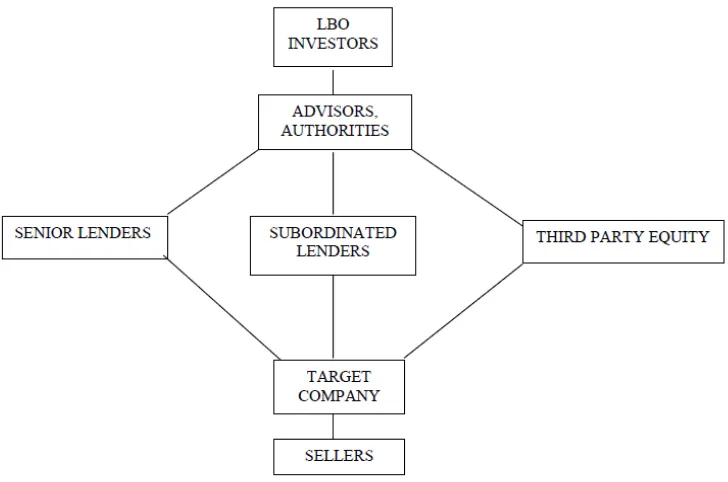
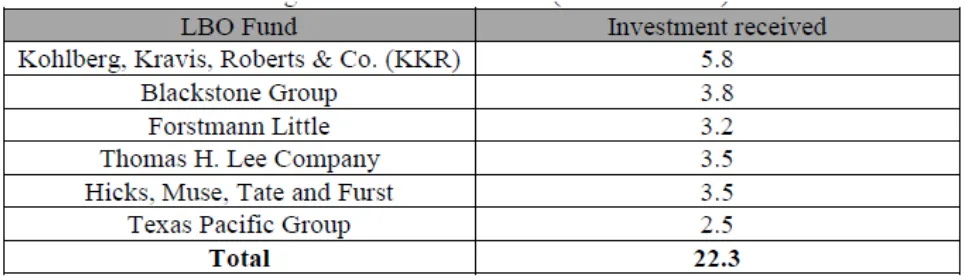
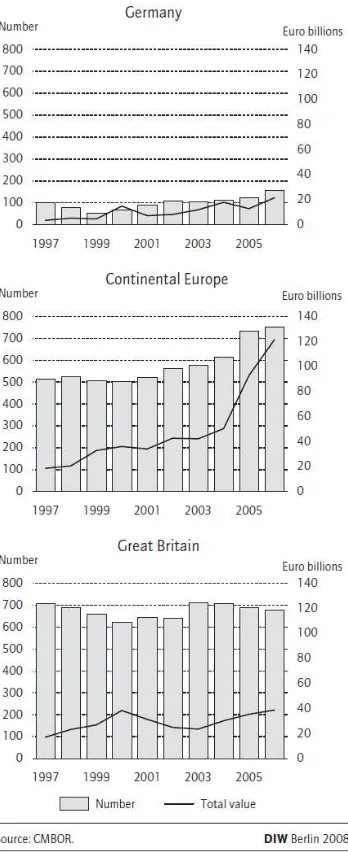
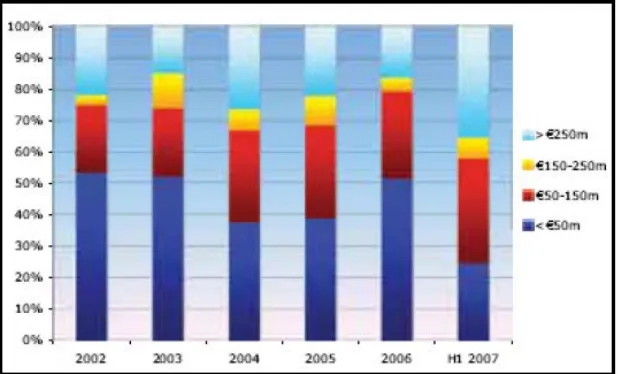
On the fundamentals of winning virtuous strategies creation toward leveraged buyout transactions implementation during private equity investment in conditions of resonant absorption of discrete information in diffusion type financial system with induced
Full text
Figure

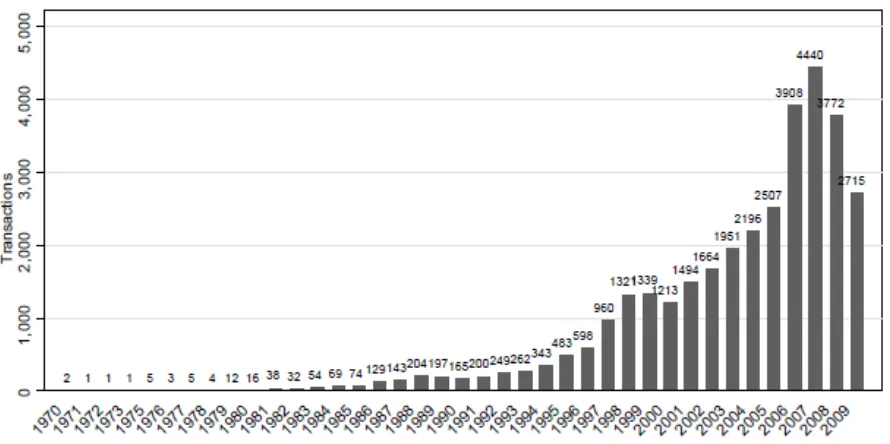

Outline
Related documents
- Paolo Sbraccia, President of the Italian Obesity Society (SIO), University of Rome Tor Vergata, Vice President IBDO Foundation.
The two step approach that we illustrated is a semi-parametric method that uses the non-parametric empirical distribution to capture the small risks and the parametric method based
Explanatory variables are the change of the internal rating ( Δ RAT), the credit line usage ( Δ USAGE), the absolute checking account amplitude ( Δ AMPLI), the credit-to-limit ratio
2 MSc.; Bacharel em Química; Doutoranda no Programa de Pós-Graduação em Física Ambiental/Instituto de Física da Universidade Federal de Mato Grosso, UFMT; Endereço:
[r]
บันทึกหลักการและเหตุผล ประกอบรางขอบัญญัติองคการบริหารสวนตําบล เรื่อง การกําจัดสิ่งปฏิกูลและมูลฝอย
A planting date of two weeks is suggested for cover crops such as cereal rye ( Secale Cereale ) and ones in the brassica family (Ngouajio, 2011). Due to the limited season,
We describe active attacks in which an adversary chooses an ar- bitrary set of users whose privacy it wishes to violate, creates a small number of new user accounts with edges to