SAAS: Attack Detection and Prevention with Forensic in cloud Environment
Full text
Figure

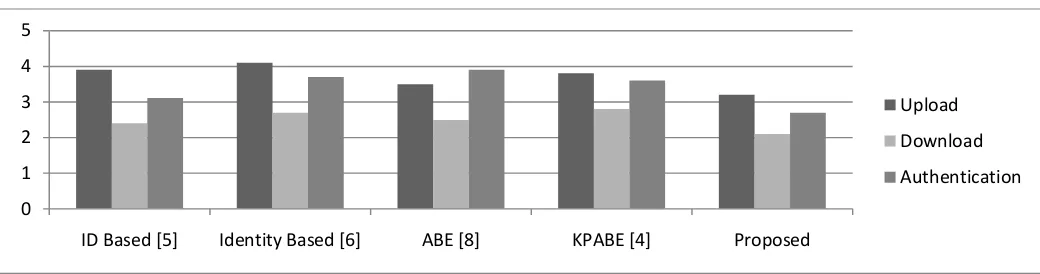

Related documents
2000 cGy (B), spinal cord; cursor was at the dose of 4500 cGy (C) and liver; cursor was at the dose of 3000 cGy (D) in conven onal AP-PA reciprocal parallel plan and four
[6] and [9] mainly discuss the TDMA scheduling scheme that requires the minimum time slot in convergecast in the linear sensor network, but they do not mention how to balance the
[Assented to 25th July, 1917.] WHEREAS The Canadian General Council of The Boy Scouts Association has by its petition prayed that it be enacted as hereinafter set forth, and it
The approved body shall audit the manufacturer’s factory production control system including the prescribed test plan (Table 7) at least once a year to ensure that the PT
This finding goes to justify the proposal of Randall (2004) that using a systematic approach to the taking of notes can enhance understanding and remembering of lecture
Simpson, Tiffany, "Do Objective Measures reduce the Disproportionate Rates of Minority Youth Placed in Detention: Validation of a Risk Assessment Instrument?"
Study of relation between coping ways with individual’s characters and mental health in infertile couples who refer to Yazd infertility center.. Tehran, Tarbiat
Dye-sensitized photoelectrosynthesis cells (DSPECs) provide a flex- ible approach for solar water splitting based on the integration of molecular light absorption and catalysis on