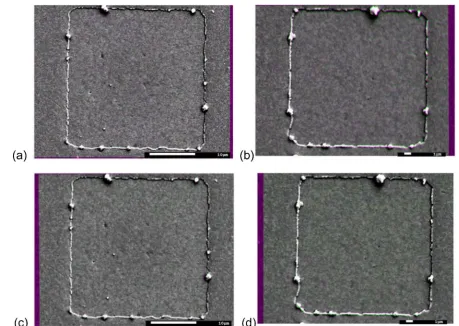
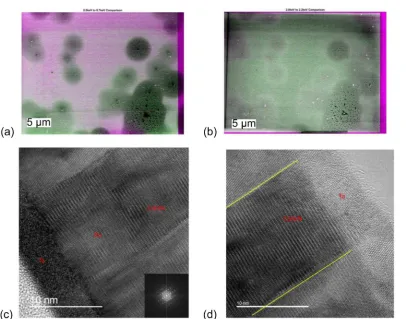
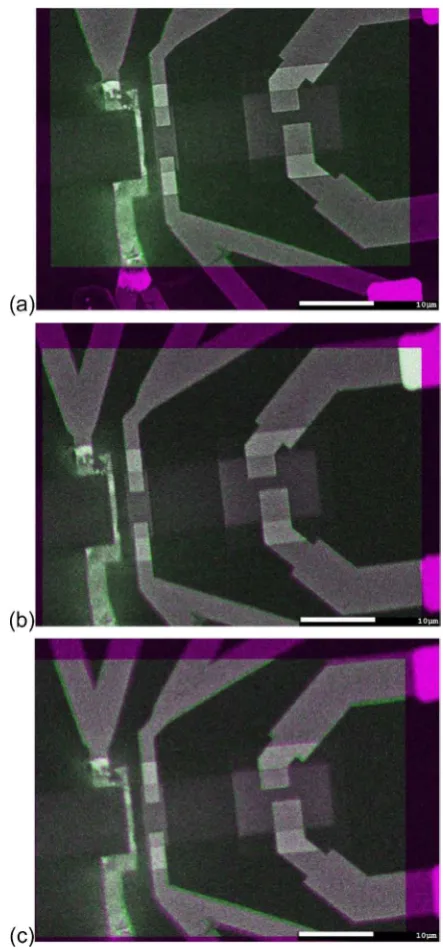
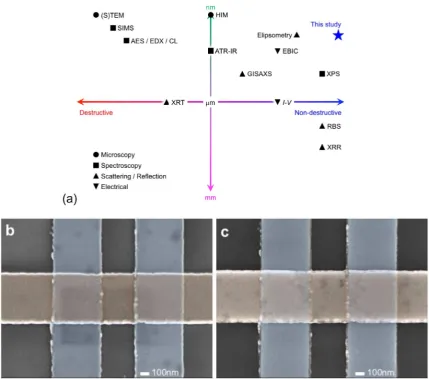
Non-destructive imaging for quality assurance of magnetoresistive random-access memory junctions
Full text
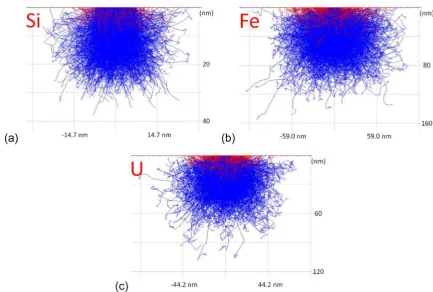
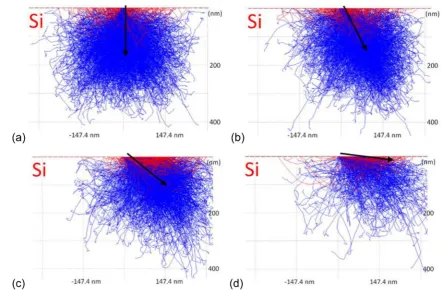
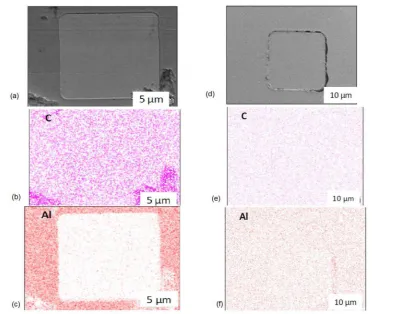
Figure
Related documents
In 1971, the United Nations began a study on how best to protect software, while simultaneously facilitating the dissemination of computer programs to developing nations.3
Further to using MODIS-derived albedo minima to extend the mass balance record of Brewster Glacier over the period of MODIS observations (2000– 2013), we proposed an alternative
It created the condition where relating in action became possible, when people setting up the second and the third jump were transforming the first jump into a performative
free or if their risk is uncorrelated with the market portfolio. We proceed to consider discount rates in the context of the CAPM single-factor pricing model. If government
Section III presents a model of fiscal solvency and sustainability and proposes two indicators to assess fiscal performance either over time or across countries: (i) fiscal
Creek project of Dole Philippines in Cogan creek, Malagos, Davao City was only participated. mostly by their employees, the local government unit thru the
(a) SO-OCBs Report Sector I encourage friends and family to use the hospital services. I tell people in other organizations that this is a good organization to work
We show how to transform the binary tree based signcryption scheme to a plain strongly forward secure signcryption scheme with evolving secret keys in Sec.. Last, a third party