Cloud Based Enterprise Adoption by SMEs in Ghana
Full text
Figure
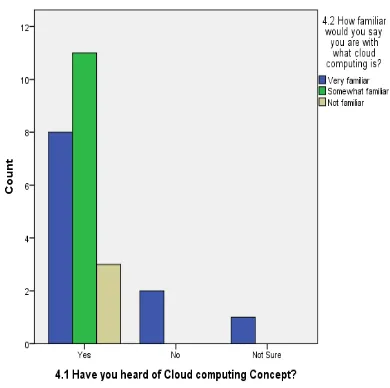
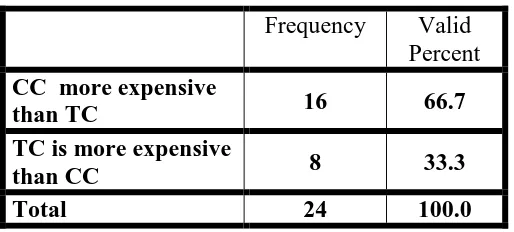
Related documents
We see that, for instance, the EVBS model generated from Gumbel (Ferreira et al., 2012) has “heavier” tail than the classical BS, and hence it can better accommodate data within
This is done through a Java toolkit, called Visidia [3,2,4,5] (for Visualization and simula- tion of distributed algorithms), whose graphical interface allows the user to build
The presentation has not been updated since it was originally presented, and does not constitute a commitment by any CDF entity to underwrite, subscribe for or place any securities or
Database Design: The System Development Life Cycle (SDLC), The Database Life Cycle (DBLC), Database Design Strategies, Transaction Management and Concurrency
When analysing changes occurring in the milk yield and composition depending on successive lactation it was concluded that the highest amount of obtained milk, calculated FCM and
While direct support to federal, state and local border security and immigration enforcement can help deter illegal cross-border smuggling, military activity in
Based on cloud computing and virtualization technology, we establish a cloud computing server storage architecture, design deployment of server virtualization service, and
Juniper’s flexible business edge solution is a comprehensive VPN toolkit that offers service providers and large enterprises a feature rich and standard-based network that