A comparative study and analysis between the PP model and Current Security Compliance models
Student Name: Kumar Dangi
Student ID: S264185
Master of Information Technology (Software Engineering)
School of Engineering and IT
Faculty of EHSE
Charles Darwin University
Darwin
October 2015
Thesis supervisors
Dr Jamal El- Den
Dr Peter Shaw
Unit Coordinator
Dr Kamal Debnath
NAME: Kumar Dangi
COURSE TITLE: Master of Information Technology (Software Engineering) SPECIALISATION: Software Engineering
THESIS TITLE: A comparative study and analysis between the PP model and Current Security Compliance models
THESIS SUPERVISORS: Dr Jamal-el-Den and Dr Peter Shaw
Abstract
Keywords: Information Security, Compliance, Positive psychology, Behavioural theory, Positive traits
We live in an age where “information” and “security” are the two pivotal elements of human society. The security of the information, therefore, has now been an area of great concern and its importance been intensified exponentially. Organizations develop, formulate and update security compliance policies and standards to ensure that every bit of information is well protected and under the umbrella of security policies and high scrutiny of organizational care. The past researches conducted in the domain of human behavioural studies highlights the fact that internal threats are more pressing and detrimental than the external threats. Thus, internal threats predominantly is the outcome of poor user security behaviour and sometimes, due to poor security compliance policies of the organization.
In this research, we draw, explore and analyse on literature in the area of behavioural compliance theories such as General Deterrence theory, Protection motivation theory (PMT), Theory of Planned Behaviour (TPB), Rational Choice theory and Job Demands-Resource Model (JR-D). We proposed the PP model (Positive Traits, Personal Strength), which shows the requirements for employees’ information security compliance. The introduced PP (Positive Traits, Personal Strength) model is a framework that is based on two main personal positive characteristics namely, the employee’s positive traits (courage, interpersonal skills, wisdom, positive experience, leadership skills) and personal strengths (self-efficacy, expertise, optimism). We strongly believe that organizations’ identification
and awareness of these traits within their employees would result during the development of security policies would result in sustainable employees’ security compliance.
Acknowledgement
I would like to extend my deepest gratitude and thanks to my supervisors Dr Jamal El-Den and Dr Peter Shaw and unit coordinator Dr Kamal Debnath. Especially, I am very obliged and thankful to the reviews, corrections and suggestions provided by my first supervisor Dr Jamal El-Den. This research paper would have never been complete without your constant support, supervision and constructive suggestion. Your guidance and expertise has ignited a spirit of research in me and helped me successfully complete it.
I would also like to thank my university and its learning resources that helped in every step of my work. Particularly, the library resources and the workshops provided by the university always instilled confidence and motivation in me. I would like to thank my family whose love and encouragement made my work exciting and comfortable in so many ways.
Lastly, I would like to thank my wife Kalpana who always stood by me in good and bad times encouraging and cheering me up.
Kumar Dangi
Table of Contents
LIST OF FIGURES ... LIST OF TABLES ... Abbreviations ...
1. Introduction ... 1
1.1 Aim and Scope of the thesis ... 2
1.2 Research approach or methodology ... 3
2. Background ... 3
2.1 Theory of planned behavior ... 4
2.2 Social cognitive theory ... 4
2.3 Social bond theory ... 5
3. Literature Review ... 5
4. Positive Psychology ... 8
5. Relation between personal strength and security compliance... 11
6. Self-efficacy ... 15
7. Knowledge Management and Expertise ... 15
8. IS Security Knowledge Management ... 17
9. Positive Organizational Behavior and Security Compliance ... 18
10. Research Framework ... 20
10.1 Conceptual Model ... 20
10.2 Top management and Organizational Policies ... 21
10.4 Individual Cognition ... 24
10.5 Organizational culture ... 25
11. Introduction to Information Security Governance ... 27
11.1 A practical approach for ISG ... 28
11.2 Business Software Alliance ... 28
11.3 Information security policy: An organizational-level process model ... 28
11.5 ISACA ... 29
11.6 ISO/IEC Standards ... 29
11.7 ITGI ... 30
12. User Security Behavior ... 30
13. An analysis of security behavior theories ... 32
13.1 General Deterrence Theory ... 32
13.2 Protection Motivation Theory ... 33
13.3 Rational Choice Theory ... 33
12.4 Job Demands-Resources Model ... 34
13.5 The PP (Positive Traits, Personal Strength) model ... 38
14. Conclusion and Recommendation ... 42
15. Appendices ... 43
15.1 Appendix A- Glossary ... 43
15.2 Appendix B- Search Terms ... 44
LIST OF FIGURES
FIGURE 1 POSITIVE PSYCHOLOGY IN RELATION TO OTHER PSYCHOLOGY (HEFFERON AND BONIWELL, 2011) ... 10
FIGURE 2 SELF-EFFICACY IN INFORMATION TECHNOLOGY (RHEE ET AL., 2009) ... 13
FIGURE 3 SPIRAL OF ORGANIZATIONAL KNOWLEDGE CREATION (NONAKA, 1994) ... 18
FIGURE 4 CONCEPTUAL MODEL OF SECURITY COMPLIANCE ... 21
FIGURE 5 FACTORS INFLUENCING USER SECURITY BEHAVIOUR (LEACH, 2003) ... 31
FIGURE 6 THE PP MODEL ... 41
LIST OF TABLES
TABLE 1 HISTORY OF PSYCHOLOGY... 10TABLE 2 THEORIES APPLIED IN SECURITY POLICY COMPLIANCE ... 37
Abbreviations
ATB: Attitude Towards Behavior CDU: Charles Darwin University
COBIT: Control Objectives for Information and Related Technology COM: Computer Monitoring
CSE: Computer Self-Efficacy CSI: Crime Scene Investigation CVF: Competing Value Framework GDT: General Deterrence Theory InfoSec: information security IS: Information System
ISACA: Information Systems Audit and Control Association ISG: Information Security Governance
ISO: International Organization for Standardization
ISO/IEC: International Organization for Standardization and International Electro technical Commission IT: Information Technology
ITGI: Information Technology Governance Institute JD-R: Job Demands-Resource)
PBC: Perceived Behavioural Control PMT: Protection Motivation Theory PP: Positive Traits, Personal Strength RCT: Rational Choice Theory SBT: Social Bond Theory SCT: Social Cognitive Theory SE: Security Efficacy
SN: Subjective Norms
TPB: Theory of Planned Behavior TRA: Theory of Reasoned Action USB: Universal Serial Bus
1. Introduction
According to the report by 2010/2011 Computer Crime and Security Survey, it has been revealed that 45.6 per cent of the respondent from major government agencies said that they have encountered at least one security attack per year. This report presented a lack of visibility in terms of severity, degree of the attack and prevention mechanism. The research from industry suggests that more than 75 per cent of the cost of security failures usually stem from the activity of the insider of the organization. Similarly, a research on the security breaches during 1997 to 2003 revealed that there is a 53 per cent increase in security breaches as reported by the respondents(Silic and Back, 2014). These data suggests that effective InfoSec is the demand of today’s world.
Information Security, also known as InfoSec, is the way to preserve the information from unauthorized access, use, disclosure, perusal, recording, disruption or destruction. It includes any form of data either physical or electronic. Confidentiality, integrity and availability are the basis of information security. In lack of any one of these elements security of information becomes incomplete and is vulnerable to threat. Confidentiality means the information should be safe wherever it is stored and should not be disclosed maintaining complete privacy. Some practical real world example includes our credit card information in the bank, the record of patient in the hospital, etc. If the organization cannot maintain confidentiality it will eventually face a loss of goodwill and its business.
Integrity refers to completeness and wholeness of the information. Without integrity information becomes unreliable and loses its value. Integrity of the information can be damaged due to intentional or
unintentional breaches of information security. For example: if the information of account holder in the bank is altered, it can be a serious subject of privacy exploitation and bank may face lawsuit.
Availability is another important element in information security meaning the information should be easily accessed and available whenever requested or desired by the authorized person. The company or
organization responsible for storing information should always be able to make the information available whenever required. For this, a secured backup system should be maintained so that data can be restored in times of emergency situation or some calamity.
Thus, all the three components of information should be monitored 24/7 in order to guarantee the security of the information (Jesan, 2006).
Compliance means a formal or informal agreement or acceptance of a certain rule, policy or system. Compliance in the field of security culture is divided into two different classes. One of the approaches discusses the use of sanctions where it focuses about penalties and pressures that is a coercive process of implementing compliance. This approach is closely linked to the deterrence theory where punishment is the solution to adhere people to policy. Another approach is more behavioural and holds belief that compliance and non-compliance are not alone associated wit sanction and expectance of rewards, rather it relies on value-driven organizational culture (Ella et al., 2013).
Although most of the organizations have been using security technologies for a long time, still the tools are sometimes not enough or insufficient. Therefore, the area of end-user security behavior and compliance has now gained a new momentum. This thesis will investigate employees’ compliance to information security systems and helps in modelling a good framework so that the sustained IS can be achieved (Herath and Rao, 2009).
1.1Aim and Scope of the thesis
The aim of this project is to investigate the trend of information security compliance of the employee in an organization and formulate the effective measure or model. There are many incidents that occur in present world about security non-compliance in an organization that poses a serious threat to company/
organization. Therefore, the focus of our research is to develop a model that clearly states that, “the compliance policies based on the positive traits and positive personal strength can help achieve a sustainable information security”. The aim of this research includes:
i) To examine the literature in information security.
ii) To review the IS problems in the organizations and possible solutions to it. iii) To investigate the compliance of security and the theories associated with it.
iv) To analyze the effect of positive psychology and employees’ strength in the organization and its subsequent effect on developing security policies.
v) To develop a solid conceptual model on security compliance based on positive traits and strength of an employee.
vi) To perform a comparative study of PP model (Positive Traits, Personal Strength) and the current existing security compliance models such as General Deterrence Theory (GDT), Protection
Motivation Theory (PMT), Job Demands-Resource (JDR) model and Rational Choice Theory (RCT) vii) To conclude the framework suggesting further works that can be expanded in the future.
The project will be based on analysing the protection motivation theory and theory of planned behavior analysing the hypothesis and assumptions. It will investigate the current work on the information security and points out the problems in the current theories or framework so that a completely new framework on security compliance can be developed. It will incorporate some widely used security frameworks and build a framework based on employees’ positive traits and personal strength(Ifinedo, 2012).
1.2Research approach or methodology
The research will analyse the current trend on information security and employees’ compliance towards it. It outlines the problems and limitations in the security compliance models that are discussed in the
literature and suggested by the research scholars. A comparative study of current security compliance models and theories will be performed so as to find a better security compliance model/framework that can be applied in the organizations for secured and sustained environment.
2. Background
The security compliant behavior is influenced by two factors, namely extrinsic (effect of penalties, social pressures) and intrinsic motivators (perceived value or contribution) (Herath and Rao, 2009). There are other factors such as upper management practices, co-worker socialization, information social climate and self-efficacy, which contribute to security compliance and influences behavior of the employees to a large extent (Mark et al., 2005). Beside these, the variables like deterrents, threat appraisal and normative belief guides the behaviour of the employees. All these factors give a clear overview of the employees’
perception of security compliance and reasons why employees’ often ignore security measures in the organization (Workman et al., 2008).
Compliance is equally based on ensuring end-user compliance towards security policies as well as its impact on the preventive software measures designed in an organization. This poses another significant issue related to security usability. Whitten and Tygar (1999) suggest that security software is usable if the target employees are:
• Aware of the their security related task in the organization.
• Efficient to solve the problems encountered and have the potential to do the task successfully.
organization.
• Comfortable with the security interface they are handling (Tygar and Alma, 2000).
Most of the organizations and companies value information system as one of their greatest asset. These systems are their most valuable organization resources. To protect these assets from misuse or abuse; organizations incorporates security measures like system backup, use of anti-virus, firewalls, encryption keys, monitoring systems, surge protectors, and so on. Therefore, Information security, also known as InfoSec has become a major concern in every organization. The failure and success of organization now depends on employees’ adherence/compliance to information security policies (Siponen et al., 2010). The research investigates whether the security policies built upon positive psychology that motivates the employees’ compliance practice on information security. It will be based on some solid behavioural theories and survey as well so that employees’ sustained security compliance can be further enhanced and help in developing positive organizational behavior (Siponen et al., 2010).
2.1 Theory of planned behavior
It is believed that an individual thoughts, feelings, behavior and action are the social influences that results when a person interactions with a group of other people or society. The theory of planned behavior gave rise to the theory of reasoned action (TRA) that suggests that behavior is the outcome of attitude, subjective norms and perceived behavioural control. The attitude refers to positive or negative thought of an individual while engaging in a particular circumstance. Subjective norms refer to idea that a person holds of about behavior that he/she conducts. And perceived behavioural control is the thought of individual to improve the behavior by the resources and efficacy one acquires. The Theory of Planned Behavior is often used to determine and analyse the organization’s ethical framework and the compliance behavior of the individual with regard to information system security (Sunil et al., 2008).
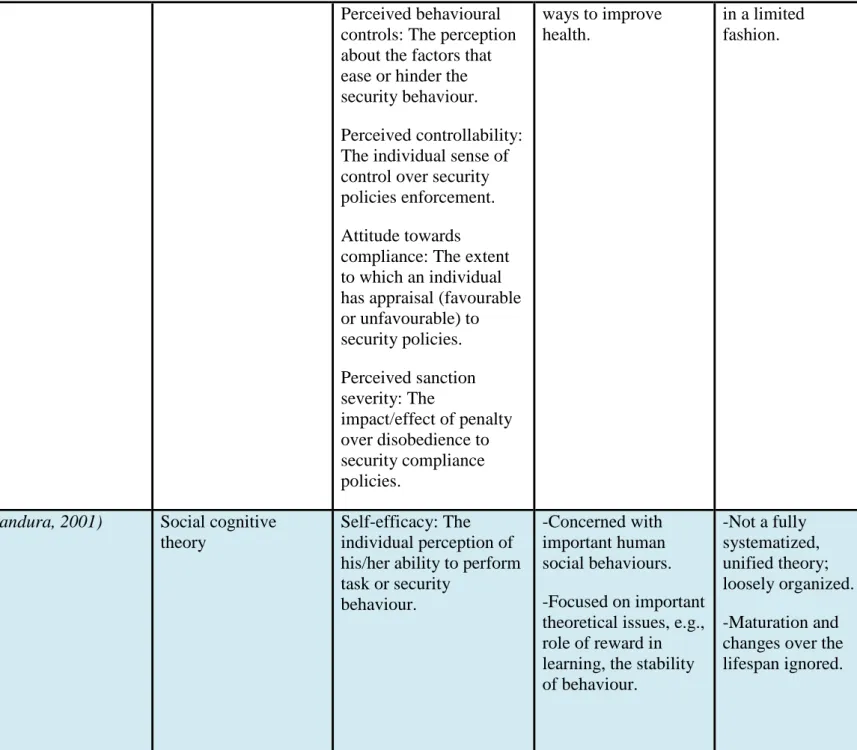
2.2 Social cognitive theory
The behavior of human is well explained by the theory of social cognitive theory (SCT). It makes the co-relation between the social aspect and personal life of an individual. SCT states that when the individual’s action is under control of his/her behavior, then there is a possibility of personal growth and development. SCT is categorised into two main factors, viz. locus and self-efficacy (Bandura, 1977).
Locus of control can be defined as degree to which the individual perceives in controlling the action that directly or indirectly impacts. If a person has full control on his/her action and belief to control the circumstances that occur eventually, they will have a sense of responsibility in everything that results from their doings. The individual who cannot bear responsibility has the habit of transferring responsibility to
others. Self-efficacy is defined as the belief a person holds in his abilities and resources. It determines the person’s strength in performing a specific task. Locus and self-efficacy are the effective measures to analyse the safety behavior of an individual (Ajzen, 2002).
2.3 Social bond theory
Social bond theory (SBT) defines the bond that an individual has with the society. According to Hirschi (1977), four different kinds of bond usually occur due to socialization, viz. attachment, commitment, involvement and personal norms. According to this theory, these bonds of socialization play an important role in reducing non-compliance or anti-social activities. Attachment refers to bond with society/organizational values. Commitment is the individual’s effort and hard work to promote the organization. Involvement is the act of developing intimacy with social groups. Personal norms are the thought and belief of an individual on the social setting he/she dwells. These bonds are essential to have in a person to contribute to the organizational mission (Hirschi, 1977).
3. Literature Review
Information security and compliance are the two inseparable elements in any organization that rely on the power of Information. One of the major threat to the information security is the employee themselves who take information just for granted. This leads to the security breaches that may damage the reputation, goodwill and organization as a whole. Therefore, it is the major concern of the organizations in today’s world to balance the equation between information security and employees compliance. In order to address this concern, there are multiple approaches to ensure IS security compliance that have been proposed. The information intensive organizations give utmost priority for securing information by using security technologies. Most of the research is mainly focused on the use of technology until now it’s been noticed that IS security cannot be achieved using the tools and technologies only. There are three components: people, process and technology which play a vital role in determining the security of IS.
According to a recent report on security breach, it says that organizations lose millions of dollars due to employee negligence and non-compliance (Herath and Rao, 2009). Another survey unveils the fact that 60% of IT managers of global companies said that employee misconduct in information system is a threat to InfoSec. The survey done by 2008 CSI Computer Crime and Security reflects another shocking fact that 44% of the respondent reported abuse of information by insider, just behind virus (49%) and other from external sources (Hu et al., 2011). These facts conclude that information security has been top priority and issue of major concern in any organization that is based on information. And employees are the weak
elements and a threat that can seriously deform the organizational security chain. Therefore, employees’ compliance with a positive psychology and behavior is today’s necessity to preserve the information in the organization.
The recent research focuses on the human perspective of handling security issues that entirely depends on the end-user, which is quite often referred to as an insider. An insider is the personnel who have the required privileges and authorities in the organization. But due to negligence, ignorance or deliberate intention, the insider pose a threat to information security (Lee et al., 2004). There is lot evidence that supports this fact. One of the survey done by the CSI/FBI reveals that about 64 per cent of the people who were surveyed that it is due to the action of insider the security is being compromised. This behavior of insider led to the concept of deterrence and sanction suggestion that the non-compliant behavior of the employees should be taken seriously and such violations should be treated with punishment so as to deter from such behavior (Straub and Nance, 1990).
The employees’ behavior should be analysed using the rational choice and the crime prevention strategies and the organizational policies should monitor the behavior of the employees so that the effective measures can be implied and change the decision-making ability of the employees. The deterrence and other social theories suggest that there exist the relation between organizational policy, information security and the awareness program and if social relation of people can be improved through organizational practices then information security can be achieved(Lee et al., 2004).
There is a huge difference in the implementation of strategies between information literature and
organizational literature. The information literature primarily focus on the use of sanction to avert the non-compliant behavior of the employee through punishment while the organizational literature targets the use of providing incentives to motivate the conduct of employees (Stajkovic and Luthans, 1997). Although the use of reward and punishment (extrinsic motivation) can work in some situations, intrinsic motivation should be always present in the employees’ so as to better comply with information security (Tyler and Blader, 2005).
The two popular theories on employees’ security compliance are the Theory of Planned Behavior (TPB) and the Protection Motivation Theory (PMT). Protection motivation theory developed by Rogers expands the health-related model in the domain of social psychology and health (Ifinedo, 2012). This theory has been successfully used in the areas like disease prevention, health promotion, politics and environmental protection since 30 years. This theory constitutes two major concepts, threat appraisal and the coping appraisal. Threat appraisal refers to perceived vulnerability and perceived severity. Perceived vulnerability refers to the probability that a negative event will take place if no one takes measure to prevent it.
The coping appraisal holds the view of how the individual assess his or her ability to cope and avert from the potential loss or damage that arises from the occurring threat. Coping appraisal has three main
elements:
a. Self-efficacy: It highlights the ability or judgment of an individual using his abilities and
capabilities to adjust or cope with a certain behavior. With regard to our research, it can be referred as skills, abilities and measures taken to protect InfoSec assets and organization as a whole.
b. Response efficacy: This factor holds the notion about benefits of the action taken by the employee.
Here, it refers the security compliance as a good mechanism to detect a threat.
c. Response cost: It emphasizes on the opportunity cost like money, time and effort used in using the
recommended behavior (Ifinedo, 2012).
Ajzen proposed theory of Planned Behavior (TPB) in 1991 suggesting that the individual behavior is highly influenced by elements such as attitude, subjective norms and perceived behavioural control. The three constituents of TPB are:
i. Attitude: It refers to the positive or negative feelings towards engagement in a specific behavior.
In our context, this implies attitude towards compliance with information system security.
ii. Subjective norms: It is the person’s thought or perception of what people important to them
really think about them given a certain behavior.
iii. Perceived behavioral control: it is the perceived ease or difficulty while performing a specific
behavior.
TPB is regarded as one of the most predictive persuasion theory and is used to investigate information system ethical behaviors and individual’s decision that can be used in developing effective security measures and compliance (Ifinedo, 2012).
In the age where technological advancement and information system are booming at an alarming rate, organizations either small or big face some threat and potential damage in their workplace. Organizations are motivated towards safeguarding information and data resources that are their biggest assets. They use tools and measures like anti-virus installation, updating firewalls, maintaining and restricting access controls, monitoring systems, using surge protectors, encryption technology and so on. This approach however may provide technological protection, but the global question is: Is the technology alone can guarantee the security of information? The question poses the fact that there is some other aspect we need to consider as well to maintain a sustainable culture of security. This ultimately and indirectly refers to the employee who is considered a weak as well as strength in the corporate IT companies and organizations. These views are already accepted by the leading researchers like Vroom and von Solms (2004) and Pahnila
et al. (2007) and they posit the view that organization that pay attention to both technical and non-technical aspects to protect their IT assets are more successful in safeguarding the information repository in the organization.
Information security, often called InfoSec, is the biggest concern in any business house or organization. But, often employees are considered as a weakest link in safeguarding the information rather than strength. This implies there are some loopholes that need to be adjusted before it’s too late. The recent research based on human behavioural theories has come up with two important recommendations: implement security policies and procedures and conduct thorough awareness trainings to the employees and make a way to clear the threat posed by employees by employees themselves (Hu et al., 2011). Here, comes the idea of positive psychology in security compliance that can be the solution to this crippling problem that has plagued the organizations for years.
Behavior of the employee in security policy compliance is another aspect to look upon while dealing with information security. Almost every organization has now started developing some policies to determine the behavioural action of an employee so as to conform/stick to the compliance policy. Although the clear and solid policies are implemented, the results are not as expected as it ought to be in the field of information security. The research and surveys in the past that suggests that employees seldom comply or adhere to the policies of information security. Moreover, there are researches ongoing in behavioural information
security that investigates the employee intentions in security compliance. In organizational context, there is a theory called Agency theory or principal agent paradigm that deals with influencing the behavior of the employee. This theory applies to different domains where there is asymmetry in information, fear of opportunism and where there is bounded rationality (Herath and Rao, 2009).
4. Positive Psychology
Positive psychology is the branch of science that deals with the positive attributes of human being to make life more fulfilled with satisfaction and positivity through happiness. It is oriented towards wellbeing, happiness, creativity and personal strength of an individual and group. It focuses on the belief that well-being in an individual will have positive effect on the group he/she dwells thereby creating a win-win atmosphere (Hefferon and Boniwell, 2011). Nowadays, it has applications in many areas of human
research that are targeted to improve the thinking pattern of people so that they can be more productive and satisfied with their work. Positive psychology itself is a vast domain which is not only limited in clinical area, but it is gaining popularity in many areas where positive attitude and thinking plays a vital role. Positive psychology is the youngest branch of psychology till date. Its main aim is to help human beings lead healthy and happy life. According to many surveys done in the past, positive psychology has been
mainly divided into three orientation of happiness: pleasant life, engaged life and meaningful life. Researches have proved that people obtaining low scores in all the categories are not satisfied with their life and are not motivated towards happiness whereas the people who have a positive perspective on all these three aspects are positively oriented towards life. This concludes that a positive psychology will have a substantial impact on people’s life (Carr, 2011).
The history suggests that for almost half of the century, Psychologists have researched in psychopathology focusing on the negative side rather than positive side of life. Before World War II, the psychology was targeted in three areas: a. cure mental disorders b. promotes the lives of the general public and c. study highly intelligent people. The war ended but no one actually bothered to observe the soldiers who were psychologically impaired due to the effect of violence and brutal killings. The funding was provided to research in the first area, that is, treatment of mental illness which led to the assumption that human are passive beings (Hefferon and Boniwell, 2011). But scientific or clinical research has now changed its course to a new science of psychology called Positive Psychology. Before the emergence of Positive Psychology, the psychologists Abraham Maslow, Carl Rogers, Erich Fromm formulated the principles and theories of human happiness. These theories have led to the evolution of positive psychology due to correlation between happiness and positive emotions. Martin Seligman in 1998 suggested about “Positive
Psychology” although the term was first used by Maslow in his book Motivation and Personality in 1959.
The history of positive psychology dates back to great philosophies and ideas posed by the philosophers as shown in the table below.
Theory Founder/Contributor Idea
Theory of morality, virtue and good life
Aristotle Highest good for all humanity
is happiness Utilitarian philosophy
(greatest happiness principle)
Jeremy Bentham, John Stuart Mill
Happiness can be measured by assessing the quantity of experienced happiness
Emotion William James Emotions come after we have
physically acted out Humanistic psychology (late
1950s and early 1960s)
Abraham Maslow Focus on mental health
specifically positive attributes such as happiness,
contentment, ecstasy, kindness, and so on.
Table 1 History of Psychology
As there are many disciplines in psychology, it is quite difficult to spot where actually positive psychology really fits in. The figure below shows the place of positive psychology within other disciplines (Hefferon and Boniwell, 2011).
Figure 1 Positive Psychology in relation to other Psychology (Hefferon and Boniwell, 2011)
Positive Psychology is linked with the organizational behavior of an employee. Jane Henry in 2004 put forward several practices in which the role of positive psychology can be seen clearly. Some of the practices are:
a. Job variety: employers should offer multiple opportunity and job variety to engage the employee.
b. Intrinsic motivation: Intrinsic motivation of an employee should be enhanced through flexible
working schedule, providing meeting and social gatherings and developing their competitiveness through trainings.
d. Creativity: positive organization should encourage creative thinking in work.
e. Strengths work: focus on strength of the worker rather than their weakness.
f. Team building: constant endeavor to build networks among team members.
g. Meta-perspective: a balanced perspective (positive or negative) should be maintained by positive
organization (Hefferon and Boniwell, 2011).
The role of positive psychology helps in shaping the nature of work and workplace environment. There are researches to develop employment relations, which focus mainly on topics like stress, workplace violence, job insecurity, etc. It is a good topic to research that will investigate on the problems in workplace so as to find a good solution. At the same time, more study should be done to improve and develop positive energy in workplace and employees to achieve the objective. The challenges faced by the employee and the employers will reflect the organization internal work atmosphere. As the way and methods of business and the organization structure is changing day by day, there should be some good way based on positive psychology to motivate everyone in the organization(Turner et al., 2002).
5. Relation between personal strength and security compliance
The two most widely used theories in the field of security compliance are theory of planned behavior
(TPB) and the protection motivation theory. Both emphasize on one common element called self-efficacy.
Self-efficacy is the individual ability to perform a particular task using his personal strengths like knowledge, experience and expertise to cope with a certain task. For the employees to follow a certain compliance rule or policies, self-efficacy plays an important role. As an instance, let us assume an employee wants to send a confidential mail as a part of his task. If he/she has the knowledge in using encryption tools he would obviously send encrypting the mail and therefore stick to the security of the company which suggests self-efficacy as a major strength an employee should possess(Siponen et al., 2010). Providing training can strengthen self-efficacy and education to the employees and the security measures and policies should be clear and defined by the managers and the IT staffs and should be reviewed from time to time.
The true security of information lies in the behavior of end user. The social cognitive theory explores the use of self-efficacy in determining the security of the organization (Rhee et al., 2009). Self-efficacy is the self-determination and evaluation of one’s ability and skills to mobilize the resources like motivation, experiences and cognitive resources to achieve a task. It is a resource to cope in an adverse situation and is really beneficial to have with the people who are employed in the sectors of information.
Computer self-efficacy (CSE) is a term derived from self-efficacy so that it can be more specifically related to information and technology (Rhee et al., 2009). CSE is the person’s expertise in using the computer and its resources. It can be used to investigate the behavior of end user like learning system, implementation of security policies, following organizations’ compliance standards and legitimate use of information. Some of the popular hypotheses in the area of self-efficacy and the individual behavioural aspect to protect information system are as follows:
According to the social cognitive theory, self-efficacy plays an important role in determining behavioural control in times of threatening circumstances. This means that people having a strong SE can find solution to the problems using his/her resources (Bandura and Jourden, 1991). While those with less SE (i.e. less knowledge and resources) have low coping tendency. In the organisational setting people having high SE suggests that they would use more secure software protection systems and act with recommended
conscious behavior of an organization. Thus, the proposition follows: 1a. Employee with high level of SE will use more secured software. 1b. Employee with high SE has high level of consciousness in security.
Self-efficacy is also related to motivation and how much conscious people are about their task. People having high SE gets involved in various task with great coping skills to solve the problems that ultimately leads to mastery of skills. According to (Zhang and Espinoza, 1998), people having a stronger sense of SE showed greater desire/intention in taking computer courses to improve their skills. Therefore it is believed that:
2. Employee with high SE shows strong determination and effort to safeguard information.
Social cognitive theory states that experience is the source of efficacy. Mastery of skills is the result of multiple past experience in a certain job that an individual get involved in. when a person is familiar with the computing skills and has prior experience, this will result in empowering his SE. while person with skills can encounter bad experiences like computer fraud and virus-related incident which lowers his/her own judgement or capability. Thus there are two assumptions regard to experience and security incidents. They are:
3a. SE is directly related to experience.
3b. Incidents in security will have negative effect on SE and will lower it.
Apart from past experience, one of the factors that influences self-efficacy is belief. The perceived belief of controllability fosters search of control mechanism. There are two ways of exercising control. One of the way involves use of efficacy to effect change by effort and this is a control that can be initiated at personal level. Another way is about control of problems and it refers to constraints and opportunities to which personal efficacy can be used to tackle problems. Thus it is concluded that:
4. Belief in controlling threats empowers SE.
Figure 2 Self-efficacy in information technology (Rhee et al., 2009)
According to the theory of planned behavior, the employee behavior and action are deeply influenced by the variables like attitude, subjective norms and perceived behavioural control and these variables can provide an insight on individual behavior (Ifinedo, 2012). This can lead in forming sustained information security measures and policies.
Some of the hypotheses made in the security compliance and employees’ behavioural intentions are as follows:
a. Subjective norm has positive impact on employees’ intention to comply.
Subjective norms are the beliefs to conform to an act or policy that is formed on the basis of
observation of the environment we live. The environment they work influences employee behavior. People they work with like co-staffs and managers and how they follow the compliance rules and policies motivate their actions. Thus, subjective norms have positive impact on employee
behavioral intention.
b. Attitude has positive impact on employees’ intention to comply.
If the employee has positive attitude towards security compliance in an organization then the behavioral aspect of employee will be positive as well and vice-versa. So attitude towards security has positive effect on behavioral intention.
Self-efficacy is related to the ability and strength of the employee. The employee with high self-efficacy will comply with the rules and policies and use the resources to improve the security. Self-efficacy has a positive effect on employee behavioral intention (Ifinedo, 2012).
d. Response cost has negative impact on employees’ intention to comply.
Response cost can be anything negative resulted from employee behavior like expenses, problems related to time, etc. there is a tendency of an employee that if a considerable amount of resource (like time and money) has to be used for certain work, employees do not show interest in following guidelines or security compliance. While, if less resource is needed, they will comply. This
suggests that if response cost is reduced, employees’ likeliness to comply with IS measures will increase. Thus, response cost has negative impact on security compliance and employees’ behavior towards it.
e. Response efficacy has positive impact on employees’ intention to comply.
If the employee has the knowledge and skills regarding the coping mechanism and the effectiveness to stay away from the threat or danger, then he/she will follow the adaptive behavior. While if an employee has no knowledge or confidence in the effectiveness of the measure then he/she will blindly accept the consequence. So, when an employee believes in the organizational information security and its measures to prevent threat, it develops a willingness to comply with it.
f. Perceived severity has positive impact on employees’ intention to comply.
As a human we normally adjust our behavior with respect to the situation we face. Similarly, if an employee perceives an information security threat in his organization, then he/she will abide by the rules and compliance policies. While if an employee does not perceive threat, he will be not be concerned in compliance and the policies of the organization.
g. Perceived vulnerability has positive impact on employees’ intention to comply.
If the employee finds that the security of the organization is highly vulnerable to threat, then the employee has the intention to strictly comply with security measures. Whereas, if an employee holds the view that the organization is invulnerable to security threat will not comply with security policies and measures.
6. Self-efficacy
Numerous researches have been conducted in the field of cognitive science, which has tremendous impact on the human behavior and action. One of the most discussed and supported cognitive elements is self-efficacy. Self-efficacy is defined as the individual judgment of personal strength in dealing with the certain situation and how well the situation is coped and dealt using the knowledge(Stajkovic and Luthans, 1998). Empirical research on the relation of self-efficacy and behavior and motivation of human has demonstrated the fact that self-efficacy has positive impact on the behavior of human work tendency and is applied in clinical, educational and organizational domain. According to Bandura (1982), “Self-percept’s of efficacy influence thought patterns, actions, and emotional arousal”. Self-efficacy has been an important attribute in organizational setting. High level of perceived self-efficacy will result in high work performance(Bandura, 1982). Psychologists hold the view that self-efficacy is the perception of one’s ability to undertake a given task at a certain condition. The social cognitive theory of Bandura strongly demonstrates the tremendous ability that self-efficacy can place in person’s way of thinking and action. The theory clearly posits the idea that personality is developed through observation of environment and learning from it and social
experience we gain. Accordingly, self-efficacy is developed and acquired through constant effort. People with high self-efficacy solve the problem in a positive prospectus and master them rather falling back. In contrast, people with low self-efficacy face the problem with less confidence and retreat from it (Sousa et al., 2012). Hence, people with high self-efficacy have more commitment, resources required to tackle with problems and skilful which is very beneficial for organization that deals with information and security of data.
7. Knowledge Management and Expertise
Nowadays the organizations face many challenges and hurdles due to new technological innovations, growing customer needs and diversified market needs. The companies need to focus on the employee personal growth and knowledge base to continuously improve the learning process to compete in the global market. So, there should be a continuous endeavour to promote the generation and sharing of knowledge within the organizational community and the networks within them. Sharing expertise is beneficial to organization in many ways like:
a. To improve the learning process in organization and organizational enhancement through learning
experience.
b. To solve time-critical problems in the organizations.
d. To develop the social capital like trust, shared norms and reciprocity within and beyond organization(Wulf and Ackerman, 2003).
In an organization, knowledge management is a top priority task rather than just a need. It is a crucial part of the organization that is to be given attention and effort to balance the organizational advancement in scale. Knowledge management is the process of managing the intellectual property to effectively store, retrieve and manage the every bit of information. In general, there are two ways of knowledge management in technological domain. The first way is to place the knowledge in external source, which means placing the information, and data in shared repositories or database. Using this method, information can be easily transferred and reused as it uses some computational technique but it has some limitations and not easy to use often. This is regarded as a traditional approach in knowledge management. The second way of knowledge management is called expertise sharing. As the traditional approach does not fulfil solving the problems related to tacit knowledge, use of expertise sharing is strongly felt. Expertise sharing is using the intellectual resource of the employee using the expertise networks. As expertise sharing is related to cognitive, social, psychological and organizational aspects of human and use of technology as well, it is considered as an effective way of knowledge management over traditional method(Wulf and Ackerman, 2003).
Although many companies and organizations that value their information expend lot of efforts and money in knowledge management and expertise, they do not gain much success compared to tireless effort. A survey done by Ernst and Young on 431 US and European companies deduced the fact that only 13 per cent of the respondents believe that they actually share the knowledge within the organization
effectively(Wulf and Ackerman, 2003). This survey posits that there are some loopholes and limitations that hinder the effective dissemination and harnessing of knowledge and expertise sharing. There are many limitations to obstruct the knowledge and expertise sharing, but if we are to mention the major limitations, we can focus on the issues of cognitive and motivational limitations.
a. Cognitive aspect: It is the limitation in expertise sharing which holds the view that regardless of experts’ motivation, the way they represent, store and process the knowledge can be obstruction in expertise sharing. The experts mentally represent and store the knowledge and as their expertise sharpens, it becomes more abstract. The skillful expert will solve the problem indulging them in the root and conceptual base of the task whereas the less skillful expert will try to hit-and-trial the problem making the problem more problematic and time consuming(Wulf and Ackerman, 2003). The skillful experts usually build the abstract representation of knowledge and simplify it using
their expertise. Their representation mechanism may hinder the sharing of expertise as people with less expertise and knowledge may fail to retrieve the knowledge shared by them.
b. Motivational aspect: Motivational limitation is another factor that will block the knowledge and expertise sharing. The problems like competition as a disincentive will contribute to the
motivational limitation(Wulf and Ackerman, 2003). The motivational problem, indeed, rise from the internal structure and operating environment of every company/organization. The organization has the tradition of placing the competition between various groups or individual in the expectation of increasing job efficiency. Some of the examples to set the employee in so-called race of
competency are rewards, promotion, incentives, etc. although this can internally motivate the individual to achieve better than other, it can restrict the sharing of knowledge and expertise with the individual of less expertise. One person’s reward can be another person’s failure which is often called sum-zero game(Wulf and Ackerman, 2003). Therefore, motivational limitation is a big setback in expertise sharing.
8. IS Security Knowledge Management
Knowledge management in information system is a crucial part in any organization because it the hub of security. The security of the information is usually handled by use of sophisticated technology but technology alone is insufficient to safeguard the information because human is the driving factor in operation of the security. The human factor poses a real threat and a subject to consider greatly in securing the information.
The information security knowledge management depends on the knowledge creation mechanism. The creation of knowledge is still an ad-hoc process in the organization. Knowledge creation takes place in the organization through expert hired from other organizations or the experts within the
company(Belsis et al., 2005). Either way, the security of the company falls in jeopardy of security threat. The knowledge creation theory developed by Nonaka and Takeuchi in 1995 states that, “human knowledge is built and developed through social interaction of tacit and explicit knowledge”. This process of interaction gives rise to Knowledge Creation. The interaction of tacit and explicit knowledge can take place in four different ways. They are:
a. Socialization: People meet, communicate and exchange the knowledge in different social setting
like seminar, workplace, and job training workshops, etc. where the actual exchange of knowledge can occur. The exchange of tacit knowledge can happen when a person closely works with skilled person or through observation.
b. Externalization: Here the conversion of tacit knowledge to explicit takes place through analogies and metaphor models.
c. Combination: the combination process takes place through meeting and documents, presentation,
workshops where the knowledge combines and becomes more structured.
d. Internalization: The explicit knowledge becomes tacit in internalization process. When a person
expresses his/her views and thoughts in a particular area, internally the knowledge will expand on the subject over time and the doubts on subject matter slowly fades away clearing the confusion between theoretical knowledge and experience (Belsis et al., 2005).
According to Nonka, these four processes form a spiral model of knowledge transformation forming a continuous cycle as shown in the figure below.
Figure 3 Spiral of Organizational Knowledge Creation (Nonaka, 1994)
The theories and ideas of positive organizational scholarship (POS) are used in development and implementation of effective organizational strategies.
POS provides an insight to understand the relation of organizational strategy and its employees’, its impact on human behaviour on workplace and subsequently provides a vision to analyse why some strategy are more productive than the rest (Cameron et al., 2003). The role of positive psychology in improving positive organizational behaviour is undebatable and has gained more popularity in the recent time (Seligman et al., 2005). Nowadays the companies or organizations direct their strategies to increase positive traits or
attributes (e.g. trustworthiness, loyalty, resilience) in employees’ to achieve their business goals and maintain sustainability (Fryer, 2004). Since positive psychology focuses on human strengths like positive traits and personal strength for organizational prosperity, it is believed to create positive impact to develop organized system that values potential in their employees’(Peterson and Spiker, 2005).
Positive organizational behaviour is defined as the study and application of positive human strengths and psychological capacities for a healthy organizational environment (Luthans, 2002). According to Luthans (2002), there exists a never-ending relationship between work and happiness; positive organizational culture and its performance; and employees’ attributes and their performance. Therefore, an assurance of employees’ feelings such as happiness, gratification and satisfaction can help in achieving organizational strategy.
Positive psychology is the science of improving quality of life through comprehensive study of positive experiences of an individual, positive traits and positive organizational culture (Seligman and
Csikszentmihalyi, 2000). The success of organization depends on many factors. Among them, employees’ behaviour; their traits such as creativity, innovation, commitment; and personal strengths of an employee tremendously influences the potential of the workforce. The organizations should be aware that
understanding and application of positive organizational behaviour in the work environment with a clear thought of employees’ positive traits and strength will help to succeed in the organizational venture in the long run.
The history suggests that the research in the past were more directed to the negative side of organizational behaviour such as violence in the workplace, organizational failures, and like (Cameron et al., 2003). While the organizational behaviour was more interested in the concepts like uncertainty management, disorganization theory and chaos theory; POB put forward the concept of positive aspect of work; positive traits of employee and their interdependency which contributes equally in the development of good work environment.
Based on the fact that POB applies in the organizational setting with a positive outcome and succeeded in realizing the positive employees’ traits to maximum for a better organizational career, we suggest that the employees’ security compliance behaviour can be improved through positive organizational behaviour. If the organization embraces the positive traits and strengths of an employee and develop a organizational culture and security compliance policies’, a better security compliance can be achieved.
10. Research Framework
10.1 Conceptual Model
Information security is often observed from the view of the behavior of the employees and the technologies implemented by the organization. This alone cannot assure the security of the organization completely. Besides, there are other factors responsible for the effectiveness of information security culture. They are top management action, employees’ psychology (positive traits) and social background of the employee. According to the Theory of Planned Behavior, the individual behavior is influenced by the belief system he/she holds and the security of the organization relies on it. Apart from the individual behavior, top management policies and organization culture also determines the compliance to security in the organization (Hu et al., 2012).
The relation between management of the organization (policies), employees’ strength (positive traits and personal strength) and policy compliance is shown in the figure below:
Figure 4 Conceptual model of security compliance
This model helps to analyse the fact why does some employee follow the policies and rules of the organization and some don’t and why some employee has greater sense of responsibility and is more accountable. The top management level of the organization comprises of the policies, standards, rules and regulations, compliance criteria, etc., which form the basis for organizational culture. The managerial efforts and the organizational culture help in shaping the behavior and their belief system which is very essential for sustainable development of the organization which in turn will create positive intention to comply with the policies.
10.2 Top management and Organizational Policies
Top management influences the behavior of the employee and their intention to comply with the
security policies. There are three mechanisms through which top management can significantly change the employees’ attitude towards security compliance (Hu et al., 2012). They are:
a. Legitimacy mechanism: By initiating solid policies, plans and programs having clear strategy,
vision and goal; top management provides legitimacy to their plans and policies. Top management participation helps in delivering the legitimacy of the plans and policies to the managers and employee in the organization. Therefore, legitimacy can encourage the employee to comply with the rules and policies.
b. Commitment: If the top-level management of the organization shows the commitment towards its goal, strategy, planning, policies and its implementation; it sends a positive signal for the employee working in an organization and can establish accountability and commitment in their work.
c. Fairness and justice mechanism: This mechanism is based on the psychology of human behavior
which suggests that, the organization which operates with fairness and justice will stimulate
positive attitudes in an employee mind about the organization. Top management participation in the organizational policy and plan will provide freedom to express idea and opinion, design unbiased and fair policies and implement better organizational procedure, rules and policies (Hu et al., 2012).
The employee behavior towards information security is based in the action and communication of top management. Educating the employee about the roles and responsibilities regarding security is one of the crucial task of the management body. The organization should be able to present a well-defined policies and communication regarding security like educating through security awareness campaign, training, seminars and reminders which help in increasing responsibility and judgment in employee, thereby enabling proactive actions in regard to security of the organization. The management can enforce policies to monitor the employees’ daily internet-usage, track the network activities and implement auto-security verification and validation programs to avoid security breaches. Computer monitoring (COM), therefore, can be a useful tool in improving the security culture within the organization(D'Arcy and Greene, 2014). Thus, strong security culture of the management can enhance positive commitment in security compliance. Hence, a hypothesis can be proposed as:
H1. Good management policies and security culture increases employees’ intention to comply.
The role of top management is felt strong when implementing the rules and policies regarding compliance. Top management should implement the policies to strengthen the employees’ strength. As we know the organizational policy has a direct influence with the employees’ strength (positive traits and personal strength), the policies should encourage and stimulate positivity in the employees’ behavior towards compliance. The positive psychology, positive traits and personal strength (e.g. expertise, experience, knowledge) are the strength of the employee in any organization. If the policy can be made incorporating the employees’ strength, then we can completely change the way employee compliance is usually looked upon.
10.3 Personal Strength and Positive Traits: Strength determines the consequence of the situation. The conscientious person with a strong personality is more careful in work than the conscientious person with a
weak personality(Dalal et al., 2015). The employee having a strong personal strength is more likely to
implemented considering the personal strength of an employee positively influence the compliance behavior. Knowledge, expertise, self-efficacy, experience and positive organizational behavior of an employee are the positive trait of an employee in an organization. Top management policies incorporating the positive trait while formulating security policies can serve as a catalyst in compliance intention of an employee. Conversely, if the policies are built without considering the employees’ positive traits and personal strength, then employees’ fail to comply with the organizational policies. So, we propose a hypothesis as:
H2: Employees intention to comply increases if the organizational policies are based on employees’ positive traits and personal strength.
Moreover, the organization policy can be implemented in two different ways so that better compliance can be achieved. One of the methods is to formulate the policies and plans to positively engage the employee. Here we are referring the employee with more experience, more expertise and more knowledge and high self-efficacy. The policies made by the organization can serve as a motivation to achieve productivity and better work life. Hence, we posit a hypothesis:
H3. Organizational policies designed to positively engage the employees’ increases security policy compliance in the organization.
Another method is to implement the policies to make the employees’ comply with the compliance policy of the organization. Here we are pointing to the employees’ who are less experienced, has less expertise and has low self-efficacy and the policies of the top management should serve as a guideline for the employees’ to achieve better performance in the work place. Thus, compliance can be achieved in the organization with good organization policies and employees’ strength. So, a hypothesis is being proposed as:
H4. Organizational policies designed to induce the employee intention to comply and based on personal strength of an employee will increase security policy compliance.
Based on the employee qualities i.e. positive traits and personal strength, the organizational policies can be developed to make the employee comfortable with the policies. The employees’ qualities like self-efficacy, knowledge, expertise, positive traits; cognitive qualities and personal strength should be well understood before implementing organizational policies. If these qualities are well analysed, then the organization can develop effective plan and policies that can internally motivate and empower the behavior of the employee. Thus, we propose a hypothesis:
H5. If the employees’ qualities are well addressed while implementing organizational policies, then positive employee compliance can be achieved.
Likewise, organizational policy is directly related to security policy compliance because only good
organizational policy can assure the development of better security policy compliance. The policies should educate, train, motivate and psychologically influence the employee concept on the security. The
organizational policies should make the employee feel that the policies are not a restriction, instead a path to successful organizational career. Thus, we propose a hypothesis:
H6: Better organizational policies helps to achieve better security policy compliance.
We concluded in H2a and H2b that intention to comply with the policies varies with the organizational policies and it may either increase or decrease the compliance based on how organizational policy is addressed with employee qualities like positive traits and personal strength. The employee qualities form the basis for developing security policy. For an example: let us assume a company X has employees with poor skills, knowledge, expertise and personal strength while a company Y has better employees in terms of positive traits and personal strength. In both the scenario the security policies should be developed for compliance but in the company Y, better security policies could be developed and the employees can be more comfortable with the policies. Thus, we posit a hypothesis:
H7: Employees’ qualities like positive traits and personal strength induce the organization to form better security policy compliance.
Other factor which affects the security compliance behavior of the employee in the organization are discussed below:
10.4 Individual Cognition
Employee compliance behavior to the policy of the organization is well demonstrated in the Theory of Planned Behavior proposed by Ajzen in 2005. According to the Theory of Planned Behaviour, employees’ behavior is driven by the intention to carry out his/her interest. Intention influences the personal behavior and motivation of a person (Ajzen, 2005). As TPB framework suggests, intention is affected by three factors:
a. Attitude towards the behavior (ATB): It refers to the employee attitude to determine whether the
task to perform is good or bad.
b. Subjective norm (SN): It refers to the impact of the social circles on the behavioral aspect of the
employee.
c. Perceived Behavioral Control (PBC): It refers to the level of ease or difficulty to perform a
behavior and awareness of the resources to achieve it.
There are numerous studies carried out on information security (e.g., Taylor & Todd 1995; Ajzen, 2005) regarding individual behavior that supports the TPB framework and the factors influencing the employees’
tendencies to comply. Some of the logical deductions made by the TPB in the information security of the organization are:
i. If there is a strong positive attitude towards compliance, the intention to comply will be stronger
as well.
ii. If there is a strong subjective norm towards compliance, the intention to comply will be stronger
as well.
iii. If there is a strong perceived behavioral control, the intention to comply will be stronger (Hu et
al., 2012).
10.5 Organizational culture
Culture is an important element of organization as it drives the organizational action and strategy. The articles in corporate security strongly suggest that security is not a technological issue alone; instead it is a management issue. The organization security culture has a direct influence in security practices, Therefore owning a security product does not solve the security issues in the organization (von Solms and von Solms, 2004). The culture is in many ways like an “operating system” of an organization since it helps to guide employees’ thoughts, actions and feelings (Hagberg and Heifetz, 1997). The practices and system by which the organization operate helps to define the culture paradigm of the organization (David and Fifield, 1999). Since the employees have the tendency to resist the change and new methods, organization face problems while introducing and implementing new technology, business processes and change in management (Cooper, 2000, David and Fifield, 1999). The implementation of new security policies and policy-based security plan often clash with the employees’ work ethos and experience they have practiced for years. The trait of organizational culture, therefore, is an important aspect of successful organization to ensure information security; and since culture fosters shared values, norms and beliefs, there is a need of balance between organizational culture and management of information security.
For the quantitative study of organizational culture and its impact on the behavior of the employee, the Quinn’s (1988) value-based organizational culture framework is widely used. Quinn’s framework focuses on the four cultural value orientations. In the context of our research, we will use Van Muijen et al.’s (1999) model, which is the adaption of Quinn’s (1988) original CVF (Competing Value Framework). According to this model, there are four basic values in the organizational culture. They are: 1. Support orientation- it refers to the support gained through group work and team co-operation for individual growth. 2. Innovation orientation- it refers to the creative and open environment of the
organization that helps to boost the work productivity of an employee. 3. Goal orientation-refers to the process motivated towards accomplishment of a task and focus on the priority of a job and
accountability in the organization and 4. Rule orientation- refers to overall rules and regulation, structure, formal communication and authority in the organization that influences the behavior of the employee. These values form the four quadrants with two opposing orientation poles (flexibility versus control and external versus internal)(van Muijen et al., 1999).
In our research we would be investigating the two values of the organization culture i.e. goal
orientation and rule orientation since it has more importance in the context of security compliance and policies and security compliance behavior is primarily targeted to make the individual comply the rules rather than dealing with the creativity and support. According to the study suggested by Chang and Lin (2007), value related to control has more influence in the security compliance environment.
Goal orientation in the organization culture reflects the collective organizational goal, responsibility and accountability of the employee. Goal oriented employee are more motivated towards a given task, seek challenges and shows competency in the job provided. Goal orientation helps in developing good attitude, subjective norm and self-efficacy while following the compliance and policies of the
organization and this leads to propositions like:
i. Strong goal orientation in organizational culture will stimulate strong positive attitude in
security compliance.
ii. Strong goal orientation in organizational culture will stimulate strong subjective norms in
security compliance and
iii. Strong goal orientation in organizational culture will stimulate strong perceived behavioral
control in security compliance.
Similarly culture of rule orientation has similar propositions in regard to compliance of the policies and rules of the organization. Rule orientation is related to the authority and compliance. It assumes that with a strong rule orientation through effective designed security policies and training of employees, the organizational stability can be achieved. It suggests that with the clearly stated rules and policies, compliance can be better achieved. Like goal orientation, rule orientation has similar propositions:
i. Strong rule orientation in organizational culture will stimulate strong positive attitude in
security compliance.
ii. Strong rule orientation in organizational culture will stimulate strong subjective norms in