High Throughput Opportunistic Cooperative Device-to-Device Communications
Full text
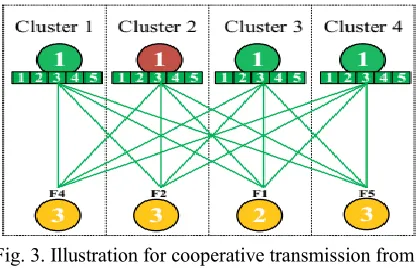
Figure


Related documents
5.1 The Supplier shall ensure that a written policy exists for pre-employment screening and that the screening status and results of all Supplier personnel on the Sky account or with
Computer Hardware Management Software Tamper-proofing Remote Control Customized Interface Operating System Filesystem Device Drivers Graphical Interface Application Software
Third, from the 1-min sequence of eyelids distances and via a temporal CNN, the “drowsiness” module (1) extracts features related to the eye closure dynamics at four timescales,
Membership information is included in ASET’s searchable on-line membership directory. However, we recognize the importance of employee privacy and provide options relating to
You can avoid chasing the 100-percent uptime myth by using technology to deliver a level of service availability your customers can be happy about, thus making the threat of
Analise da comercialização de alimentos através do Programa Nacional de Alimentação Escolar (PNAE) no Município de Marechal Cândido Rondon, Paraná, foi realizada
• 11% of agencies reported external fraud involving misuse of identity – 1,153 incidents of creating and/or using a fictitious identity / forgery – 2,859 incidents
This week-long seminar partners the renowned academic reputation of Tel Aviv University with the American Society for Industrial Security (ASIS) International, the