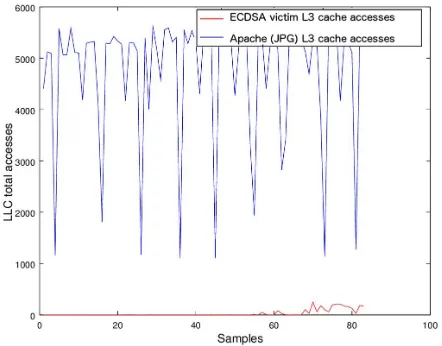
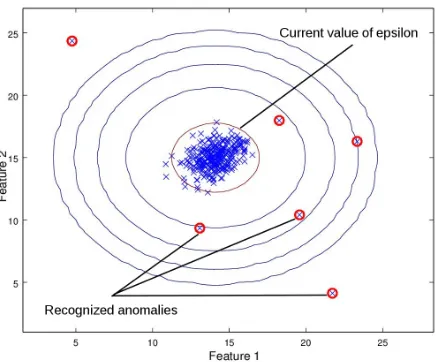
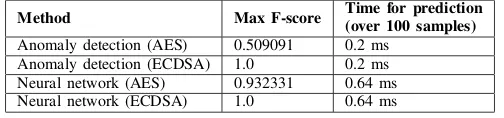
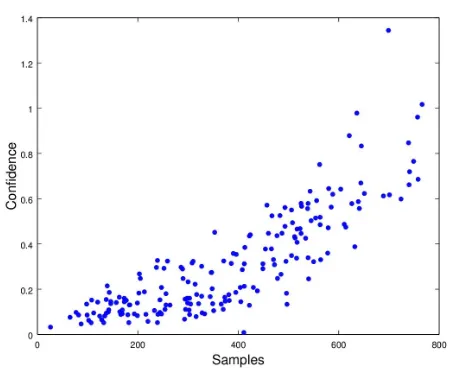
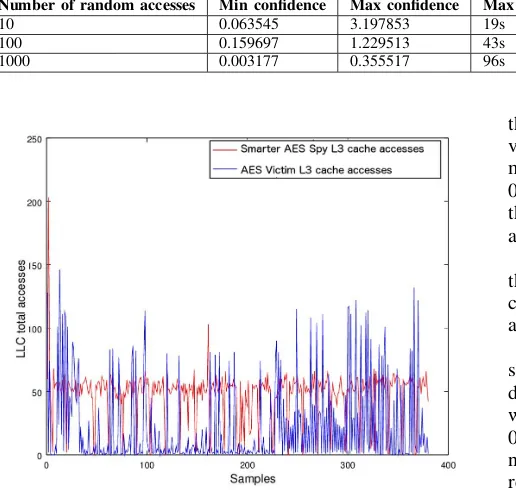
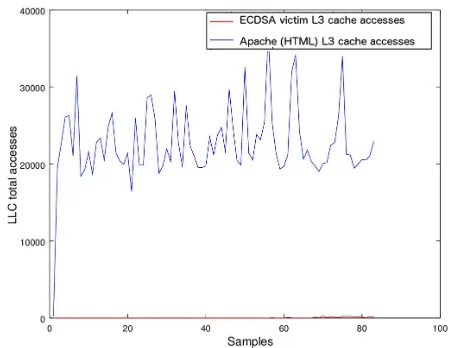
Real time detection of cache-based side-channel attacks using Hardware Performance Counters
Full text
Figure


Related documents
Papadopoulos et al 15 reported that 142 pa- tients with osteoporotic vertebral fractures who underwent a unilateral transpedicular approach achieved satisfactory results in terms
capita income from all sources was found to be ` 61.12 for marginal farmers, ` 70.25 for small farmers, ` 90.29 for medium farmers and ` 109.32 for large farmers with
However, few children were ex- cluded from either rural or urban areas as a result of prior case status because the erythrocyte protoporphyrin screening test that was used
The charter incorporated three key clauses relevant to the latest time for redelivery: the basic period clause, stated to be 11 months plus or minus 15 days at charterers’ option;
This engagement will include the development of the schedule of assignments described in (ix) above. xi) The Panel commends the current induction programme which is
This design thus exploits the robust nature of open model survival rate estimators (see Cormack, 1972; Carothers, 1973; Nichols et a1. ,1983) and the diversity of closed models
The k -Linear assumption family has been successfully used to build chosen ciphertext secure en- cryption [HK07, Sha07]; to construct pseudorandom functions [LW09, BMR10]; to
sourdough, being the levels of acetic and D/L lactic acids in dough and