DOI : https://doi.org/10.32628/IJSRCSEIT
The Internet-of-Things (IoT) Security : A Technological
Perspective and Review
Dr. Yusuf Perwej*1, Firoj Parwej2, Mumdouh Mirghani Mohamed Hassan3, Nikhat Akhtar4
*1Assistant Professor, Department of Information Technology, Al Baha University, Al Baha, Kingdom of Saudi Arabia
(KSA)
2Research Scholar, Department of Computer Science & Engineering, Singhania University, Jhunjhunu, Rajasthan, India
3Assistant Professor, Department of Computer Science, Al Baha University, Al Baha, Kingdom of Saudi Arabia (KSA)
4Research Scholar-Ph.D, Department of Computer Science & Engineering, Babu Banarasi Das University, Lucknow, India
ABSTRACT
Recent years have seen the swift development and deployment of Internet-of-Things (IoT) applications in a variety of application domains. In this scenario, people worldwide are now ready to delight the benefits of the Internet of Things (IoT). The IoT is emerging as the third wave in the evolution of the Internet. The 1990s’ Internet wave connected 1.2 billion subscribers while the 2000s’ mobile wave connected another 2.4 billion.
Actually, IoT is expected to consist of more than 84 billion connected devices generating 186 zettabyte of data by 2025, in the opinion of IDC. It includes major types of networks, such as distributed, ubiquitous, grid, and vehicular, these have conquered the world of information technology over a decade. IoT is growing fast across several industry verticals along with increases in the number of interconnected devices and diversify of IoT applications. In spite of the fact that, IoT technologies are not reaching maturity yet and there are many challenges to overcome. The Internet of Things combines actual and virtual anywhere and anytime, fascinate the attention of both constructor and hacker. Necessarily, leaving the devices without human interference for a long period could lead to theft and IoT incorporates many such things. In this paper, we are briefly discussing technological perspective of Internet of Things security. Because, the protection was a major concern when just two devices were coupled. In this context, security is the most significant of them. Today scenario, there are millions of connected devices and billions of sensors and their numbers are growing. All of them are expected secure and reliable connectivity. Consequently, companies and organizations adopting IoT technologies require well-designed security IoT architectures.
Keywords : Internet of Things (IoT), Sybil Attack, IoT Authentication, IoT Trust, IoT Protocols, IoT Security
I. INTRODUCTION
The size of computer systems has diminished drastically over the years, from mainframes encompassing whole rooms, via desktop computers, and down to smart cell phones [1]. At the turn of the century, a new concept appear called the Internet of
Things, envisioning all “things” in the world
Internet of Things today is consolidation of data, and responding to the collected data in a useful way [3]. While connecting all our things to the Internet will permit us to advantage insight into our lives and environment, we can potentially permit others to advantage the same insight if security is not managed correctly. A couple of security anxiety on a single device like as a mobile phone can swiftly turn to 60 or 70 anxiety when considering multiple IoT devices in an interconnected business or home. In light of the significance of what IoT devices have access to, it is an essential to understand their security peril [1].
The Internet of Things (IoT) [4] enables everywhere communication between various devices. From entering patient details to watch post-surgery, from parking vehicles to tracking vehicles, from childcare to elder care, from smart cards to near field cards, sensors are making their impendence felt. Sensors play an important role in the IoT as well. In spite of, the functionality and operations of the IoT heavily depend on the underlying network connectivity structure. In the opinion of Gartner [5], it is required that the number of Internet connected devices will increase from around 28 billion to 50 billion by 2020. In spite of the IoT features everywhere communication [6] among all kinds of electronic devices, it inevitably raises security concerns due to seamless infiltration and automated integration among all sorts of applications. The IoT works across miscellaneous networks and standards. Security and privacy are considered the most important IoT challenges [7]. In particular, no network is free from security threats and vulnerabilities. Each of the IoT layers is uncovered to various types of threats. In the opinion of Gartner [8] security and risk, concerns will continue to be the greatest hindrance to IoT adoption. The market for IoT distinguished security solutions will dramatically expand in 2017 as current security providers aggressively retool present capabilities to address IoT security risks IoT devices have often limited resources and may be more
exposed to attacks by malicious opponent [1]. An invasion may compromise an IoT device and use it as a platform for launching invasion on other IoT devices. IoT security introduces technological defiance at the device, network and platform level. Therewith, there is the process challenge of organizing the security technologies in an end-to-end manner. One thing is certain, when evaluating security necessity is that, then IoT is still very much a work in progress. This paper provides an overview of Internet of Things (IoT) stage in section 2. We are briefly discussing Internet of Things (IoT) threats in section 3, and in section 4, we describe Internet of Things scheme. We categorize the reliance in section 5. In section 6, we discuss public key infrastructures in Internet of Things. In section, 7 and 8 Internet of Things design thought for digital certificates and protocols. In the last section discuss guidelines for secure the IoT devices.
II. INTERNET OF THINGS (IoT) STAGE
The IoT requires five stages, from data collection to data delivery to the end [1] users on or off demand, as shown in figure 1.
Figure 1. The Internet of Things (IoT) Stage
modify the physical conditions that generate the data. The thing may be a constant body (body sensors or RFID tags) or a dynamic vehicle (sensors and chips) [10]. The actuating and sensing stage involucre everything from legacy industrial devices to robotic camera systems, water-level detectors, heart rate monitors, accelerometers, and air quality sensors. In the secondly data collected on stage first should be stored and making it obtainable for analysis. If the thing has its own local memory, data can be stored [7]. The different technologies are appropriate for this purpose, depending on the scenario. The high performance storage solutions are suggested for companies performing data analysis with the distributed system Hadoop. Normally, IoT components are installed with low memory and low processing potential [1]. The cloud takes over the answerability for storing the data in the case of stateless devices. In the thirdly stage, IoT analyzes the data stored in the cloud DCs and provides intelligent services for work and life in hard actual time as well as analyzing and responding to queries, then IoT also handle things. The IoT proposal for intelligent processing and control services to all things homogeneously. In the fourth, data transmission happen in all stage for instance sensors, RFID tags [10], processors to controllers, devices, DCs to processing units, and end users. In the fifth stage, delivery of processed data to things on time without errors or transformation is a sensitive task that must always accomplish.
III. INTERNET OF THINGS (IoT) THREATS
The IoT devices have several applications that are designed to make life convenient and effortless. Think of engineers being able to access a device, perform remote diagnosis and remediation any problem. This is after the device has informed the engineering team of an imminent problem before it becomes a major problem [11]. As you can predict, with this data exchange over the internet come
security problems. In the future, maybe around the year 2020 with IPv6 and the 5G network, billions of miscellaneous things will be part of the IoT. Privacy and security will be the major factors of worry at that time [12]. IoT security threats and attacks will escalate as the IoT devices become everyday events. The security threat is high enough for Gartner to estimate spending on IoT security is required to reach near $600 million in 2018. In this [13] report, prophecy that 30% of attacks in enterprises will include IoT. In this section, we are discussing security problems in three dimensions, components, based on stage, and architecture.
3.1 The Components Based Incursion
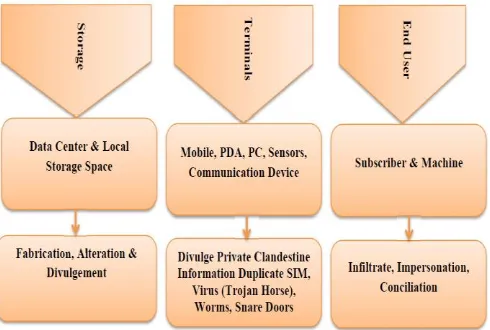
As a technology, IoT is peerless since it has a role to play in consumer, industrial worlds and enterprise. The things are diverse in nature, communicating sensitive data over a distance [13]. The Internet of Things (IoT) is extremely heterogeneous, highly dynamic, always available, [7] and consequently always vulnerable to attack. Apart from attenuation, stealing, loss, violation, and disaster, data can also be [1] concocted and modified by compromised sensors. The figure 2 shows the types of attacks at the component level in IoT.
3.2 The Stage Based Incursion
The diversify kind of attacks on the five stages of IoT. Data effusion, sovereignty, [14] violation, and authentication are the major concerns in the data perception phase.
3.2.1 Data Effusion
The data is a precious resource, and if recent events surrounding the allegations against (for instance, Cambridge Analytica) demonstrate anything, it is that you cannot always trust companies to manage such data responsibly. Specifically, device manufacturers are in a prime position to potentially abuse [14] IoT generating data. Data effusion can be internal or external, intentional or unintentional, authorized or spiteful, involving hardware or software. Data effusion is a solemn threat to reliability. As the cloud data move from one renter to several other renter of the cloud, there is a sedate risk of data effusion.
3.2.2 Data Sovereignty
Internet of Things (IoT) connections growing from 9 billion in 2017 to 24 billion by 2020, it is vital to understand the potential influence data sovereignty will play for organizations collecting and sharing
customer’s individual information. International
organizations are now often moving big data across borders for analysis and consolidation [2]. Data sovereignty is the idea that information which has been transformed and stored in binary digital form is subject to the laws of the country in which it is located. The IoT encloses all things across the globe and is hence responsible to sovereignty.
3.2.3 Data Authentication
The data can be perceived from any device at any moment. The powerful IoT device authentication is
needed to make sure connected devices on the IoT can be trusted to be what they intend to be. Accordingly, each IoT device needs a distinctive identity that can be authenticated when the device effort to connect to a main server or gateway. With this distinctive identity in place [15], IT system administrators can track every device throughout its lifecycle, communicate securely with it, and inhibit it from executing detrimental processes. If a device shows unforeseen behavior, administrators can simply revoke its perquisite [16]. In addition, it is compulsory to verify that the data do not change during transit. Data authentication could endow originality and integrity.
3.2.4 Data Mislay
Data mislay considered a primus risk for the Internet of Things. The data mislay dissimilar from data effusion in that the latter is a sort of revenge taking action on the employer or administrator. Data mislay is losing the work accident due to hardware or software, lack of success and natural calamity.
3.2.5 Attack on Availability
The Internet of Things continues to increase, which
in turn spread your organization’s attack surface.
usually work is not available. There can be many factors for unavailability, but it generally refers to an infrastructure that cannot cope due to capacity overload [18]. In a Distributed Denial of Service (DDoS) attack, a huge number of systems spitefully attack one target. This is often done via a botnet, where many devices are programmed to entreaty a service at the same time.
3.3 The Architecture Based Incursion
The IoT will generate data at various locations for various end users, including the enterprise, its subscriber and partners, network segmentation and segment-based topologies are expected to protect against extensively attacks. The various vendors and applications adopt their own layers. Now, we are discussing the possible threats to each layer in IoT.
3.3.1 Exterior Attack
The IoT is a bit of a buzzword right now. It is a used as a catch all for everything that layers physical devices like as computing infrastructure, sensors, networking, storage, application [14] capabilities. The organizations purposely offload both confidential and non-confidential data to obtain the services. However, they do not know of the location where their data will be processed or stored. It is possible that the provider may share this information with others, or the provider itself may use it for spiteful actions.
3.3.2 Wormhole Attack
The wormhole attacks considered as the grievous attacks during IoT routing. In this attack, tunnel is established between two nodes and the packet is forwarded among each other. These distant spiteful nodes make believe that they are very close to each other so that vicinal nodes forward packets via them. If wormhole attack is triggered in the more number
of vicinal gets formed and these new vicinal [19] are all from other end of wormhole tunnel and not in transmission range of node therefore, during the attack lots of control packets are going to exchange from one end of the tunnel to the other in that vicinal advertisement. Wormhole attack is very strange and arduous to identify. The figure 3 shows the wormhole attack on IoT.
Figure 3. The Wormhole Attack in Internet of Things
3.3.3 Brute-Force Attack
A brute force attack is the cyber-attack compeer of trying every key on your key ring, and in conclusion finding the right one. This type of attack depends on a trial and error technique in order to get information like as user passwords or personal identification number (PIN). The brute force attack uses [20] automated software to generate a large number of sequential guesses to decrypt the cipher text. The criminals to crack encrypted data may use brute force attacks.
3.3.4 Man-in-the-Middle Attack
the faith that they are communicating directly with each other. As the attacker has the genuine communication, they can trick the recipient into thinking they are still getting a rightful message. Man-in-the-middle attacks can be succinct in many ways, including MITM, MitM, MiM and MIM.
3.3.5 Sinkhole Attack
The sensors, which are leave unattended in the network for long periods, are mainly susceptible to sinkhole attack. The compromised node attracts the information from all the neighboring nodes. Thereby, the intruder posts other attacks, [21] such as selective forward, fabrication, and transformation.
3.3.6 Botnet Attack
A botnet is a collection of Internet-connected computers whose security defenses have been infarct and control ceded to a spiteful party. Each such
compromised device, known as “bot” is created,
when a computer is infiltrated by [22] software from a malware distribution, else cognize as malicious software. The controller of a botnet is able to direct the concern with of these compromised computers via communication channels formed by standards-based network protocols such as hypertext transfer protocol (http) and internet relay chat (IRC).
3.3.7 Side-Channel Attack
Most IoT objects, for security intent, will be integrated with some of security mechanisms such as an encryption to protect their confidential data. The side channel attack, [23] is intended to break such mechanisms by analyzing side channel information emitted by IoT objects. In this context, power and time analysis attacks are some examples of such type of attacks.
3.3.8 Sybil Attack
The impersonation is a threat in which malicious nodes alter the data flow route and tempt the nodes to the wrong positions. In Sybil attack, a malicious user dissimulates to be a separate user after acquiring multiple identities and tries to create a relationship with a truthful user. If the malicious user is successful in compromising one of the truthful users, the attacker gains unauthorized privileges that help in the attacking process [24].
3.3.9 Social Engineering Attack
Social engineering is the act of manipulating people so they give up secret information [25]. The types of information that criminals are seeking can vary, but when individuals are targeting, the criminals are usually an effort to deceive the user into giving them passwords or bank information. Alternatively, they could be effort to access a computer in order to stealthily install malicious software that will then give them access to confidential information, as well as giving them control over the computer.
3.3.10 Hello Flood Attack
In Hello flood news attacks, every object will familiarize with Hello messages to all the vicinal that are reachable at its frequency level. A malicious node will cover a wide frequency area, and hence it becomes a vicinal to all the nodes in the network. Thereupon, this malicious node will also broadcast a Hello message to its entire vicinal, make an impression the availability. Flooding attacks cause non-availability [26] of resources to rightful users by distributing a large number of nonsense requests for a few services.
3.3.11 Data Insertion Attack
attacker could insert some data into this data only, if the object needs a long time to reply [27]. The well-turned insertion could only happen if the inserted data can be conveyed, before the original device starts with the answer. If both data streams overlap, the data will be unserviceable.
3.3.12 Flash Crowd Attack
A flash crowd is fundamentally an unexpected increase in the overall traffic to any specific web page or website on the Internet and the unexpected occurrence of any event that triggers that particular massive traffic of people accessing that web page or website. Less robust sites are unable to cope with the large increase in traffic and become not available [14]. The general causes of flash crowd or lack of sufficient data bandwidth, servers that collapse to cope with the huge number of requests, and traffic quotas.
3.3.13 IP Spoof Attack
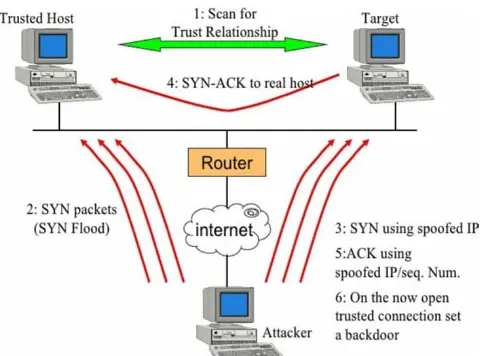
Spoofing is a type of attack in which the attacker dissembles to be someone else in order to gain access to prohibit resources or thieve information. This type of attack can take a [28] diversify of different forms, for example; an attacker can act the IP address of a authorize user to get into their account. IP address spoofing, or IP spoofing, refers to the creation of IP packets with a counterfeit source IP address, called spoofing, with the purpose of concealing the identity of the sender or imitate another computing system. The figure 4 shows the IP Spoof attack.
Figure 4. The IP Spoof Attack
3.3.14 Eavesdropping Attack
Eavesdropping is obstructing of network traffic to gain prohibited access. It can outcome in lack of success of confidentiality. The man in the middle attack is also a category of eavesdropping. Eavesdropping attack observes the packets transmitted between objects and servers during the firmware [29] upgrade process. The attacker could only get confidential data if the packets are either weakly keeping safe or not keep safe at all.
3.3.15 Object Tampering Attack
The likelihood of accessing IoT objects physically by attackers is very high because some IoT objects may bring into service in stoic environments. Consequently, such objects are vulnerable to hardware attack, the most [30] renowned ones are the extraction of cryptography keys, the modification of operating system or firmware, and the circuit transformation.
IV.INTERNET OF THINGS (IoT) SCHEME
to share information and coordinate decisions. In spite of, the functionality and operations of the IoT heavily depend on the underlying network connectivity structure [1]. The IoT characteristic ubiquitous communication among all kinds of electronic devices, it inevitably raises security concerns due to seamless infiltration and automated integration among all sorts of applications. Consequently, efficient and effective defense mechanisms are of the paramount importance to make sure the reliability of the IoT [31].
4.1 Sequential Scheme
A sequential defense scheme is proposed by that sequentially collects feedbacks from high degree nodes for attack presumption. The benefit of sequential defense is that there is no necessity to acquire feedbacks from all nodes, and it abolishes the collection process once sufficient feedbacks have been collected for attack presumption. The huge network size renders concurrent data transmissions infeasible, particularly for wireless networks with scarce radio resources [32]. Besides, due to the huge network size and limited computational power, analyzing the collected information from all nodes incurs terrible computation overheads and it may default to [33] provide timely safeguard. It is reaffirming in that a relatively small fraction of feedbacks is enough to detect fatal attacks on the network prior to network interruption.
4.2 Topological Scheme
A topological defence scheme permits alteration of network topology to enhance network resilience [34]. It has been established in that by swapping a small number of edges in the network topology, one is able to significantly make better network resilience without including extra edges. Moreover, the proposed edge rewiring technique in can be executed in a distributed fashion, which is especially advantageous for the IoT due to scalability.
4.3 Friend Relationship Sybil Scheme
In a mobile network, due to the mobility and the deficiency of global social graph information, Sybil defense is completely different and arduous compared with that in the online networks [24]. Quercia and Hailes propose an MSD scheme to match mobile user communities and label the users from the Sybil community as Sybil attackers [35]. In, one imagination is that each mobile maintains two lists, first familiar list containing the trusted mobile users, and second foe list with the unfaithful users in it. In view of the fact that two users are encountered in the network, they match their communities. If a user were not in the trusted communities, this user would be reckoned as a Sybil user. In [36], Chang et al. also propose a Sybil defense scheme in MSNs, assuming that the Sybil users and normal users happen in various communities, and rely on the community analogous to detect the Sybil users [24]. Therefore, leveraging rapprochement is an effective solution to detect Sybil attackers. Although, this type of FR-MSD schemes need mobile users to maintain the faithful community information in advance.
4.4 Fusion Scheme
A fusion-based defense mechanism is proposed to deduce the presence of an attack [37] based on the response from each node. The response information can be as simple as a binary status report reflecting that each node is, or is not, under attack, based on the node-level detection capacity [38]. The network level attack presumption plans are carried out at the fusion center [39]. A two-player game between the protector and the attacker is naturally formed, given the critical value of network resilience and the node-level detection configurations. Intuitively, from the
detected by the fusion center, which means that the attack is eventually in futile. From the protector point of view, inferring attacks using all feedbacks might treat the topological attack as a fabled alarm, since only a small subset of nodes are targeted. On the other hand, inferring attacks using only a few feedbacks might tolerate from information insufficiency and therefore fabled to detect the presence of attacks [40]. Accordingly, there exists a balance point at which both attacker and defender are contented with their own master plan, which is precisely the notion of Nash equilibrium in game theory. As an outcome, the game payoff at game equilibrium can be used to study the robustness of a network.
V. INTERNET OF THINGS (IoT) RELIANCE
The Internet of Things (IoT) can deliver important advantage to our society and economy, enabling superior health services, cleaner and secure societies, more dexterous industries and [41] stimulating new businesses. On the other hand, data is a sensitive subject and customers and end users are wary of sharing data for apprehension that it will fall into the hands of criminals, or using in ways they consider inappropriate [42]. Faith is the oxygen, which will breathe life into the internet of things. Industry necessity to show data is secure and that it is properly treated [43]. Faith and security are based on tokens or credentials, provided by a faith management infrastructure, which are embedded in and potentially shared between devices. The aim of this section is to investigate frameworks that ensure faith as well as communication security between nodes in an IoT deployment [44].
5.1 Reliance and Security from a Device Point of View
IoT devices are vulnerable in many sides, so providing and maintaining faith and security is an
arduous endeavor. On the physical level, device enclosures are frequently not tamper proof devices can be unlocked and their hardware can be accessed via investigate and pin headers [45]. The device central processing units (CPUs) are low-cost components that frequently have no sophisticated means to protect their code, data, and tokens for external access. This permits an attacker to clone entire devices or manipulate software and data. If the device is brought into service in an unsupervised environment, it may be accessed and frame up by a malicious third party without information. Besides, IoT devices are frequently based on low-power hardware and may only be able to process tokens with a low complexity. This can have an implication on the robustness of a token, as it can be reengineered or recovered through a brute force attack. As an outcome of this, any faith management system for IoT deployments must have the ability to dynamically withdraw faith of individual devices. When faith and security credentials given out at the time of manufacturing or deployment, a device is seen as initially honest. A network wide update mechanism will ideally incorporate a smooth and effective patching process, which contains robust integrity and authenticity examine, minimize service outages, and permits for a version withdraw if needed.
5.2 Secure Key Storage
The secure storage provision to increase the robustness of reliance tokens used both within an IoT system and within its reliance management infrastructure [46]. Passive keystores endow a means to securely save and retrieve credentials cryptographic operations are carried out [10] outside these stores by
5.3 Reliance and Security from a Network Point of View
During the operation of a network, devices set up stable or unstable communication links with other peers. These links can be either point-to point or
incorporate a group of nodes. From a device’s point of
view, the challenge [47] is to validate the authenticity and authority of the other peer and to set up a secure communication link to keep away from attack scenarios. For this objective, reliance tokens are interchange and validated or new session tokens bring into being. The promise of data integrity, optionally in combination with data confidentiality through [48] encryption, provides trustworthiness in the data a node sends or receives. Data integrity and confidentiality provide a foundation to deal with the principal attack vectors of interception, transformation and disruption. The data secrecy is generally conferred through symmetric encryption with the advanced encryption standard algorithm as a de facto industry standard often implemented directly in hardware. While data integrity confers through message authentication codes or cryptographic hashes that are attached to the data payload [48]. The peer authenticity belonging to the problem of how a peer
can validate another peer’s identity before a
communication link is established. Peer authenticity can go hand in hand with system availability. For instance, denial-of-service (DoS) way attacks are typically external attacks, so the ability to qualify and if necessary to discard data or connection requests [14] at an early stage can help to reduce such attacks. Proof of authorization provides commitment that a peer has the authority to communicate with another peer and conduct a few actions.
VI.PUBLIC KEY INFRASTRUCTURES (PKIs) IN INTERNET OF THINGS
At present, there are more things (devices) online than there are people on the planet. The devices are
the number one users of the Internet and necessity to digital identities for secure operation. As enterprises seek to transform their business models to stay competitive, swift adoption of IoT technologies is creating increasing demand for Public Key Infrastructures (PKIs) to confer digital certificates for the increase number of devices and the software and firmware they run [49]. The secure IoT deployments need not only faith the devices to be authentic, but also faith that the data they collect is real and not changed. If one cannot fault the IoT devices and the data, there is no point in collecting, running analytics, and executing decisions based on the information gathered.
6.1 The PKIs Elements
A public key infrastructure confers the revocation, distribution, revocation and verification of public keys used for public key encryption, and enables linking of identities with public key certificates. The public key infrastructure describes the policies, the procedure, the hardware, the software, and the people that are used to handle digital certificates [50]. This means the process of creating, distributing, handle, storing, and revoking certificates are all encapsulate under PKI. The PKI also mention to the associations we make with a public key to a person, or a public key to a device. It is based on faith, and a certificate authority creates this faith. This key management lifecycle starts with the creation of a key [51]. We make up one's mind on a distinctive strength of the key, which would be a certain number of bits, and we make up one's mind what cipher we would like to use to create the key. Now, we are discussing the PKI elements.
6.1.1 The Certification Authorities
and other existence. Generally known as certificate authorities (CA), these entities provide promise about the parties identified in a PKI certificate. Each CA keeps going its own root CA, for use only by the CA. The certification authority browser forum, also called a CA & browser forum, is an industry coalition founded in 2005 and whose members contain [51] CAs, browser software publishers and other system contributor, who use X.509 digital certificates for authentication and encryption. The CAs forms the backbone and the faith anchors of a PKI. They problem certificates and, in many cases, repeal status data regarding the certificates they problem, and publish both types of products.
6.1.2 The Registration Authorities
The registration authorities (RAs) act as the front end of certification authorities. A registration authority, often called a subordinate CA, problem PKI certificates. The registration authorities are certified by a root certificate authority and authorized to issue certificates for distinguished uses permitted by the root. That they are accountable for identifying and authenticating entities that request certificates, and then dispatching certificate requests to CAs and routing back the certificate(s) to the implore entity. In some instance, RAs are just a unique component of CAs.
6.1.3 The Validation Authorities
A certificate database stores information about controversy certificates. Therewith, to the certificate itself, the database includes validity period and the status of each PKI certificate. The validation authorities (VAs) permit for the validation of certificates. Validating a certificate in fact comprises many steps for instance; possibly acquire certificates, verifying signatures, checking the revocation status.
It’s normally supposed that VAs only provides services in connection to check revocation status,
typically through online certificate status protocol services.
6.1.4 The Central Directories
The central directories protect location in which are stored and index keys [50]. The central directories make certificates accessible to other entities. Since other data, such as policies or CRLs necessity to be published as well, central directories store and make all these data accessible. They are frequently executing as lightweight directory access protocol servers.
6.1.5 The Time Stamping Authorities
When the date and time of the phenomena is recorded, we say that it is time stamped. A digital camera will record the time and date of a photo being taken, a computer will record the time and date of a document being saved and emended. These are all instances of a timestamp. Timestamps are essential for keeping records on when information is being reciprocity, created, or destroyed online. In many situations, these records are simply utilitarian for us to know about. However, in some situations, a timestamp is more valuable. The time stamping authorities are characterized by their ability to problem PKI based believable timestamps. Believable time stamping is a process that keeps track of the creation and alteration of data. This data can be a program or a document. This process is done in a trouble free manner and recorded so that no one cans alteration the data, including the owner, without being informed and it assurance the integrity of the data.
6.1.6 The Certificate Revocation Authorities
expiration date and should no longer be believed. The CRLs is a type of blacklist and are used by different endpoints, including web browsers, to confirm whether a certificate is valid and trustworthy. In general, invalidate duties are carried out by a dedicated service that belongs to each certificate authority. While either the number of issuing certificates is high, or the complexity of invalidate procedures increases, or so does the number and diversification [51] of CAs, specialized authorities, CRAs, come to play, whereby a single, centralized CRA can replace equivalent invalidate services on multiple CAs. When a web browser makes a connection to a site using TLS, the web server's digital certificate is investigated for anomalies or difficulty, part of this process involves investigating that the certificate are not catalogued in a certificate revocation list. These investigate are arduous steps in any certificate-based transaction because they permit a user to calibrate the identity of the owner of the site and discover whether the CAs still considers the digital certificate believable.
6.2 The IoT Challenges in PKIs
PKI for IoT needs to be dissimilar than an enterprise PKI. The majority of devices collect transmit and has at least one piece of private, confidential or proprietary information [47]. Some devices will cross-unencrypted network and cloud services with varying security levels and requirements. Some devices will be physically inaccessible. Other devices may be attractive to impersonate in order to [14] gain access to IoT system resources. Comprehension the following difficult situation can help organizations plan certificate policies upon which the PKI environment will be based.
6.3 In the IoT Authentication, Integrity & Confidentiality
The connected IoT endpoints share coequal security requirements [47]. A faithful or device identity, confirm applications and data secured in motion and at rest. These needs translate to authentication, signature and encryption [52]. The industrial sector has placed greater trust on digital certificates for IoT system elements such as controls, applications, sensors, devices, switches, and data [23]. The countless commercial operations, systems and infrastructure are before controlled through the Internet. Many devices that use the sensors and actuators should follow particular policy and proxy rules for authentication to authorize the sensors to public their information [53]. Meantime, low cost solutions in this field have not been conferred as much as needed. At the present, if we want to confer the security for the sensors we have to use high-cost solutions, which is a dispute with the primary goal of IoT to provide lightweight protocols. The need for particular commitment and related controls is greatly increased for both industrial and consumer-driven IoT devices. The security is very critical, and one of the key distinctions between an enterprise PKI and an IoT PKI is the necessity for protecting data and safe authentication at multiple endpoints. In this context, digital certificates are an increasingly famous solution for signing, encryption and authentication.
6.4 Need the IoT Device Authentication
6.5 Need the IoT Device Connected Trouble Freely
To trouble freely participate in the IoT, each connected device needs a distinctive identity even before it has an IP address. This digital credential
establishes the root of faith for the device’s entire
lifecycle, from initial design to deployment to freedom from work. The every device a distinctive identity using the powerful cryptographic processing, key shielding, and key management available. A digital certificate is injected into every device enable to firstly, authentication of each device introduced to
the organization’s architecture. Secondly, verification
of the integrity of the operating system and applications on the device level. Thirdly, secure communications between devices, gateway, and cloud. Lastly, authorized software and firmware updates, based on approved code.
6.6 The PKI Security Guarantee in the IoT
The guarantee in the PKI space can be defined as the amount of confidence that a person or system has that the identity being introduced in a certificate in fact be suited to the device. Maintaining specific levels of guarantee across millions of deployed device identities is no trivial task. Risks must be comprehensible and mitigation plans established and executed. The IoT system may incorporate millions of diverse connected devices sharing data to complete various tasks, it makes sense that peril be inclined to be greater for an IoT system than for an enterprise use case. The higher IoT peril’s profile, the PKI
environment needed to issue believe certificates across the system endpoints warrants very careful security planning to make sure a distinctly defined level of promise for device authentication. The reliability promise applies to both enterprise and IoT PKIs and various use cases may rely on varying levels of promise. Some use cases need to define, detailed and strict promise requirements, while others may require less definition. Organizations must define in
certificate policy the suitable amount of promise so that relying parties know why the certificate is considered faith, as well as to understand what the device is authorized to do and not to do.
VII. TERNET OF THINGS (IoT) DESIGN IDEA FOR DIGITAL CERTIFICATES
In a digital identity certificate, both its owner and the CA that signed the certificate must be distinctively identified. While there will be a comparatively small number of CAs, there is a need for a scalable naming scheme appropriate for billions of nodes. In the design idea, device identifier establishment plans can be based on a different technique. These techniques incorporate either a hierarchical identifier, the encoding of extra information, unsystematic data, and the use of cryptographic operations [54]. In the design idea, certificate validity the X.509 certificates have a limited life span, which is enciphered in the validity field [55]. The field accommodates the two date’s
notAfter and notBefore, both accommodates a timestamp in the UTCTime encoding format. Investigation the validity of a certificate requires access to actual time [56], and since low cost oscillators found in embedded, systems have an important drift in the order of up to many. Seconds per day, the use of time synchronization protocols like network time protocol or precision time protocol should be believed. In the design idea, the public key cryptosystems confer pairs of keys, whereby the public encryption key dissimilar from the secret decryption key [51]. Such cryptosystems are at the core of PKI, as they confer a means to digitally, the
hash value of a digital certificate using a CA’s private
key; provide a means to confirm the integrity of a digital certificate, through decoding the already. The
encoded hash value using a CA’s public key and
string of variable length into a fixed-length hash value. They are utilizing to digital signs a certificate [57]. In the hash, functions have four essential mathematical and algorithmic characteristic, first they should have a small computational complexity, second irreversible
“one-way” functions, third infeasible to alter an input without changing the hash and fourth it must be infeasible to find two dissimilar inputs with the same hash. There are a number of various future-proof hash algorithms in use, most particularly 2 and SHA-3 with customizable hash lengths of between 224 and 512 bits.
VIII. INTERNET OF THINGS (IoT) PROTOCOLS FOR ACCESS NETWORKS
The Internet of Things (IoT) goal to make better our lives by increasing the interconnectivity of an increased variety of embedded computing devices using components of existing Internet infrastructure [1]. This will permit for communications between sensors in cars, laptops, factory, home appliances, mobile phones, machineries, and many other devices that are already capable of network access through existing protocols such as 3G, Wi-Fi, Bluetooth [58], and ZigBee. The IoT scenarios remain a challenge, mainly due to the large number of miscellaneous devices as well as data exchanged via insecure connections. Moreover, the concepts of security are extended not only to device-to-device communications, but also to network aspects. As an example, many hackers create fake networks (termed botnets) to steal data and user privacy information. Normally, various security requirements should be addressed to promise network, and data security. First, confidentiality is essential to limit network access and data only to authorized users. Second, data integrity and authentication should be promise so that messages are triumphantly transmitted and are reliable to the receiver. In the end, data authentication and availability should be provided, as well as detection of malicious interloper [59]. In IoT
scenarios, a number of technologies have been developed to achieve information privacy and security objective, such as transport layer security, which could also make better the confidentiality and integrity of the IoT.
8.1 In IoT Secure Device Provisioning and Authentication Using Azure
The security token technique provides authentication for every call made by the device to the IoT hub by associating the symmetric key to each call. The X.509-based authentication permits authentication of an IoT device at the physical layer as part of the TLS connection establishment [60]. The security token-based method can be used without the X.509 authentication, which is a less safe pattern. The preference between the two techniques is primarily dictated by how safe the device authentication needs to be, and availability of safe storage of the device. IoT hub uses security tokens to authenticate devices and services to keep away from sending keys on the network. Besides, security tokens are limited in time validity and scope. Azure IoT SDKs automatically generate tokens without need any special configuration [61]. Some scenarios need the user to generate and use security tokens outright. These scenarios contain the direct use of the AMQP, MQTT, and HTTP surfaces, or the implementation of the token service pattern.
authentication at the physical layer. The private key is stored securely in the device and is not detectable outside the device. The X.509 certificate contains information about the device, like as device identification, and other organizational details. A signature of the certificate is originated by using the private key. Internet connection between the IoT device and IoT hub is secured using the transport layer security standard. Azure provides for IoT transport layer security standard, namely TLS 1.2, TLS 1.1, and TLS 1.0, in this order.
8.2 The Secure Access to Unidirectional Data in IoT
The unidirectional devices cannot perform any safe procedure for secure key exchange with the negotiator. The transmitter just sends a message without any feedback, that is, it lapses to receive any signal, and is equipped with an internal clock, which is supposed not to be on the mark. Then, a nonspecific non-IP unidirectional terminal runs the following move to send data to the gateway and negotiator in a safe way. In the first move, it generates the encryption key locally, based on the time measured by a local clock. In the second move, it creates the message and encrypts it with the generated key, this message includes the payload and any other data to be used to make better security. In the third move, it computes the hash values using the message text and the generated key and attaches them to the message. At the end move, it sends the message to the gateway and negotiator.
8.3 The Secure Access to Bidirectional Data in IoT
For bidirectional terminals, the negotiator can periodically broadcast its clock timing in a dedicated message, and its identification in the plain part of the message. The terminals can align their local clocks to the gateway and negotiator terminal, and then generate the security keys in accordance with the algorithm already described [62]. Since devices are
close to the gateway and negotiator, propagation delays can be ignored. In addition, for the unidirectional case, the security keys have a valid time interval sufficiently long to transmit one or more packets and to absorb possible retransmissions or any other undesirable latency.
IX. GUIDELINES FOR SECURE THE INTERNET OF THINGS DEVICES
The Internet of Things is comprised of an indiscriminately diverse range of device types from small to huge, from simple to complex, from consumer gadgets to state of the art systems found in DoD, [1] utility and industrial and manufacturing systems. IoT devices face the same types of privacy and security problem that many traditional end-user devices face. There are approx six million new things being connected every day in 2016, as we head toward more than 22 billion by 2020, according to Gartner [5]. End users do not have the technical specialist to assess the privacy and security implications of any particular IoT device, or they may lack interest in doing so [63]. The subscribers already have trouble identifying and troubleshooting the devices that are currently connected to their home networks [64]. IoT devices will worsen these circumstances, as subscribers connect an increasingly wide variety of devices to their home networks. The consumer will likely lose track of what devices are connected to the Internet over time, which will make defend them even more challenging. In this section, we are discussing guidelines for secure the IoT devices.
9.1 Don’t Connect Your Devices Unless You Necessity
The first step is to consider what functionality you necessity from the device. In view of the, your TV or
fridge can connect to the internet, doesn’t mean you
features it offers and learn precisely what internet connectivity brings before you connect.
9.2 To Secure Communications Using Encrypted Protocols
Encryption practices of IoT devices are lower and unsafe. A small number devices use encrypted communications as part of their beginning configuration. Instead, most use ordinary web protocols that communicate across the Internet in plain text, which makes them simple targets for hackers keep an eye on network traffic to identify debility. At the very least, all webs, traffic should be using HTTPS [65], transport layer security, secure file transfer protocol, DNS security extensions, and other secure protocols for communications with management stations and across the Internet. Therewith, devices that connect to mobile apps or other remote gateways should use encrypted protocols as well as encrypt data stored on flash drives.
9.3 Block Incoming Traffic When Possible
The several IoT devices ship with open ports to support management functions rather than the standard functionality available through a user interface. Even some passwords allow telnet access with only an IP address. Afterwards, the point here is to decrease your attack surface as much as feasibly possible. That might mean perfectly blocking all incoming traffic with a firewall. However, in other cases, that will mean only keeping open which TCP and UDP ports you necessity.
9.4 Two-Factor Authentication
Supposing any of your devices offer two-factor authentication, use it. Two-factor authentication is an extra security layer on top of a device password that need secondary authentication a one-time code
sent through email or SMS before access is permitted. When used properly, two-factor authentication can halt the bad people obtain access to your accounts and taking control of your IoT devices.
9.5 Using the Latest Firmware
If you want to make sure you have the latest security patches and diminish the possibility of a successful attack, then you need to keep your firmware fully updated. Vulnerabilities and exploits will be extricated as they emerge, so your IoT devices and your router need to be frequently updated. Automate this wherever possible or set a schedule to investigate for updates every two months or so.
9.6 During Processing Using a Encrypt Data
Infrequently the party processing the data should not be able to read the data or the computational outcome. The operational data while they are in encrypted form. For instance, identical encryption is a form of encryption that permits computations to be carried out on cipher-text, thus generating an encrypted outcome that, when decrypted, matches the outcome of operations performed on the plain text.
9.7 Create Impressive and Inoffensive Password Policies
Most network infrastructure needs the administrator’s
address and control the device’s configuration and
operation.
9.8 Investigate if Physical Access Assents Intrusion
It is obliged to understand how your attack surface dissimilar in the case that a hacker is remote versus, when they are corporeally in the office location. There are a number of attached devices that are vulnerable subsequently doing a hard reset. If there are any, consider locking them away, when feasible.
9.9 Decrease Data Granularity
The IoT applications should appeal the minimum level of granularity that is needed to perform their most important tasks. A higher level of granularity could lead to secondary data usage and in conclusion privacy violations.
9.10 Ameliorate Failover Design
The devices should function when Internet connectivity is vanished or interrupted. However, few IoT devices are designed to face with the lack of success, such as Internet continuity or data disconnections. Failover design is especially vital for IoT devices that involve user protection, like as video monitoring, door lock mechanisms, and environmental monitors and alarms. These devices should have manual overrides or particular functions for disconnected operations.
9.11 Careful of the Cloud Services
Many IoT devices rely on cloud services, but the need for an internet connection in order for something to function can be a real difficulty. Not only will it not work when the network is very slow, but it may also be synchronized sensitive data or offering another potential route into your home and make sure you
read up on the provider’s privacy policy and look for
commitment about encryption and data safety.
9.12 Put IoT Devices on Their Personal Firewalled and Monitored Network
When it comes to linked consumer grade IoT devices in the enterprise, you need to take a proactive procedure. You want to have them segmented away and rear a firewall. You can block incoming traffic to it so people cannot attack from the inboard and you can handle and monitor it closely.
9.13 Disable UPnP Characteristics
The IoT devices tend to have Universal Plug in and Play (UPnP) characteristics, enabling various devices to explore and connect to one another. Whilst this is favorable and removes the need to configure each device individually, the protocols rely on local networks to connect to each other and these are vulnerable to third party attackers.
9.14 Conduct Risk Assessment
After choosing the devices, check-up the network and its potential lapse points, as well as the IoT and Cloud platform used for handling and storage of data. Many simpler IoT devices have no computing power and communicate with a gateway and the idea should be given to choosing a remote monitoring service or IoT service platform.
X. CONCLUSION
will be personalized. Much of the value of the IoT comes from the capability to customize products and services to a client individually and immediately, necessity. The analysts have a prophecy that hundreds of thousands of new IoT services will connect billions of new IoT devices over the next decade. Industry and academia are both concentrating on moving ahead in attempts to improve usability, maintainability, and security via standardization and development of best practices. The Internet of Things (IoT) embodies the convergence of the physical and virtual worlds. It is the important nexus between data-oriented applications and device-oriented sensor networks facilitated by Internet technologies. The biggest challenges to the IoT will come in securing sensitive information from unauthorized access as well as authorizing access to only the information we're comfortable disclose. This paper provides an overview of Internet of Things (IoT) threats, scheme and faith. Afterwards, we are briefly discussing public key infrastructures and guidelines for secure the IoT devices.
XI. REFERENCES
[1]. Yusuf Perwej, Mahmoud A. AbouGhaly, Bedine
K. Hani Ali M. Harb, “An Extended Review on
Internet of Things (IoT) and Its Promising
Applications”, Communications on Applied
Electronics (CAE), ISSN: 2394-4714, Foundation of Computer Science FCS, New York, USA, Volume 9, Number 26, Pages 8– 22, Feb 2019, DOI: 10.5120/cae2019652812
[2]. Yusuf Perwej, “An Experiential Study of the Big Data,” International Transaction of Electrical
and Computer Engineers System (ITECES), USA, ISSN (Print): 1273 ISSN (Online): 2373-1281, Vol. 4, No. 1, page 14-25, March 2017, DOI:10.12691/iteces-4-1-3.
[3]. Nikhat Akhtar, Firoj Parwej, Dr. Yusuf Perwej,
“A Perusal of Big Data Classification and Hadoop
Technology,” International Transaction of
Electrical and Computer Engineers System (ITECES), USA, ISSN (Print): 2373-1273 ISSN (Online): 2373-1281, Vol. 4, No. 1, page 26-38, May 2017, DOI: 10.12691/iteces-4-1-4.
[4]. Luigi Atzori, Antonio Iera, and Giacomo Morabito. The internet of things: A survey. Computer Networks, 54(15):2787–2805, 2010. [5]. Gartner Inc. Press Release (2014)
http://www.gartner.com/newsroom/id/2905717 [6]. G. Wu, S. Talwar, K. Johnsson,N. Himayat, and
K. D. Johnson, “M2M: from mobile to embedded internet,” IEEE Communications Magazine, vol.
49, no. 4, pp. 36–43, 2011.
[7]. L. Atzori, A. Iera, and G. Morabito, “The internet of things: a survey,” Computer
Networks, vol. 54, no. 15, pp. 2787–2805, 2010. [8]. Gartner Inc., “Hype cycle for the internet of
things 2017,” Technical report, July 2017.
[9]. V. Karagiannis, P. Chatzimisios, F. Vazquez-Gallego, J. Alonso-Zarate, "A survey on application layer protocols for the internet of things", Transaction on IoT and Cloud Computing, vol. 3, no. 1, pp. 11-17, 2015.
[10].Xiaolin Jia, Quanyuan Feng, Taihua Fan, Quanshui L. , ”RFID technology and its applications in Internet of Things (IoT)”, 2nd
International Conference on Consumer Electronics, Communications and Networks (CECNet), IEEE, Yichang, China, April 2012 [11].Nasser S. A., Andrew J., Olga A.,” Internet of
Things Security: A Review of Risks and Threats
to Healthcare Sector ”, IEEE International
Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Exeter, UK, June 2017
[12].Wei Z., Yan Jia., Anni P., Yuqing Z., Peng
L.,”The Effect of IoT New Features on Security
and Challenges Yet to Be Solved”, IEEE Internet
of Things Journal, June 2018
[13].J. Gubbia, R. Buyya, S. Marusic, M. Palaniswami, "Internet of Things (IoT): A vision architectural elements and future directions" in Future Generation Computer Systems, Elsevier, vol. 29, pp. 1645-1660, 2013.
[14].R. H. Weber, "Internet of Things New security and privacy challenges", Computer Law & Security Review, vol. 26, no. 1, pp. 23-30, Jan. 2010.
[15].M. O. Lehtonen, F. Michahelles, E. Fleisch, "Trust and Security in RFID-Based Product Authentication Systems", IEEE Systems Journal, vol. 1, no. 2, pp. 129-144, Dec. 2007.
[16].Yusuf Perwej, Kashiful H., Uruj J., Firoj Perwej,
“Block ciphering in KSA, A major breakthrough in cryptography analysis in wireless networks”
International Transactions in Mathematical Sciences and Computer, India, ISSN-0974-5068, vol. 2, No. 2, pages 369-385, July-December 2009
[17].G. Gan, Z. Lu, J. Jiang, "Internet of Things Security Analysis", 2011 International Conference on Internet Technology and Applications, pp. 1-4, Aug. 2011.
[18].I. Gudymenko, K. B. Pfitzmann, K. Tietze, "Privacy implications of the internet of things" in Constructing Ambient Intelligence, Springer, pp. 280-286, 2012
[19].Marianne Azer, Sherif Kassas, Magdy
El-Soudani, “A full of the Wormhole Attack”,
International Journal of Computer Science and Information Security, 2009.
[20].Kelly Jackson, “Hacker’s Choice: Top Six
Database Attacks.
[21].Ş. Okul ; M. Ali Aydın,” Security Attacks on IoT ”, International Conference on Computer
Science and Engineering (UBMK), IEEE, Antalya, Turkey, Oct. 2017
[22].Elisa Bertino, Nayeem Islam,” Botnets and
Internet of Things Security ”. Computer, IEEE,
Volume 50 , Issue 2, Feb 2017
[23].A. Mohsen Nia and N. K. Jha, “A Comprehensive
Study of Security of Internet-of-Things,” IEEE
Transactions on Emerging Topics in Computing, vol. PP, no. 99, p. d, 2016.
[24].Kuan Zhang, Xiaohui Liang, Rongxing Lu,
Xuemin Shen,” Sybil Attacks and Their Defenses in the Internet of Things”, IEEE Internet of
Things Journal , Volume 1 , Issue 5 , Oct. 2014 [25].Ian G. Harris,” Social Engineering Attacks on the
Internet of Things ”, September 7, 2016
[26].L. Atzori, A. Iera, G. Morabito, "The Internet of Things: A survey", Comput. Netw., vol. 54, no. 15, pp. 2787-2805, 2010.
[27].E. Haselsteiner and K. Breitfuß, “Security in
Near Near Field Communication (NFC)
Strengths,” Semiconductors, vol. 11, no. 71, p.
71, 2006.
[28].Seo JW, Lee SJ,”A study on the detection of DDoS attack using the IP Spoofing”, J Korea Inst
Inf Secur Crytol 25(1):147-153, 2015
[29].D. Miessler, “Securing the Internet of Things:
Mapping Attack Surface Areas Using the OWASP IoT Top 10.
[30].G. Hernandez, O. Arias, D. Buentello, and Y. Jin,
“Smart Nest Thermostat : A Smart Spy in Your Home,” Black Hat USA, pp. 1–8, 2014.
[31].Pin-Yu Chen, Shin-Ming Cheng, and Kwang-Cheng Chen. Optimal control of epidemic information dissemination over networks. IEEE Trans. Cybern., 44(12):2316–2328, December 2014.
[32].Pin-Yu Chen and Shin-Ming Cheng. Sequential defense against random intentional attacks in complex networks. Phys. Rev. E, 91:022805, February 2015.
[34].Pin-Yu Chen and Alfred O. Hero. Assessing and safeguarding network resilience to nodal attacks. IEEE Commun.Mag., 52(11):138–143,November 2014.
[35].D. Quercia and S. Hailes, “Sybil attacks against mobile users: Friends and foes to the rescue,” in
Proc. IEEE IEEE Conf. Comput. Commun. (INFOCOM), 2010, pp. 336–340.
[36].W. Chang, J. Wu, C. Tan, and F. Li, “Sybil defenses in mobile social networks,” in Proc.
IEEE Conf. Global Commun. (GLOBECOM), 2013, pp. 1–6.
[37].Pin-Yu Chen and Kwang-Cheng Chen. Intentional attack and fusion-based defense strategy in complex networks. In Proc. IEEE Global Telecommunications Conference (GLOBECOM), pages 1–5, December 2011. [38].Pin-Yu Chen, Shin-Ming Cheng, and
Kwang-Cheng Chen. Information fusion to defend intentional attack in internet of things. IEEE IoT-J., 1(4):337–348, August 2014.
[39].J. Tian, W. Zhao, R. Du, and Z. Zhang, “A New
Data Fusion Model of Intrusion Detection-IDSFP,” in Parallel and Distributed Processing
and Applications, vol. 3758 of Lecture Notes in Computer Science, pp. 371–382, Springer Berlin Heidelberg, Berlin, Heidelberg, 2005.
[40].Martin Osborne and Ariel Rubinstein. A Course in Game Theory. MIT, Cambridge, MA, 1999. [41].S. Sicari, A. Rizzardi, L. A. Grieco, A.
Coen-Porisini, "Security privacy and trust in Internet of Things: The road ahead", Computer Networks, vol. 76, pp. 146-164, Jan. 2015. [42].T. Eder, D. Nachtmann, D. Schreckling, "Trust
and Reputation in the Internet of Things", Conference Seminar (SS2013) - Real Life Security (5827HS), Dec. 2013.
[43].Z. Yan, P. Zhang, A. V. Vasilakos, "A survey on trust management for Internet of Things", Journal of Network and Computer Applications, vol. 42, pp. 120-134, Jan. 2014.
[44].J. Guo, R. Chen, "A Classification of Trust Computation Models for Service-Oriented Internet of Things Systems", IEEE International Conference on Services Computing (SCC), pp. 324-331, June 2015.
[45].Ie yuan, Xiaoyong li,” A Reliable and
Lightweight Trust Computing Mechanism for IoT Edge Devices Based on Multi-Source
Feedback Information Fusion”, special section
on security and trusted computing for industrial internet of things, volume 6, May 16, 2018 [46].P. Porambage, C. Schmitt, P. Kumar, A. Gurtov,
M. Ylianttila, "Two-phase authentication protocol for wireless sensor networks in distributed IoT applications", Proc. IEEE Wireless Commun. Netw. Conf. (WCNC), pp. 2728-2733, Sep. 2014
[47].E Vasilomanolakis, J Daubert, M Luthra, V Gazis, A Wiesmaier, P. Kikiras, "On the Security and Privacy of Internet of Things Architectures and Systems", 2015 International Workshop on Secure Internet of Things (SIoT), pp. 49-57, Sep 2015
[48].Chen, D., Chang, G. R., Sun, D. W., Li, J. J., Jia.
J., and Wang. X. W.,”TRM-IoT: A Trust Management Model Based on Fuzzy Reputation
for Internet of Things”, Computer Science and
Information Systems.,1207-28, October 2010 [49].Michael Schukat, Pablo Cortijo,” Public key
infrastructures and digital certificates for the
Internet of things”, 26th Irish Signals and
Systems Conference (ISSC),IEEE, Carlow, Ireland, June 2015
[50].Zhiyong Zhang, Qingqi Pei, Jianfeng Ma, Lin Yang, "Security and Trust in Digital Rights Management: A Survey", International Journal of Network Security, vol. 9, no. 3, pp. 247-263, 2009.
Infrastructure Springer Berlin, Heidelberg", vol. 4043, pp. 248-250, June 2006.
[52].Yun-kyung Lee, Hong-il Ju, Jee-hye User, authentication mechanism using authentication server in homnetwork Advanced Communication Technology, pp. 504-506, 2006. [53].Gianmarco Baldini, Trevor Peirce, Maria Chiara
Tallachini, "Internet of Things: IoT Governance European Research Cluster on the Internet of Things, Jan. 2014
[54].M. Bauer, P. Chartier, K. Moessner, Catalogue of IoT Naming, Addressing and discovery schemes in IERC projects V1.7, IERC-AC2-D1, 2013. [55].AS. Wazan, R. Laborde, F. Barrère, A. Benzekri,
"Validating X. 509 certificates based on their quality", Young Computer Scientists 2008. ICYCS 2008. The 9th International Conference for IEEE, pp. 2055-2060, November 2008.
[56].J. Shannon, H. Melvin, A. G. Ruzzelli, Dynamic flooding time synchronization protocol for WSNs, IEEE GLOBECOM, 2012.
[57].P. Camion, J. Patarin, "The knapsack hash function proposed at Crypto'89 can be broken", Adv. in Cryptology Proc. Eurocrypt'91, pp. 39-53, 1991.
[58].Yusuf Perwej, Kashiful H., Uruj J., Sharad S.,
“Some drastic improvements found in the
analysis of routing protocol for the Bluetooth technology using scatternet” International
Conference on Computing, Communications and Information Technology Applications (CCITA-2010), Ubiquitous Computing and Communication Journal (UBICC) Seoul, South Korea, ISSN Online 1992-8424, ISSN Print 1994-4608, Volume CCITA-2010, Number 5, pages 86-95, 2010
[59].J. Granjal, E. Monteiro, J. Sá Silva, "Security for the Internet of Things: A survey of existing protocols and open research issues", IEEE Commun. Surveys Tuts., vol. 17, no. 3, pp. 1294-1312, 3rd Quart. 2015
[60].Borislav S. Đorđević, Slobodan P. Jovanović, Valentina V. Timčenko, ” Cloud Computing in
Amazon and Microsoft Azure platforms:
Performance and service comparison ”, 22nd
Telecommunications Forum Telfor (TELFOR),IEEE, Belgrade, Serbia, Nov. 2014 [61].R. Tudoran, A. Costan, G. Antoniu, L. Bougé, "A
performance evaluation of azure and nimbus clouds for scientific applications", Proceedings of the 2nd International Workshop on Cloud Computing Platforms, pp. 4, 2012.
[62].R. Giuliano, A. Neri, and D. Valletta, “End -to-end secure connection in heterogeneous
networks for critical scenarios”, WIFS 2012,
Proc. of the 2012 IEEE Intl. Workshop on Information Forensics and Security, pp. 264–
269, Tenerife, Spain.
[63].Ka-Ping Yee, "Aligning security and usability." IEEE Security & Privacy 2.5, pp 48-55, 2004 [64].Rebecca E. Grinter, et al., "The work to make a
home network work." ECSCW 2005. Springer Netherlands, 2005
[65].A. P. Castellani, M. Gheda, N. Bui, M. Rossi, and M. Zorzi, "Web Services for the Internet of Things through CoAP and EXI," in IEEE RWFI, Kyoto, Japan, Jun. 2011
Cite this article as :
Dr. Yusuf Perwej, Firoj Parwej, Mumdouh Mirghani Mohamed Hassan, Nikhat Akhtar, "The Internet-of-Things (IoT) Security : A Technological Perspective and Review ", International Journal of Scientific Research in Computer Science, Engineering and Information Technology (IJSRCSEIT), ISSN : 2456-3307, Volume 5 Issue 1, pp. 462-482, January-February 2019. Available at doi : https://doi.org/10.32628/CSEIT195193