The Hacker Playbook, Practical Guide To Penetration Testing pdf
Full text
Figure
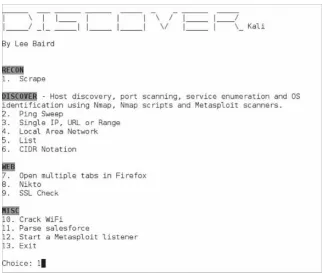
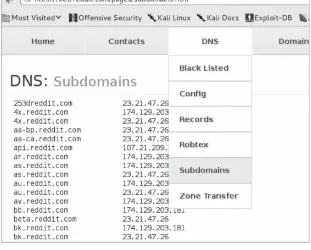
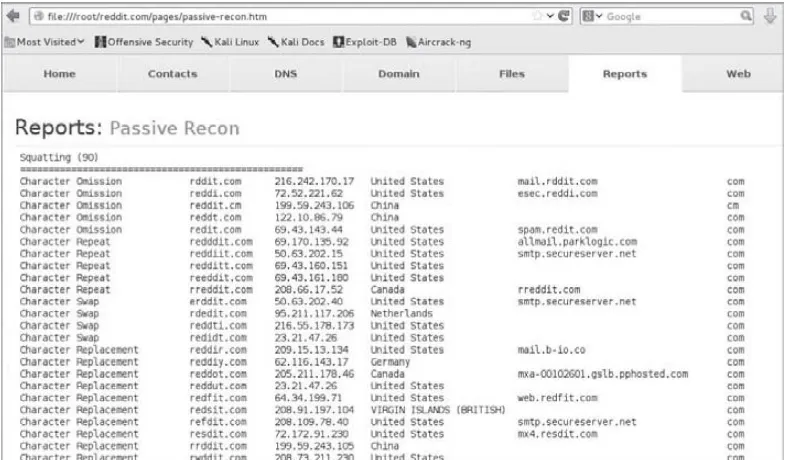
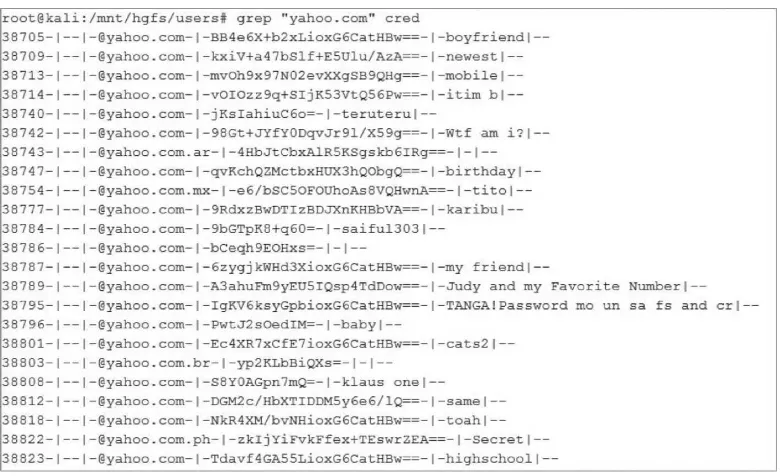
Related documents
Surya Surya Shukra Shukra Budha, Guru Budha, Guru Chandra Chandra LAGNA LAGNA Ketu Ketu Shani Shani M Ma an n a all Rahu Rahu.. REMEDIES FOR.. REMEDIES FOR KAAL SARP KAAL SARPA DOSH
• OpenSource Vulnerability Assessment Scanner • Previously GNessUs (a GPL fork of the Nessus) • OpenVAS is a security scanner to allow future. free development of the now-proprietary
An effective intrusion prevention and detection system includes limiting your vulnerabilities, knowing what methods attackers are using, educating your users,
Qualifying yarns for TACTEL® branded fabrics are available in the following Dtex counts: • Refer to NILIT Product Catalog. CHOICE OF
and mission length trend analyses are presented in Table 3 ... relatively few locations to estimate global trends. Last, the SeaWiFS mis- sion provided a stable and traceable source
When you are ordering replacement parts, please refer to this Parts Catalogue and quote both part numbers and part names correctly.. Modifications or additions which have been
Digital pho- tographs were taken at the delivery of final restorations in order to assess following variables; mesial papilla, distal papilla, soft tissue level, soft tissue contour
(Widiyanto, 2017, hal. 80), keterampilan hanya dapat diperoleh dan dikuasai dengan jalan praktik dan banyak latihan. Kemampuan berbicara ini dilatih dengan tujuan