An Application Oriented Network Model for Wireless Sensor Networks
Full text
Figure
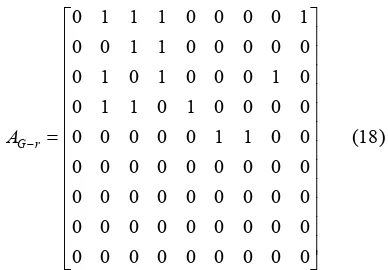
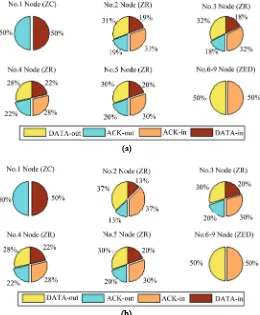
Related documents
Table 3.3: Classification accuracy using decision fusion (GMM classifier) and feature fusion (SVM classifier), where (1) represents the enhanced summary autocorrelation pattern,
This sections presents a theoretical model of the incentive structures underlying grading systems from very coarse to very fine. For simplicity, I write the model specifically for
Subsequent failure to achieve the required grade point average will result in the student's suspension from the College unless the student earns a 2.0 average on the hours of
(2006) Rural Ken y a and Madagascar Multiple equilibria in asset space LOESS of curren t herd size on 3 mon th earlier herd size Find evidence of dynamic p o v ert y trap An tman
Job Targets Sought: Accounting; Business Administration; Computer Information Systems; Economics; Finance; Health Science; Management; Marketing; Public Administration;
(2006) “Web versus Email Data Collection: Experience in the Current Employment Statistics Program”, Proceedings of the Section on Survey Research Methods, American
Heavenly Father, we come to You as the original disciples came to Jesus and we ask, “Lord, teach us to pray.” We will need to know about prayer along the way, but we really need to
Critical Contact Critical Contact Critical Contact Critical Contact Critical Contact Contact Process Competitor Trigger Contact Outcome Situational Influential