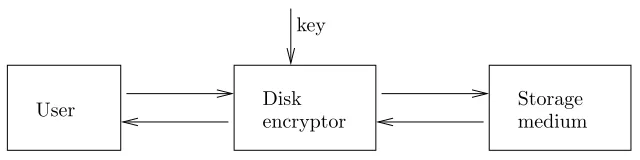
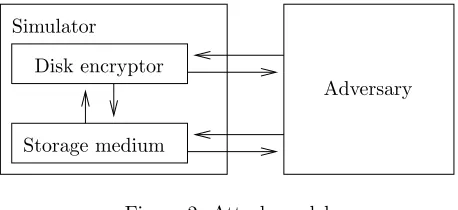
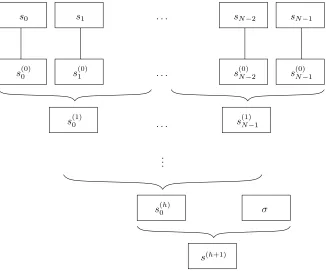
Security notions for disk encryption
Full text
Figure
Related documents
The majority of the students said that the coursebook objective was relevant to their needs, the contents were complete, the topics were interesting and were relevant
HCC is developing in 85% in cirrhosis hepatis Chronic liver damage Hepatocita regeneration Cirrhosis Genetic changes
The current study examined coping strategies utilized by individuals with SMI versus those with SMI-PTSD, while also investigating the role of PTSD symptom severity,
The summary resource report prepared by North Atlantic is based on a 43-101 Compliant Resource Report prepared by M. Holter, Consulting Professional Engineer,
An analysis of the economic contribution of the software industry examined the effect of software activity on the Lebanese economy by measuring it in terms of output and value
Students will knowledge of mechanism of action, route of administration, half-life and siden effects of different gases used to give anaesthesia. Students will have knowledge
Compared with the NTG group, preventive treatment with NLRP3 inhibitor MCC950 not only significantly decreased the protein ex- pression levels of IL-1β, but also decreased the
Student satisfaction measurements are performed that the distance education services provided to students consists of : (1) registration service which consists of 9 indicators,