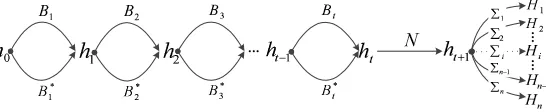
Cryptanalysis of GOST R Hash Function
Full text
Figure




Related documents
13 Because Goblin Market explicitly and undeniably focuses on the body’s (and mind’s) desire for exotic foodstuffs, and because the text emphasizes the female by the exclusion
When a pathway diagram is used as an illustration, desktop publishing tools can be used to draw the diagram (Adobe Photoshop, Paintshop Pro, etc.). In this role, pathway
In this paper we made an attempt to study the mechanical and wear behaviour of Al alloy composites containing various al2o3 compositions namely 3%, 6% and 9% by
In this paper, we examined the influence of the fabrication process on mechanical properties, molecular interactions and thermal properties of PLA/MWCNT composites
Shear bond strength tests confirmed the occurrence of fracture within the porcelain [56]; whereas in the porcelain fused to metal (PFM) the cracking is observed
In addition, for a given scavenging application and native workload, using a low priority for a scavenging process performs implicit, “best-effort” performance control,
The aim of this research is to study the physical properties of a class of organic semiconductor materials in the form of isolated molecules and molecular