Integrated Real-Time Intrusion Detection System Using IoT
Full text
Figure
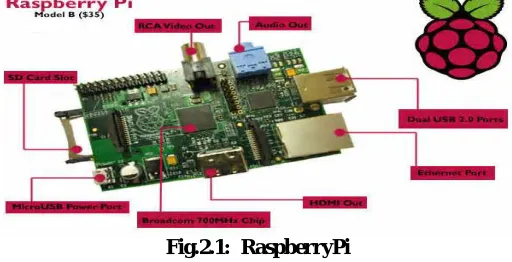
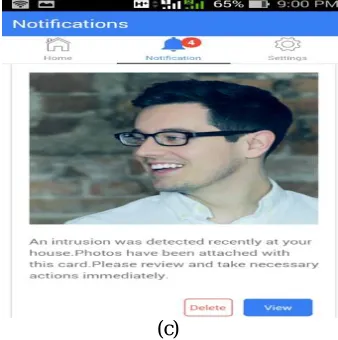
Related documents
It is well known that projection plays a pivatal role in functional analysis and linear algebra hereat to develop functional analysis and linear algebra, we take care of the
Lagrange optimal controls and time optimal controls for composite fractional relaxation systems Lian et al Advances in Difference Equations (2017) 2017 233 DOI 10 1186/s13662 017 1299 7 R
And the bandwidth ,Gain is improved by replacing the shape of microstrip patch antenna by inserting the more slots inside the rectangular patch in the shape of
Grained Attribute Based Data Storage in Cloud. Computing International Journal of
> Injury = or > personal injury = means only injury by accident arising out of and in the course of the employment and shall not, except as hereinafter provided, include
Extending seasonal malaria chemoprevention to five cycles: A feasibility and acceptability study in Cascades region, Burkina Faso.. 2020 Annual Meeting of the American Society