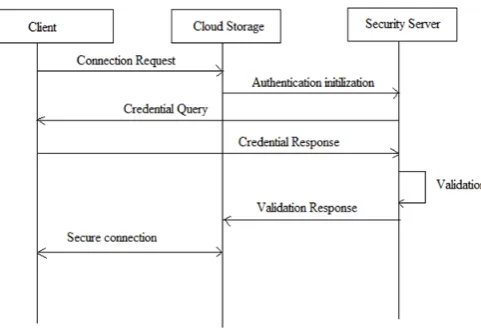
Architecture of Secure Cloud Data Center Storage
Full text
Figure

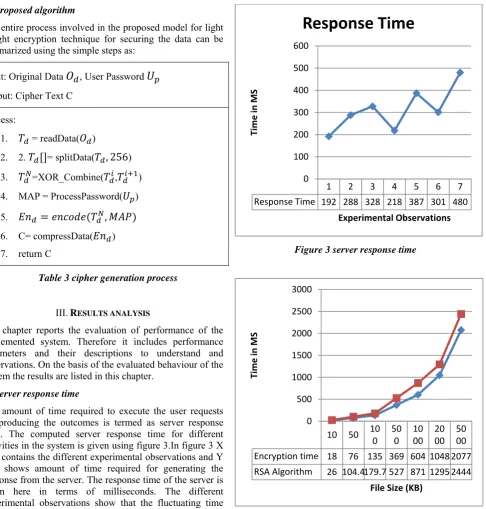

Related documents
Membranipora Lacroixii and Bowerbankia imbricata were taken up as far as half a mile above Halton Quay, where the salinity range from high to low water was approximately 210/00to
Table 3.2: List of the meteorological stations used in the simulations performed on Fort Cobb river basin. ID is the station identificative number, City is the closer city to
Labels for data points: 1 Adygey Republic, 2 Altay Republic, 3 Altaysky Krai, 4 Amursk Oblast, 5 Arhangelsk Oblast, 6 Astrahan Oblast, 9 Bashkortastan Republic, 10 Belgorod Oblast,
This framework inherits the characteristics of iCAM image quality measurement, and the color difference is calculated in the uniform color space IPT, which is the key part of the of
In this exploratory descriptive study, an investigator-developed survey tool was used to describe military clinical faculty’s perception of the characteristics that nurse
Exploring the contingent effect of the external environment, we found: (1) BM novelty provided greater performance benefits when the environmental dynamism was
This holds due to the following implications detailed in section 5: game universal implementation is equivalent to weak stand-alone security (our result), strong
This paper describes a dual voltage source inverter (DVSI) scheme, in which the power generated by the microgrid is injected as real power by the main voltage