Denmark Joan Miró , Graphikmuseum Pablo Picasso Münster, Münster, Germany Joan Miró, Galería Leandro Navarro, Madrid,
IT IP Technology Servers Computers Wiring Closet Routers Switches Phones White Space Management IT Applications Network Management Systems IT / Server Room management