Implementation of DNA Cryptography in Cloud Computing and using Socket Programming
Full text
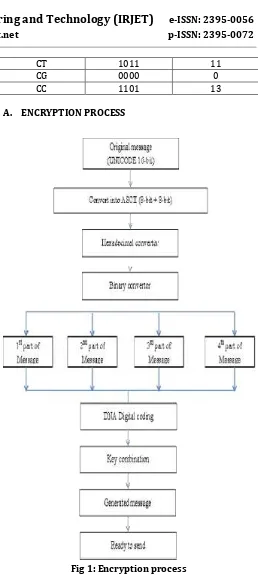
Figure

Related documents
To demonstrate drug treatment anatomically the functional difference in each intestinal part of male mice after treatment with beta-agonist fenoterol at 7,14,21
Moreover, the suitability of groundwater for irrigation was determined according to the sodium absorption ratio (SAR), percentage sodium (% Na) and permeability
that are factors
CI: Confidence interval; FEV 1 %: Forced expiratory volume in one second percent; CF: Cystic fibrosis; HCWcf: Adult healthcare workers with CF; Non-HCWcf: Adult non-healthcare
Another important unresolved barrier is the lack of clarity in the call centre program direction. However, policy changes at the provincial ministry of health level that would
Simulations of data sets containing a mixture of single and double mutants under this landscape show that inferences about the distribution of fi tness effects of bene fi cial mutants
On the other hand, smaller groups of the MLFMA should be used because, for a small group size, the number of subdomains that belong to adjacent groups is small, and therefore only
Children who subsequently developed complications differed from other groups of children as follows: (i) the numbers of CD3 1 and CD4 1 cells were lower than in uninfected children (