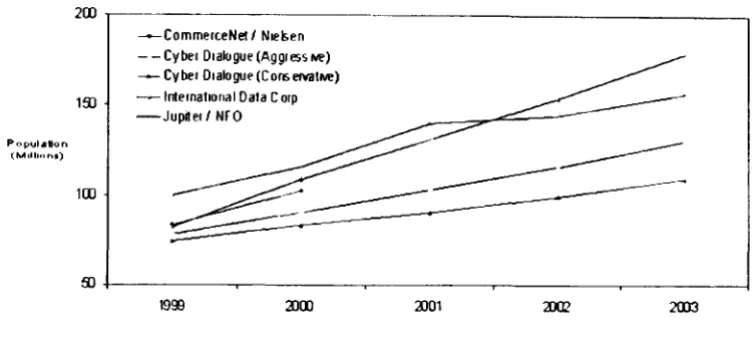
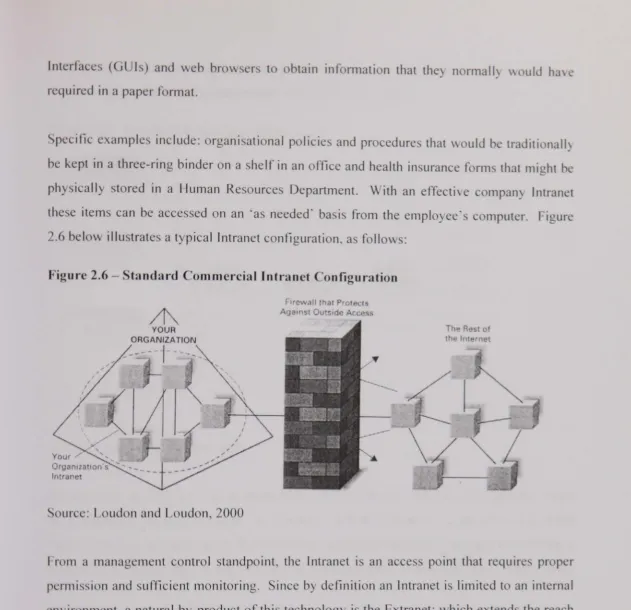
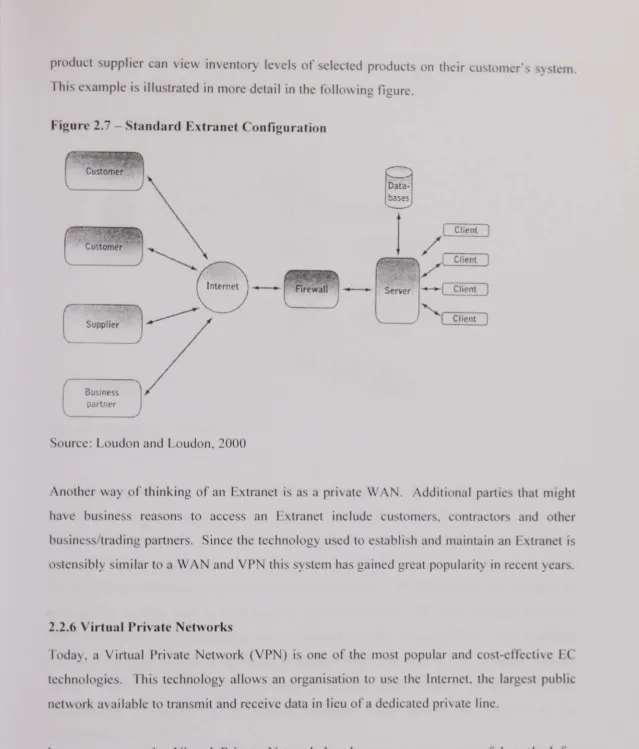
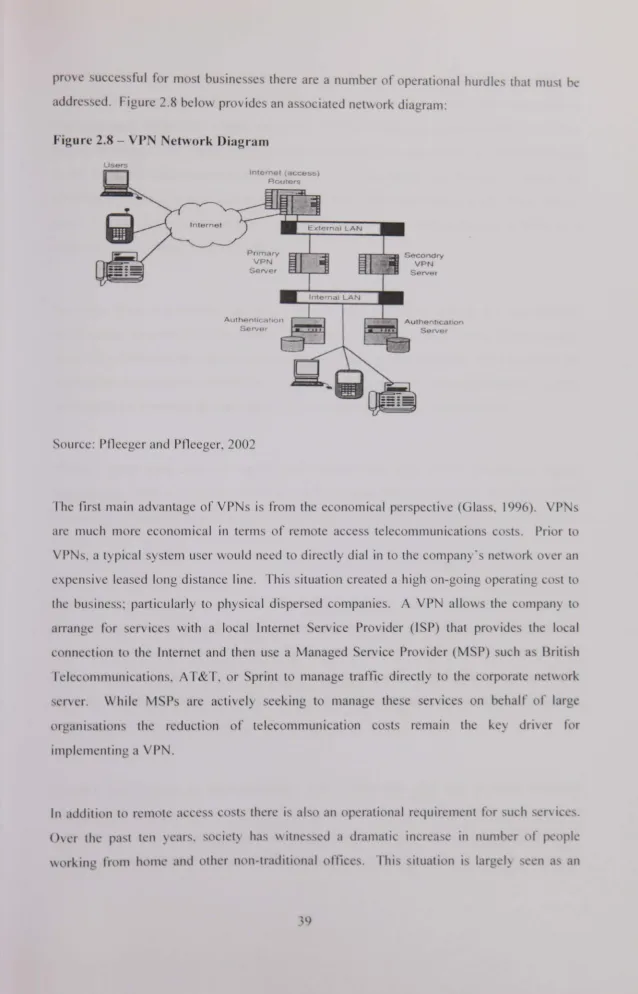
Cyber security information sharing in the United States : an empirical study including risk management and control implications, 2000-2003
Full text
Figure

Related documents
The purpose of Cyber Risk Management is to identify, analyze, and mitigate cyber-security threats and risks to critical information and technology assets and services. Risk
A statistically significant negative correlation was dem- onstrated in the study cohort between the maternal serum PIGF levels, foetal heart rate (FHR), birth weight and length,
Reviewing the clinical question, “Do anesthesia providers, implementing a temperature guideline compared to not using a temperature guideline affect the incidence of
In general, grants to other Section 501(c)(3) public charities and private foundations further a public charity’s exempt purposes, so a public charity can make a grant without
Ensure that clinically urgent patients are treated or seen in clinical priority order, and thereafter in strict chronological order within the target timescales set out in this
Depending on the berry developmental stage and the type of radiation (i.e., irradiance level, exposure length), increased UV levels activate different metabolic pathways through
The overall aim of the thesis was to evaluate the outcome in patients with stable trochanteric (Study II), unstable trochanteric (Studies I and III) and subtrochanteric (Studies I