Two‐Step Authentication in Mobile Ad Hoc Networks
Full text
Figure
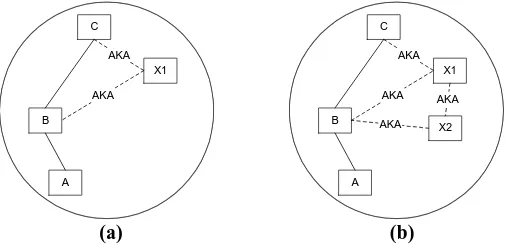
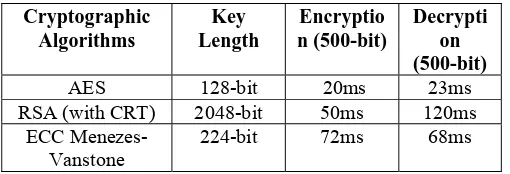
Related documents
Analytical methods like Rayleigh-Ritz method, Galerkin method or orthogonal polynomials have been extensively used in many research works to obtain the natural
These include changing how C is allocated in fixed and dynamic schemes based on data from current forest syntheses and different parameterization of allocation schemes for
Psychological and social consequences of non invasive prenatal testing (NIPT) a scoping review RESEARCH ARTICLE Open Access Psychological and social consequences of non invasive
BioMed CentralWorld Journal of Surgical Oncology ss Open AcceCase report Frontal skull craniotomy combined with moderate dose radiotherapy effectively ameliorate a rare case of non
The environmental impacts of dye based textile inks mainly come from the energy required for pre-treatment, fixation, post treatment and wash off procedures, with associated
The similarity between the patterns of soil moisture differences (WT − FD runs) and wtd (WT run) illustrates the controlling role of groundwater in soil mois- ture spatial
Figure 2 Phylogenetic analysis of 2019-nCoV in the context of β-coronaviruses Maximum likelihood-based phylogeny of full genomes of 2019-nCoV isolates was generated with the
Integrated basin management prac- tices and the importance and role of irrigation and hydropower plant operation in integrated basin management, how it should be, optimal use