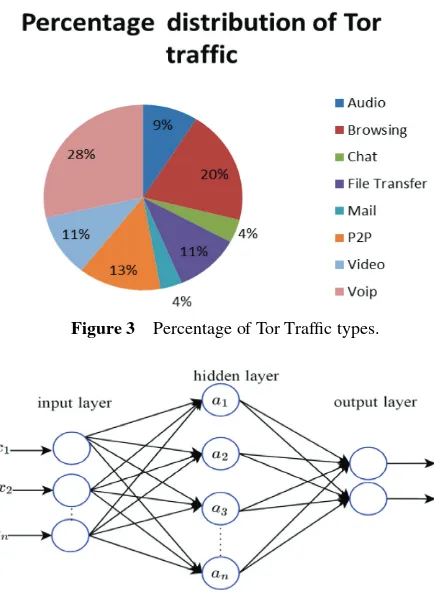
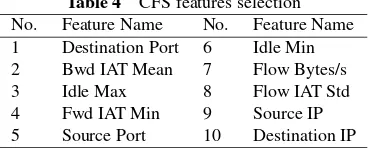
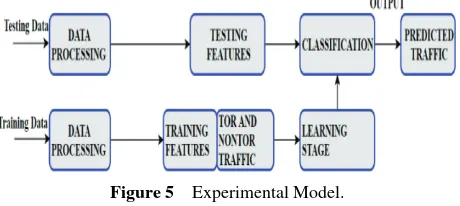
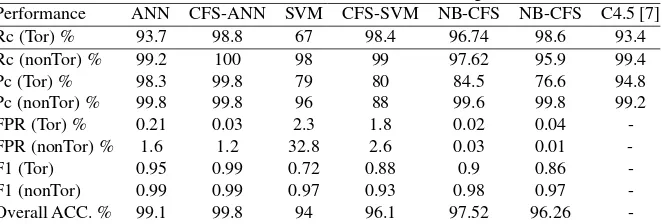
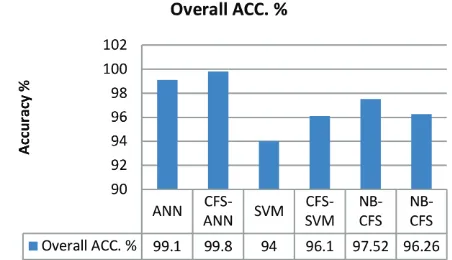
Machine learning approach for detection of non-Tor Traffic
Full text
Figure
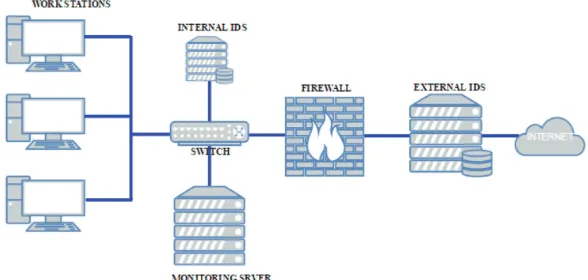
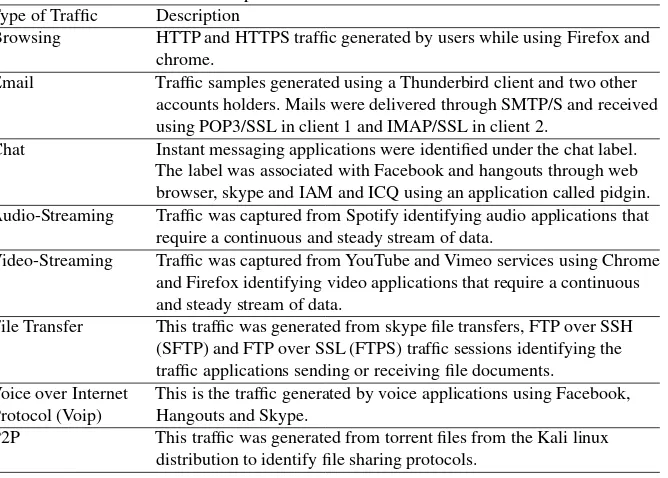

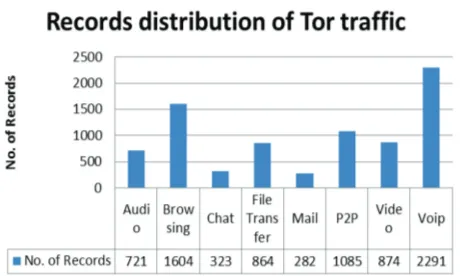
Related documents
Focus groups following an IPE simulation event will allow for a better understanding of how these events potentially impact student learning, future learning outcomes, and
to facilitate this project, says Douglas stayman, the school changed some of its programming, taking out courses like international finance and adding in classes on how to work
The renewal policy down payment will be assessed to the account information on file on the final day of existing policy unless notified in writing by the insured at least 10
In order to include generation from a neighbouring system in a capacity mechanism, the TSO of the country launching the CRM (hereafter CRM-system) must be sure that, during scarcity
Net cash reserves - defined as the excess of cash and short-term marketable securities over interest-bearing debt – increased by NT$25.78 billion to NT$213.79 billion at the end
The purpose of this study is to conduct a meta-analysis of studies that have reported consumer willingness-to-pay (WTP) or willingness-to-accept (WTA) values for GM food and
Advantages in either direction can be considered quite drastic with up to 20 percentage points in favor of testing only the first digit for the logistic distribution, and up to about
Dart provides a hybrid table schema to store spatial data in HBase so that the Reduce process can be omitted for operations like calculating the mean center and the median center..