Research on Security Architecture in Mobile Cloud Computing to Prevent Adaptive Anomaly Attacks
Full text
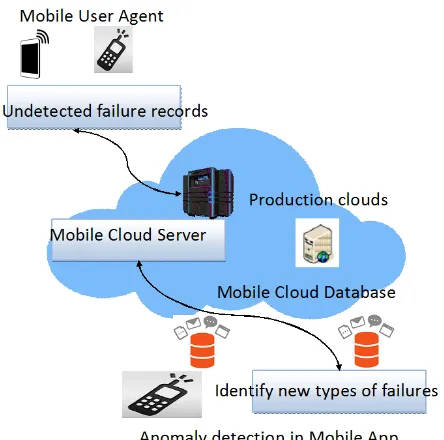
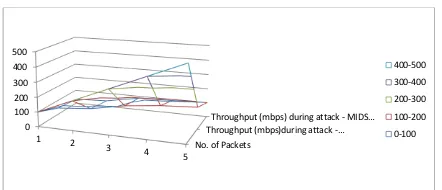
Figure
Related documents
Department of Justice’s Office of Juvenile Justice and Delinquency Prevention (OJJDP) and functions as a clearinghouse and resource center for collecting and distributing
However, the benefits of e-governance practice as identified by Yusuf (2006) such as cost effectiveness in government and public operations and significant savings
For example the machines that simulate 2-tag or bi-tag systems leave ‘garbage’ data on the tape, because of this they use space that is linear in the time of the simulated
Accessible Social Security Numbers are also critical to preventing, detecting, and remedying identity theft, yet they appear to play little if any role in contributing to most
President Jane Crockett called the January meeting of the Shenandoah Valley Quilters Guild (SVQG) via Zoom to order at 9:30.. It was moved by Terry Wiita, seconded by Sandie Hammel
I examine the effect of irrigation dams on water pollution and infant health outcomes in South Africa.. To remove bias associated with non-random dam placement, I utilize
To limit open vial wastage, a restrictive vial opening policy has been implemented; 10-dose measles vaccine vials are only opened if six or more children aged 9 – 11 months are
Vandenberg, PP, AICP, is the newly appointed Executive Director of PlanSmart NJ and has a broad background in land use planning, community development, housing, and