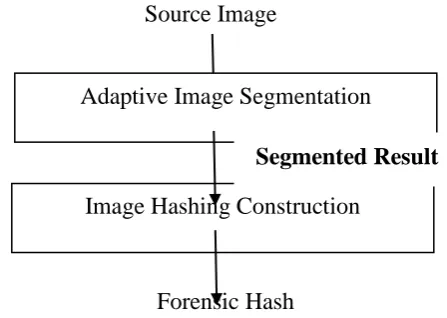
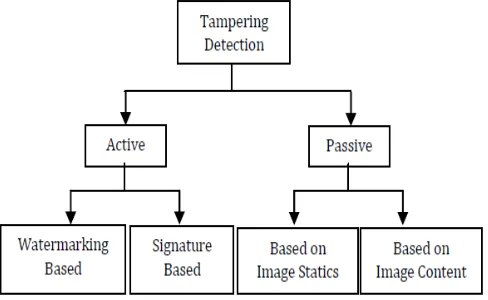
Study and Investigation of Tampering Detection Methods Based on Image Hashing
Full text
Figure
Related documents
As with other cytosolic bacteria, vacuolar acidification played a role in CAB2 escape into the cytosol, since pharmacolog- ical blockage of vacuolar acidification caused a
Intraindividual comparisons of the fecal microbiota compositions yielded small differences over time in Campylobacter -negative participants, but significant long-term changes
In conclusion, pravastatin is effective in lowering serum total cholesterol, LDL-cholesterol and triglyceride and increasing serum HDL-cholesterol. The drug is well
The time course analysis of degradation of filter paper was performed using a 5% (wt/vol) concentration of the substrate and. 3 M enzyme (GH5 plus GH9, 1.5 plus 1.5
Herpes simplex virus (HSV) encodes two proteins with potential RNase H-like folds, the infected cell protein 8 (ICP8) DNA-binding protein, which is necessary for viral DNA
Because IFN- ␥ and TNF- ␣ levels were different in the lungs of mice infected with the three different strains at a high sublethal dose, we evaluated the levels of these cytokines
The parents were instructed by the Social Welfare Officers to bring the child to the local district hospital, where a diagnosis of transverse fracture of the
Gene editing by homologous repair of DSBs introduced by CRISPR/Cas9 requires only transient expression of Cas9/sgRNA from a plasmid; no integration of selection marker or other