Hacking the next web: penetration testing over IPv6
Full text
Figure
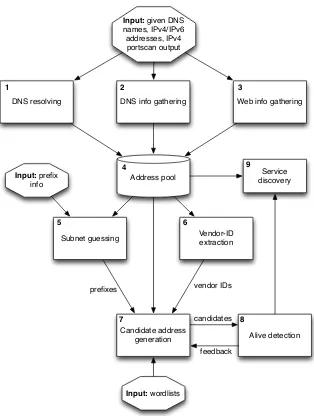
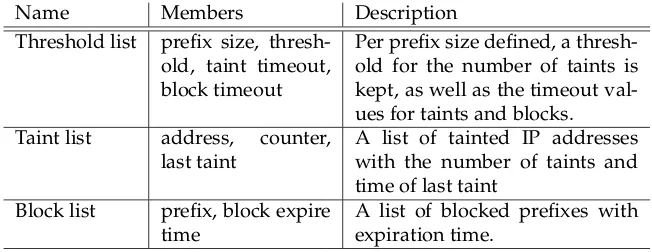
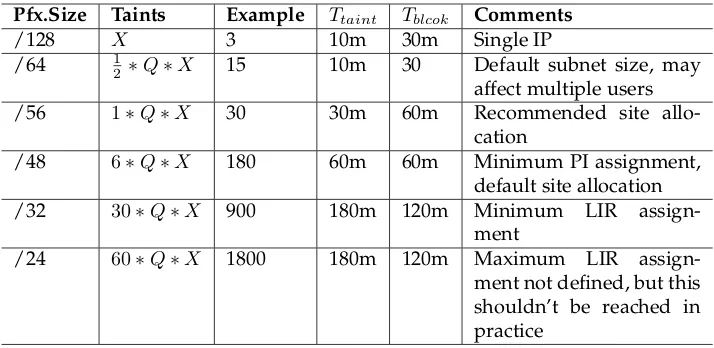
Related documents
In addition to connecting the IPv6 network with the IPv6 Internet through the IPv4 network, the prefix is the same and the 6to4 router will encapsulate the IPv4
neighbouring properties the generous gardens and grounds of Green Haven include and ample driveway parking to the front of the bungalow, garage and car port offering..
The results obtained suggest that, in both Germany and Spain, there is a positive association between the importance that companies give to factors that impede their
Workshop on Strategic Executive Leadership International Bank of Qatar 5/20/2010 12/20/2010 Business & Management Training of Medical Services Director Qatar Petroleum
Penelitian ini menggunakan teori tanda-tanda oleh Peirce dan teori code oleh Chandler untuk menganalisis tanda-tanda yang digunakan dalam beberapa iklan billboard rokok di jalan
Local Addresses With Network Prefix • Unique Local IPv6 Unicast Address. – Addresses similar to the RFC 1918 / private address like in IPv4 but will
Analogously, if 12% of the documents in a sample are found to be responsive, and the sample size is sufficient for a margin of error or confidence interval of plus or minus 5%,
Characterization Techniques Test Invasive/ Noninvasive Sample Recovered Usage Standard penetration test Invasive Yes Extensive Cone penetration test Invasive No Extensive