Data Intensive Dynamic Scheduling Model and Algorithm for Cloud Computing Security
Full text
Figure


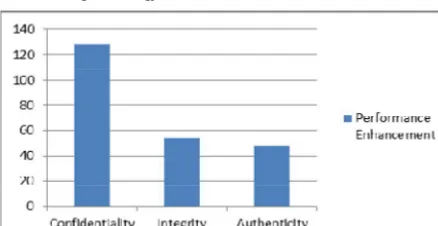
Related documents
Keywords : Netdosis, two-sided markets business model, two-sided markets strategies, pricing, network effect, pediatrician, pharmaceutical companies, and off-
“window sign” means a sign which is permanently painted on or attached to the windowglass of a building used for commercial,
3 Through tight monitoring of local governments underpinned by a result-oriented governance, and enhanced coordination of local officials, decentralisation has allowed the
You can specify the period (“window”) of time after a transaction is submitted during which the payment gateway checks for a duplicate transaction (based on credit card number,
The confidentiality and integrity of data processed by the Viewabill solution is protected by numerous layers of security technologies and processes.. By using a cloud computing
• Sets demands on the science park’s network • Science parks as hub for R&D companies. • Science parks must choose branches where they can add value to
leaves of Holarrhena antidysenterica ; hence the present study aims to investigate the ability of ethyl acetate fraction of Holarrhena antidysenterica Linn leaves (EAHA) to
It is quite common for people that have just retired, to sell their house, buy a smaller home instead, and invests the remaining money in overseas property - buying a house