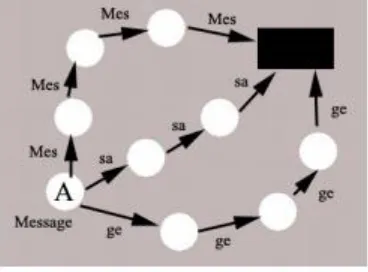
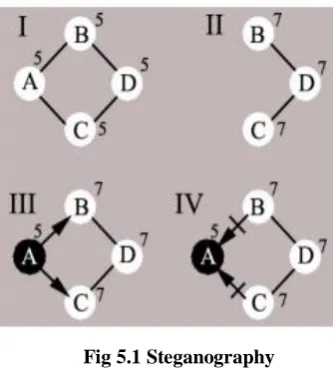
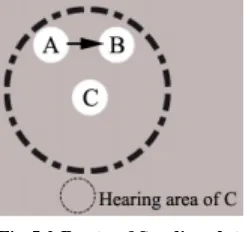
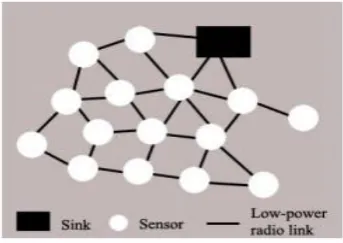
Attacks in Wirelesssensor Networks A Research
Full text
Figure
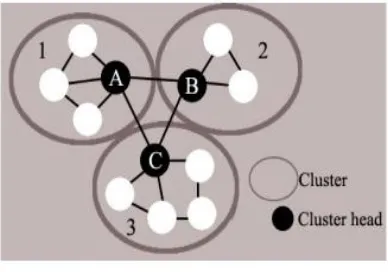
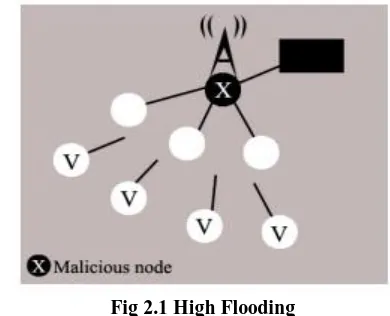
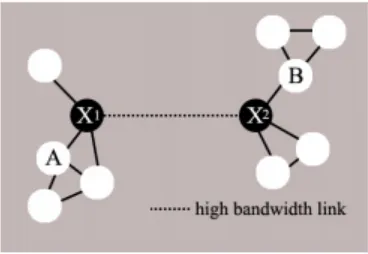
Related documents
Cited from www.dvb-h.org ; In the figure, DVB-T, as one candidate, is used to transmit broadcast signal. In fact, other digital terrestrial broadcast technology can also be
The scale used for the context and product congruence analysis was Likert (range 1 to 7) based on the article Kononova and Yuan. As a result of the pre-test, the question
TRI-CITIES PREP SCHOLARSHIP: A scholarship is avail- able for students from the Parish of the Holy Spirit who are inter- ested in attending Tri-Cities Prep High School. The
• 33-year-old male who presents to his doctor reporting a purulent urethral discharge and dysuria for 3 days • Lives in Dallas with history of travel to Hawaii 3
advantage over separate stroke and/or bleeding risk scores.[13] In the Loire Valley Atrial Fibrillation Project, a composite risk model included risk factors
Overall, IRF analysis suggests that: (a) asset prices and mortgage rate shocks have an impact on saving with some delay; (b) MEW shocks (through their component
Enclosure 12 was removed through formal coordination and approval of Reference (de); necessary information can be found in that issuance.. Change 10, 12/31/2020 26 ENCLOSURE 13
In the implemented directory protocol, on every cache miss, the core that causes the miss sends the request only to the home tile, which is the serialization point for all