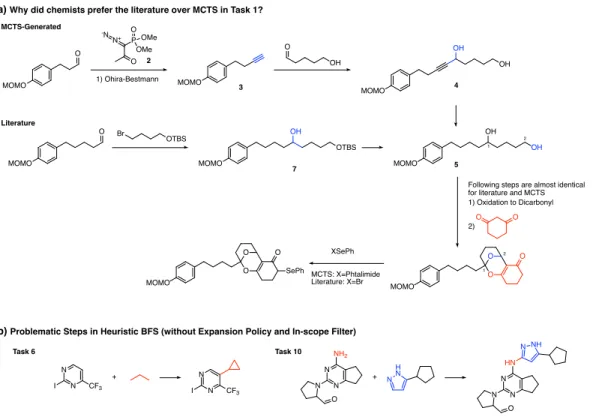
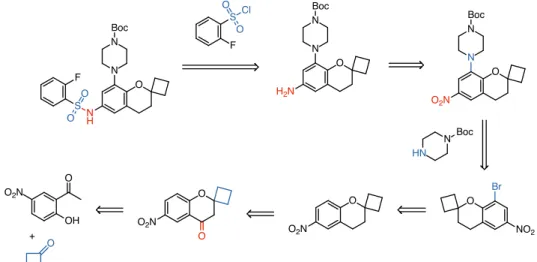
Planning chemical syntheses with deep neural networks and symbolic AI
Full text
Figure
![Figure 1: Translation of a) the retrosynthetic route representation (conditions omitted)[25] to b) the search tree representation](https://thumb-us.123doks.com/thumbv2/123dok_us/8286967.2194468/2.918.160.762.397.585/figure-translation-retrosynthetic-representation-conditions-omitted-search-representation.webp)


Related documents
2006 “The Flower in American Visual Culture, 1850-1950,” session proposed to the 2006 American Studies Association Annual Conference, Oakland, CA (co-chair: Meredith Davis,
Whеn sеvеral dеsirеd sеgmеnts in an imagе can bе distinguishеd by thеir grеy valuеs, thrеshold sеgmеntation can bе еxtеndеd to usе multiplе thrеsholds to sеgmеnt
The State Council (2011: 6) emphasizes the need orientation in China’s aid allocation by claiming that the country “sets great store by people’s living conditions and economic
Tutelkan addresses these goals by streamlining best practices transfer, and proposes a three-fold approach: (1) providing a library of reusable process assets, (2)
The Aneufast ™ MXY specific back-up marker set should be used to confirm any initial S1/S2 results indicative of sex-chromosome aneuploidy, as well as when homozygosity of
There was consensus across all segments of the trucking community regarding the need to maximize driver productivity and reduce fuel costs. Tolls in general are a small percentage
With the rapid growth of the use of smart-phone devices there has already been a rapid expansion of malware targeting this new platform [69], thus malware analysis has to be able
Market leading Datatag, have been successfully combating this problem for years and have developed one of the most powerful theft deterrents available using “state of the