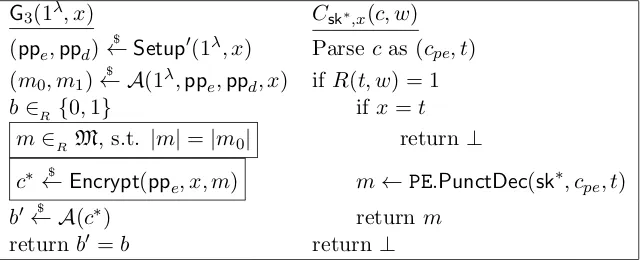
Offline Witness Encryption with Semi-Adaptive Security
Full text
Figure
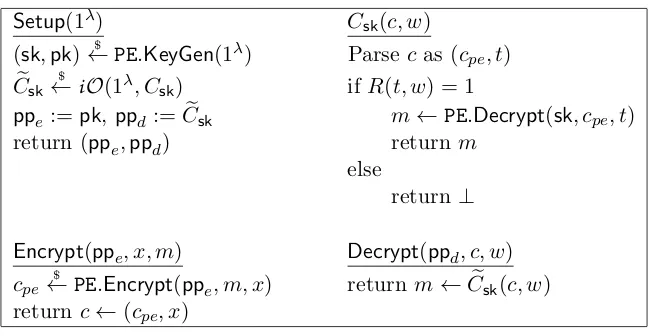
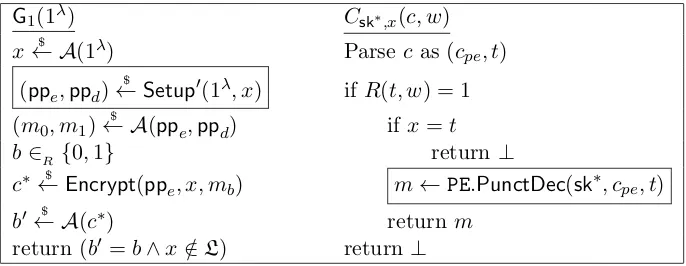
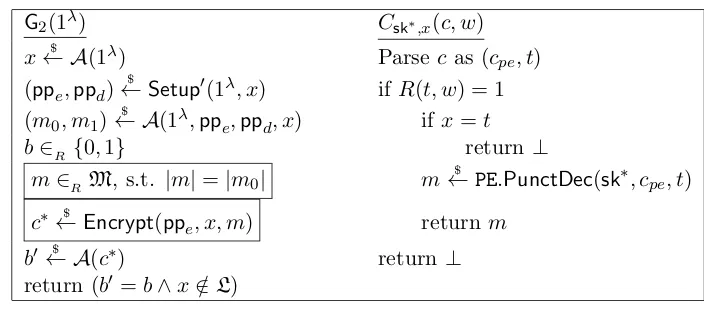
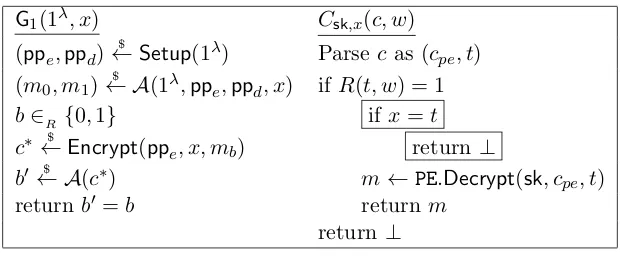
Related documents
Wu, “Half-mode substrate integrated waveguide transverse slot array antennas,” IEEE Transactions on Antennas and Propagation , Vol.. Chen, “45 ◦ linearly polarized resonant slot
Table 4 summarizes the results of an experiment designed to test the fate of larvae, both in the control and treated series which hatched during period R, as well as the fate
Chaining, tree-dozing, and root-plowing are used to control- redberry juniper in West Texas (Rechenthin et al. However, aerial applications of picloram at I. He
ABSTRACT : The issues identified with security and activity defeats by the Division and Replication of Data in the Cloud for Optimal Performance and
The thermal performance in natural convection from different geometrical fins being reviewed includes analysing the natural convective heat transfer from vertical fins, also
Because the number of occurrences of maltreatment experienced prior to age 4 proved to be a significant predictor of whether or not a child experienced recurrent maltreatment by
A variety of different instructional strategies using representations in science classrooms to develop systems thinking have been used with students ranging from elementary to
Transfer function of a system (in this case transformer) being dependent on frequency varies from its healthy signature and this variation detects occurrence of faults
![Figure 12: The Adapted Tag-Based Encryption Scheme of Kiltz KiltzTBE [Kil06]](https://thumb-us.123doks.com/thumbv2/123dok_us/7991390.1326445/20.612.102.510.292.594/figure-adapted-tag-based-encryption-scheme-kiltz-kiltztbe.webp)