ISSN (Online): 2348 – 3539
HOMOMORPHIC ENCRYPTED DOMAIN WITH DWT METHODS
N.HABEEP
1, R.Dayal Raj
2Salem College of Engineering And Technology- Salem
Abstract: The Signal processing in the Cryptosystems play an important role in secure signal processing, but not all cryptosystems are appropriate for signal processing in the encrypted domain. is a new technology with the goal of protecting valuable signals from insecure signal processing. This paper has investigated the implementation of DWT and MRA in a Homomorphic encrypted domain and tackled the problem of data expansion caused by quantization errors under the framework. To solve the problem of data expansion, which may be very important in practical applications, we present a method for reducing data expansion in the case that both DWT and IDWT are performed. With the proposed method, multilevel DWT/IDWT can be performed with less data expansion in Homomorphic encrypted domain. We propose a new signal processing procedure, where the multiplicative inverse method is employed as the last step to limit the data expansion. Taking a 2-D Haar wavelet transform as an example, we conduct a few experiments to demonstrate the advantages of our method in secure image processing. We also provide computational complexity analyses and comparisons.
Keywords: Data expansion, DWT, MIM, MRA.
Reference to this paper should be made as follows: N.Habeep1, R.Dayal Raj2 (2014) „Homomorphic Encrypted Domain With Dwt Methods‟, International Journal of Inventions in Computer Science and Engineering, Volume 1 Issue 3 2014 .
1 Introduction
Image processing in the encrypted domain, also referred to as secure signal processing (SSP), has attracted considerable attention in recent years. This new technology may promise two kinds of applications in future. The first one is in the case when the owners and manipulators of data are two different parties. For example, in the scenario of network media distribution, the customer may be asked to embed a watermark in the media to trace illegal copies. Since plain media can be easily attacked by the customer during watermarking, a solution is to embed the watermark in the encrypted media, whose content is protected by the cryptosystems. Signal processing technology in the encrypted domain provides powerful tools to make such secure implementation possible. The second application is in privacy protection. For example, in the case of a remote access system based on biometric data, the users‟ sensitive authentication information will be stored in the server. processing encrypted signals is indeed feasible by relying on probabilistic Homomorphic encryption and secure multiparty computation (MPC), we focus on techniques based on Homomorphic encryption, since they constitute the basis for any practical implementation of s.p.e.d. theory. A cryptosystem is said to be Homomorphic with respect to an operation*, if another operation + exists such that, given two plaintexts m1and m2.
we have
This is the case of linear operators like the discrete Fourier transform (DFT), finite impulse response (FIR) filters,
correlation, and simple operations among two or more signals like component wise signal addition [1]. The JPEG-2000 standard specifies two wavelet transformations, which are irreversible Daubechies 9-tap/7-tap filters and reversible 5-tap/3-tap filters. They are chosen for a number of reasons [1]. Both of them have short finite impulse response (FIR) filters, so fast computation can be implemented. 5-tap/3-tap transformation has only two lifting steps, which help to achieve a very low computational complexity.9-tap/7-tap transformation has the highest values of Peak Signal to Noise Ratio (PSNR) over many test images for low bit rates [2].The New trapdoor mechanism and derive from this technique three encryption schemes : a trapdoor permutation and two Homomorphic probabilistic encryption schemes computationally comparable to RSA. The technique conjugates the polynomial-time extraction of roots of polynomials over a finite field with the intractability of factoring large numbers.
1)A New Probabilistic Encryption Scheme
Scheme 1. Probabilistic Encryption Scheme Based on Composite Residuosity.
The correctness of the scheme is easily verified from Equation 2, and it is straightforward that the encryption function is a trapdoor function with _ (that is, the knowledge of the factors of n) as the trapdoor secret [3]. Based on the watermarking of a ROI signature (computed on independent pixel blocks) into RONI of the image. As it will be shown, the embedded signature allows us achieving L1 to L3 under the constraint of low watermarking capacity performance. one can associate three distinct levels of integrity:
Level 1 (L1): Modification Detection -- an alarm should be given under any kind of image modification;
Level 2 (L2): Modification Location -- untrustworthy parts of the image have to be indicated; either in a rough way, so as to designate areas still interpretable by the physician;
Level 3 (L3): Forensics analysis -- the nature of the modification over the whole image or within untrustworthy regions has to be identified (accidental, authorized/non authorized).
We assume that L1 and L2 procedures have been already performed. We only focus on L3. We recall that our system decides if the modification is global or local based on the output of L2. If all blocks are declared unauthentic, then it tries to identify the nature of the global tampering; otherwise, it looks for approximating local modifications in blocks indicated as tampered [4].
2. Existing Method
In existing, embedded and/or extract Watermarking on encrypted image without being able to decrypt is a challenging problem. We firstly discuss the implementation of Walsh-hadamard transform (WHT) and its fast algorithm in the encrypted domain, which is particularly suitable for the Applications in the encrypted domain for its transform matrix, consists of only integers. In changed the relations among the adjacent transform coefficients, in using WHT based image Watermarking Algorithm in the encryption domain. Due to the constrains of the encryption, extraction a Watermarking blindly from an encrypted image extraction both in the Decrypted Domain and encrypted Domain. on
the implementation of the discrete Fourier transform (DFT) as well as the fast Fourier transform (FFT) on encrypted signals. A data encrypting method, which packs several samples as a single one, Due to the limitation of the encryption, it is very difficult, sometimes impossible, to transplant the existing mature watermark scheme to the encrypted domain. Thus it is meaningful to design a new image watermark scheme under the constraints of the Homomorphic encrypted domain.
A. Walsh-Hadamard Transform in the Encrypted
Domain
WHT is used widely in the field of signal processing. The transform matrix of WHT contains only and no multiplications are required in the computation. Thus WHT is more efficient than other orthogonal transformations, such as DFT or DCT. Another advantage of WHT has is that WHT will not bring the quantization error in the encrypted domain. WHT can therefore be perfectly reconstructed in the encrypted domain.
B.Fast WHT in the Encrypted Domain
2D WHT is a separable transform, i.e., a 2D transform which can be decomposed into two 1D transforms. Specifically, performing 2D WHT on I(x; y) is equivalent to performing 1D WHT on the each column of I (x; y) first and then performing 1D WHT on the each row to the former result. The fast algorithm follows the recursive definition of the Hadamard matrix2. There are totally M log2M additions/subtractions for the fast WHT. More specifically, every two coefficients are obtained at one stage from another two coefficients at the previous stage by using only addition or subtraction3.
C. Blind Image Watermarking in the Encrypted
Domain
In order to embed a watermark on an encrypted image, we should tackle two challenging issues. The first one is how to achieve the goal of blind watermark exaction.
Since the original image is protected by the encryption, it is not practical to involve the plain original image into the extraction.
2.1. Watermark Embedding
The embedding domain, e.g. the spatial domain or the transform domain, plays a crucial role in robust performance and the visual quality of the watermarked image. In order to make the watermark scheme more robust, we choose to embed the watermark in the transform domain rather than the spatial domain.
2.2. Watermark Extraction
For our watermark scheme, the watermark extraction can be accomplished in either the plain domain or the encrypted domain. That is, we can extract the watermark either from the image IW; 256 (x; y) or from the encrypted image ~Iw (x; y). After the watermark has been extracted, it will be compared to the original watermark with some metrics. We use the bit error rate (BER) to measure the difference between the extracted watermark and the original one. If we denote the extracted watermark by w0j , then the BER of w0j and wj is given as 4
2.3. Extraction in the Encrypted Domain
In order to extract the watermark from the encrypted image, we segment ~Iw(x; y) into non-overlapping blocks of m *n. According to the sequence a, we select n blocks from total (M=m)2 blocks. We then apply WHT of size m*m to all the selected blocks to output the encrypted coefficients. Let us denote those encrypted coefficient blocks by5
2.4. Extraction in the Decrypted Domain
Let us consider the case of extracting the watermark from the decrypted watermarked image. Based on the analysis the implementation of watermarking in the encrypted domain will enlarge the plain value of the watermarked image. And small modification of the transform coefficients may result in large variation in the spatial domain 6. Thus the decrypted values are very likely to be greater than 255 or less than 0.
{wj}will be compared with the embedding message {wj}by using the BER metric to output the result that whether there is a watermark in Iw;256(x; y)7.
2.5 Parameter Settings
Cryptosystem‟s modulus N : longer than 1024 bits.
The average PSNRs on 100 images of 512*512 is 43dB. The BER > 43dB when WNR > -10.
3. Our Contributions
A method of proposed technique for implementing discrete wavelet transform (DWT) and multiresolution analysis (MRA) in Homomorphic encrypted domain. We first suggest a framework for performing DWT and inverse DWT (IDWT) in the encrypted domain, then conduct an analysis of data expansion and quantization errors under the framework. To solve the problem of data expansion, which can be very important in practical applications, we present a method for reducing data expansion in the case that both DWT and IDWT are performed. With the proposed process, multilevel DWT/IDWT can be performed with less data expansion in Homomorphic encrypted domain. We propose a new signal processing procedure, where the multiplicative inverse method is employed as the last step to limit the data expansion. Taking a 2-D Haar wavelet transform as an example, we conduct a few experiments to demonstrate the advantages of our method in secure image processing. We also provide computational complexity analyses and comparisons.
This paper addresses the issues of DWT and MRA in the homomorphic encrypted domain. Firstly, we describe a framework for performing DWT and IDWT in homomorphic encrypted domain. The framework can be used for general purpose operations on encrypted data. For instance, pyramid algorithms can be implemented in the encrypted domain by using our strategy. We then conduct the analysis of data expansion and derive an upper bound on the accumulated error for decomposition and reconstruction. Secondly, we propose a method, called the multiplicative inverse method (MIM), to remove the quantization factor without decryption. The proposed method provides a solution to the problem of data expansion. By using the proposed method, MRA can be implemented homomorphically in the encrypted domain with much less data expansion.
3.1 Paillier Cryptosystem:
A. Probabilistic Homomorphic Cryptosystem
The homomorphic cryptosystem was first introduced as a privacy homomorphic, which is defined as an encryption function allowing one to operate the ciphertexts without decrypting them into plaintexts. Specifically, there exist two algebraic operations corresponding to each other, one in plaintext space and the other in cipher text space. If m1 and m2 are any two plaintexts in homomorphic cryptosystems, we have
corresponding algebraic operations in the cipher text and the plaintext spaces, respectively.
The Paillier cryptosystem is a public key cryptosystem which has been proved to be semantically secure. It has an additive homomorphic property. That is, for any two ciphertexts, one can generate a ciphertexts of the sum of the plaintext as long as the public key is known (9),(10).
Public key and the private key,.
The decryption process of c can be described as (11)
The following equations (5) show some useful homomorphic properties of the Paillier cryptosystem.
3.2 Discrete Wavelet Transform In The Encrypted
Domain:
This method of DWT in the encrypted domain and compute an upper bound of the decrypted wavelet coefficients.
A. Integer Approximation And Evaluation
DWT is widely used in the field of signal processing According to the Mallat‟s algorithm.
According to the above discussion, we give the recursive definition of the integer approximation of DWT as
The procedure for implementing multi-level DWT in the encrypted domain using is shown Fig.1.
B. Expanding Factor and Upper Bound
In order to implement DWT in the encrypted domain by need to consider some issues. One is whether we are able to recover Sj (k) from the decryption of E[Sj (k)] without error. Another is how to obtain the plain wavelet coefficient X j (k) when the recovery requirement is satisfied.
Fig.1 Block diagram of two-level DWT in the
encrypted domain.
3.3 Inverse Discrete Wavelet Transform In The
Encrypted Domain
:A new mechanism to reconstruct IDWT in the encrypted domain and provide an upper bound on the accumulated quantization error in the reconstruction.
A. Integer Approximation And Reconstruction
According to the fast algorithm proposed by Mallat in using IDWT is defined recursively as
Where hr (k) and gr (k) are the low-pass and high-pass reconstruction filter coefficients, respectively. In order to implement IDWT in the encrypted domain, the reconstruction filter coefficients hr (k) and gr (k) must be converted to suitable integers first
Without loss of generality, we assume that the integer reconstruction filter coefficients have the same quantization factor as the integer decomposition filter coefficients. Then the quantization process of the reconstruction filter coefficients is expressed as.
In Fig.2 we show the procedure for implementing IDWT
in the encrypted domain.
3.4 Reduce Data Expansion:
The data expansion problem and propose a method to remove the expanding factor when performing both DWT and IDWT.
A. Data Expansion in the Encrypted Domain
The data expansion results from two parts. One is the absence of the normalized factor 1/√2 the other is the quantization processes described by Each level of DWT (or IDWT) in the encrypted domain will expand the plain coefficients by a fixed factor, √2Q. The data expansion will become serious in three application scenarios. The first is the implementation of MRA in the encrypted domain. the expanding factor K will exponentially enlarge as the decomposition/reconstruction level increases. The second is the processing of multi-dimensional signals. Let i be the dimension of the input signal. Then K will increase exponentially as i increases. The third is the case where both DWT and IDWT are performed, as shown in Fig.3 which is very common in DWT-based signal processing, such as watermarking, compression, filtering, and feature extraction. In this case, the data expansion is twice the one obtained when single DWT or IDWT is performed.
Fig.3 Block diagram of ordinary signal processing based on DWT.
B. Rational Filter Coefficients Wavelets
Let us consider rational filter coefficients wavelets, such as the Haar wavelet, CDF 5/3 wavelet and biorthogonal spline wavelet family. We denote the least common multiple by L. When the quantization factor Q is the multiple of L, that is.
This assumption can be easily achieved for most rational filter coefficient wavelets, such as the Haar wavelet, the CDF 5/3 wavelet and the biorthogonal spline wavelet family.
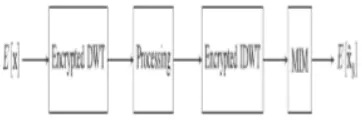
Fig.4 Block diagram of MIM. Encrypted DWT, encrypted IDWT, and MIM
MIM requires no additional information about x(k). It is applicable in the case that both DWT and IDWT are performed in the encrypted domain. The procedure of this method is shown in Fig. 4. Note that we cannot multiply some modular multiplicative inverse to remove the scaling factor (√2Q) j. The reason is that the wavelet coefficient X j (k).
C. Applications Of Mim
MIM can be used to improve the performance of some applications, such as information hiding, data compressing, and feature extracting, in the encrypted domain. Actually many DWT-based applications have the same model in mathematics, that is, first adding an additional signal to the DWT coefficients and then performing the IDWT on the modified coefficients.
In order to perform the processing based on DWT in the encrypted domain, one should apply a τ -level wavelet transform to the input signal E[x(k)] first.
Fig.5 Block diagram of MIM in the applications where some processing occurs between DWT and
IDWT.
MIM has a better performance in image processing than in one-dimensional √ signal processing, since the factor 2 can be removed when the input is 2D. We show the procedure of MIM in this situation in Fig. 5. If we treat MIM as part of the Encrypted IDWT in Fig. 5, then the procedure shown in Fig. 5 is essentially not different from the traditional processing procedure. For one who has not the decryption key, MIM will not provide any information about the encrypted data.
4. Performance Comparison
transform precision of each level are not changed during the processing, then the value of log2 N and log2 Q are fixed. we can obverse that MIM reduces the coefficient of the variable μ from 1 + 2 log2 Q to 1 + log2 Q. Therefore if the maximum capacity of the cryptosystem and the transform precision of each level is the same, then the value of μ will decrease more slowly with MIM than it does without MIM. In Fig.6 we compare the maximum capacity μ with and without MIM, where N and Q are assumed to be 21024 and 265, respectively. When τ = 8, the method without the multiplicative method will no longer correctly process any data in the encrypted domain.
Fig.6 Case of modifying the transform coefficients.
5. Results:
In this section, we investigate the use of our proposed technique and MIM for image processing.
A. Mim In Secure Image Processing
The grayscale image Fig.7 “Lena” of 512×512×8 bits is chosen as the plain signal. We exploit the 2D Haar wavelet as the wavelet basis in the experiments and choose two large prime numbers for the cryptosystem.
Fig.7 The grayscale image “Lena” of 512×512×8 bits is chosen as the plain signal Image
Fig.9 Image watermarking scheme based on Haar Wavelet transform in the encrypted domain.
Watermarking with MIM and Decryption of watermarking with MIM.
In our experiment, we use the same quantization factor Q = 264 for the Haar wavelet transform. A Gaussian noise is chosen as the watermark signal. After performing five-level DWT on the input encrypted image, we add the Gaussian noise as a watermark into the low frequency bands (LL) of the fivelevel coefficients by using the perform five-level IDWT on the modified results Fig.9 to obtain the watermarked image in the encrypted domain. The processed result and its decryption .The decryption looks the same as the expected watermarked image. In fact, there is only one scaling factor between the decryption and the desired image. it is easy to obtain the final watermarked image ˆ xy (k).
5. Conclusion
This paper has investigated the implementation of DWT and MRA in a homomorphic encrypted domain and tackled the problem of data expansion caused by quantization. We have proposed a framework to implement DWT and MRA in the encrypted domain by using homomorphic properties. Compared with plaintext DWT.in this using DWT method of the plaint value of the processed data. We have derived an upper bound on the expanded data, regardless of the kind of wavelet.
The rational filter coefficients wavelet transforms, we have presented a method to perform DWT/IDWT in the encrypted domain without any quantization error. MIM is proposed to remove the expanding factor without decrypting. The proposed method improves the capacity of signal We have investigated 2D Haar wavelet transform in our experiments. An example of image watermarking based on Haar wavelet transform in the encrypted domain has also been studied. The experiment results demonstrate the validity of our framework and the advantages of the proposed method. processing with the same cryptosystem parameters. The technique described in this paper and the proposed algorithm are suitable for secure multimedia applications, such as secure signal filtering, secure feature extraction, secure face detection and secure watermarking.
6. Future works
The Future method of two aspects. One is to address the issues regarding the storage and computation overheads induced by the homomorphic encryptions. It is necessary but very challenging to develop a method to reduce the storage overhead. A fast algorithm to speed up the computation in the encrypted domain is also very important. The other may be to extend MIM be a generalized method for other cryptosystems and other signal transforms, for example, the DFT in the encrypted domain.
[1] Bianchi.T,Piva.A, andBarni .M, “On the implementation of the discrete Fourier transform in the encrypted domain,” IEEE Trans. Inf. Forensics Security, vol. 4, no. 1, pp. 85– 95, Mar. 2009.
[2] Damgård.I and Jurik .M, “A generalisation, a simplification and some applications of Paillier‟s probabilistic public-key system,” in Proc. Public-Key Cryptography, 2001, pp. 119–135.
[3] Erkin.Z “Protection and retrieval of encrypted multimedia content: When cryptography meets signal processing,” EURASIP J. Inf. Security, vol. 2005, pp. 1–20, Jan. 2005.
[4] Elgamal.T“A public key cryptosystem and a signature scheme based on discrete logarithms,” IEEE Trans. Inf. Theory, vol. 31, no. 4, pp. 459–452, Jul. 1983.