Securing DNA Information through Public Key Cryptography
Full text
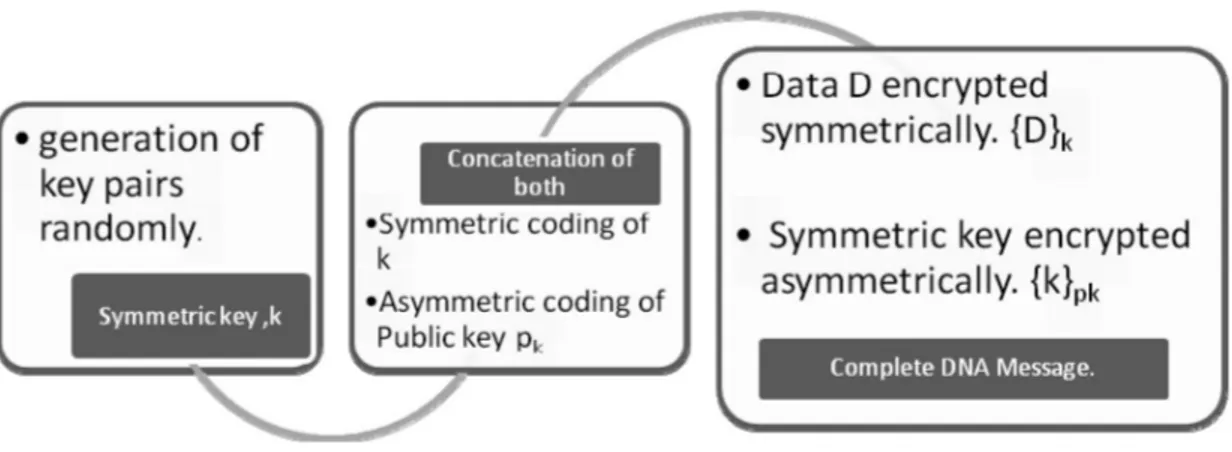
Figure



Related documents
This study determined whether there was a significant relationship between teacher effect data in middle school mathematics and a teachers years of experience and whether there was
Figure 3 Odds ratios with 95% CIs for 2-year infant survival without neurological impairment for a longitudinal decrease in fetal heart rate (FHR) short-term variation (STV)
MAP: Milk Allergy in Primary Care; CMA: cow’s milk allergy; UK: United Kingdom; US: United States; EAACI: European Academy of Allergy, Asthma and Clinical Immunology; NICE:
Field experiments were conducted at Ebonyi State University Research Farm during 2009 and 2010 farming seasons to evaluate the effect of intercropping maize with
sensitivity to attentional load as demonstrated by larger visual N1 to picture onset for high- than low-complexity images, (2) reduced emotional processing of unpleasant compared
To evaluate the potential relationship between volume expansion and analgesic efficacy following surgical site infil- tration with liposome bupivacaine in humans, we analyzed
– Assess inbound travellers with fever or other symptoms of the infection at border control points (BCP). – Refer suspected cases of MERS to HA for further