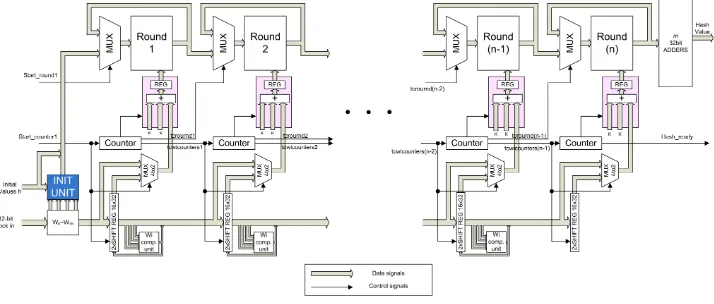
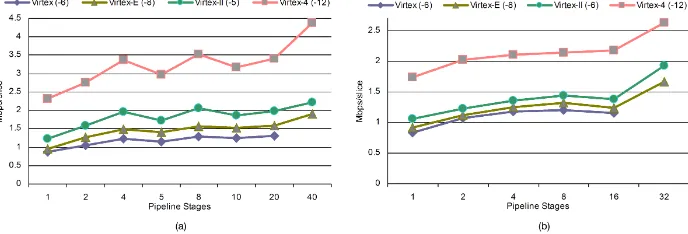
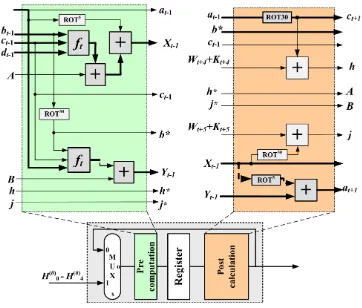
Area throughput trade offs for SHA 1 and SHA 256 hash functions’ pipelined designs
Full text
Figure



Related documents
Our general model simplifies the presentation of total variation based methods in that it reduces the duality treatment to a common theorem.. Furthermore, we address a loss of
Using a very simple overlapping generations model, we have shown that in a world without any barrier to international investment, where all is done to induce
Child welfare researchers and professionals have observed that residential treatment or group care of foster children is best used sparingly for children with serious
dependent on other opioids. Dependence and abuse, including drug-seeking behaviour and taking illicit actions to obtain the drug, are not limited to those patients with prior
Required: Master’s Degree in the Social Sciences or Education and a minimum of 15 years’ experience in the Organizational Development field or in a related area. Senior
Since it has been shown that WDDL suffers from the early propagation effect [20], DPL-noEE connects the signals of the true and false network to the same gate and evaluates the
In recent days multilevel inverters has become very popular for motor drive applications of industry .Multilevel pulse width modulation inversion is an effective solution