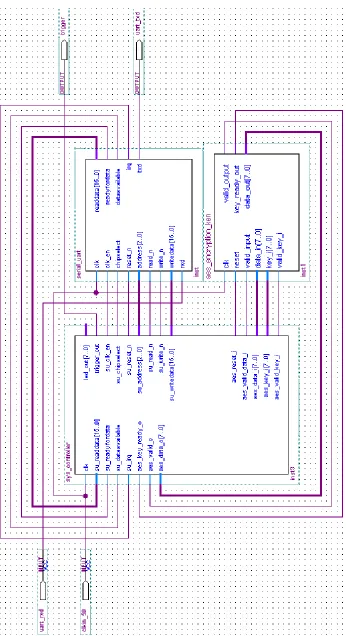
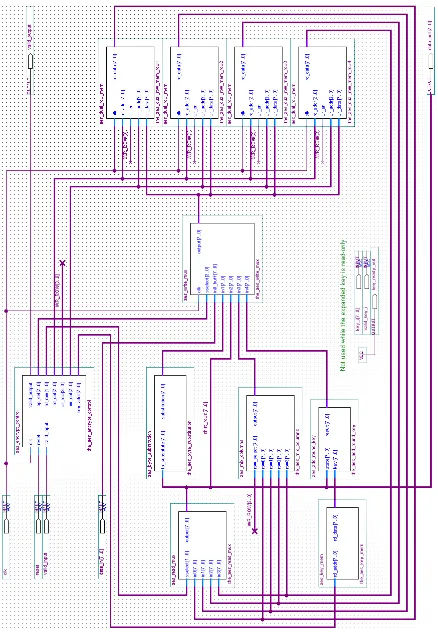
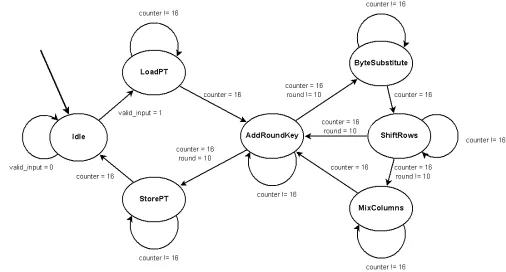
Methodologies for power analysis attacks on hardware implementations of AES
Full text
Figure
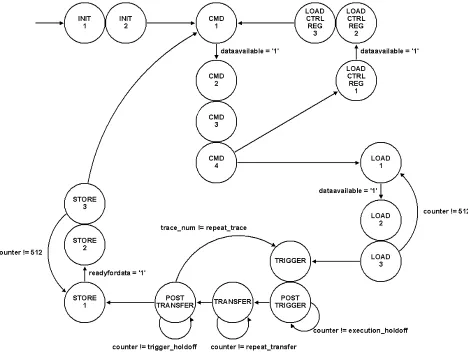
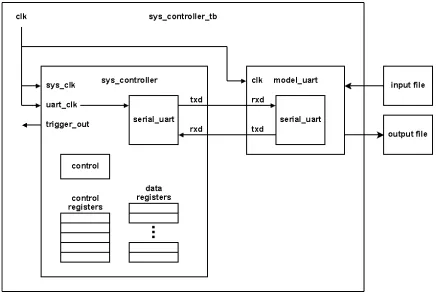
Related documents
Our new favourite thing will be to listen to music together We will be so happy when Covid is
Comparative study of various bomber aircrafts The first step in the design of aircraft is to collect data of existing aircraft of similar purpose i.e., bomber.. This step
3.2 Multidimensional inequality measures which fulfil PDB derived from social evaluation functions. We focus on the derivation of relative inequality measures following
Even if we were able to correctly classify each Twitter user, we would not be able to make a reliable estimate of the voting results as (i) several Twitter users may not vote,
She has created mechanisms to feedback customer service and mystery shopping data into real time, revenue producing activities by the front line and outside sales forces.
Nelson, L. in Instructional Technology, University of Central Florida). Project management in higher education. in Educational Leadership, University of North Carolina at
Marriage certificates show that in Morteros the majority of these repeated pairs belong to Italian pairs and Spanish pairs of surnames, in both immigration and post-immigration
In order to approach the question of whether USP2a is involved in bladder cancer progression and aggressive- ness, we analyzed USP2a mRNA expression level by qRT- PCR using