Design and Analysis of Multisource Logs Forensic With Lock Technique for Cloud Security Enhancement
Full text
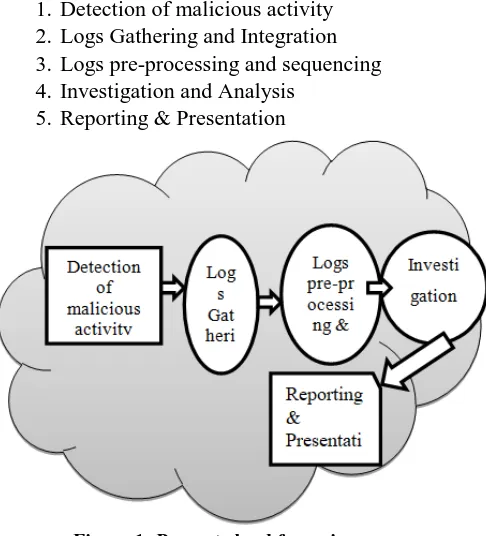
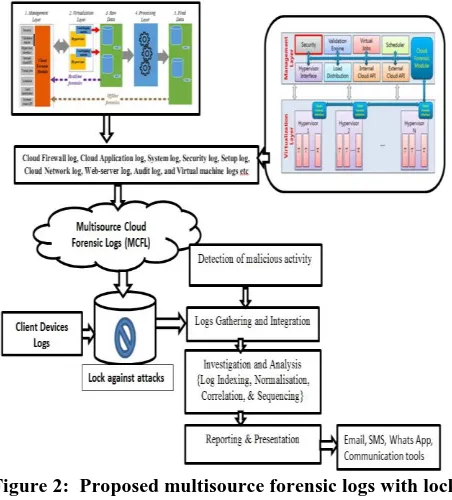
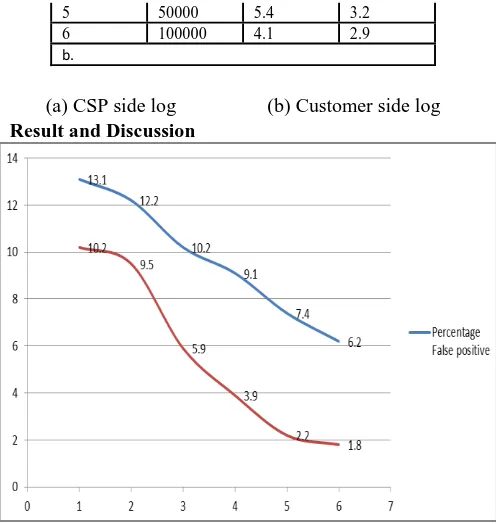
Figure
Related documents
the Commission for the Protection of Competition has held that the rules of bona fide trade practice have been infringed, as provided by art. The Supreme Administrative Court
While things may look different this year, NYSSO is committed to making everyone’s experience as safe as possible.With tackle football,flag and cheerleading practices beginning
Note: ACTIVE command is generated by dummy memory read from address 0 when FT800 is in sleep or standby mode.. This is followed by 2
Short Term Exposure: Available data indicates that this product is a skin irritant.. Symptoms may include itchiness and reddening of
Observations of inverse-Compton emission from components of radio-loud AGN in principle allow us to determine the magnetic field strength in those components — the energy loss rate
The dynamic range of the real-time PCR assay, i.e., the range of initial template concentrations for which accur- ate Ct values are obtained, was determined on the dilu- tion series
We hypothesized that, in contrast to young adults, (i) older adults would show stronger FC to the frontal regions under low load, as ageing has been associated with
(1) no thalamic or neocortical abnormality was observed in the acute clinical MRI; (2) volume reduction in the thalamus was strongly correlated with that in the hippocampus, and