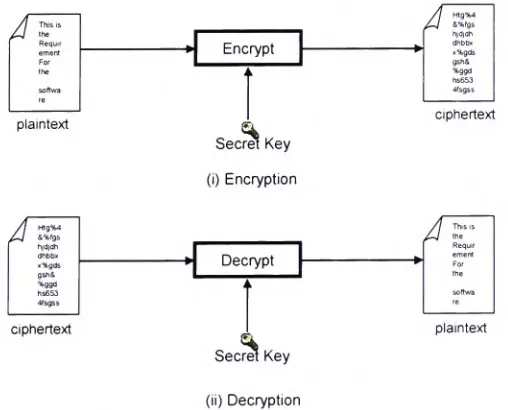
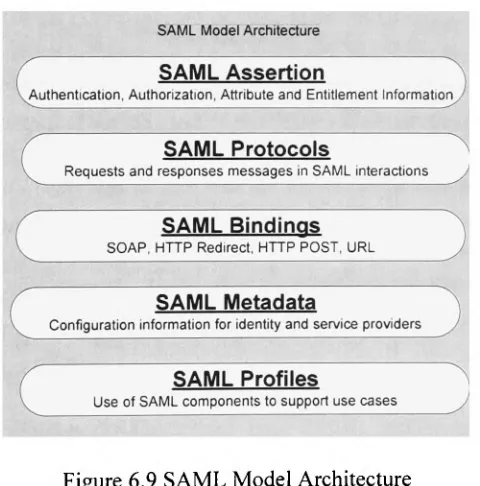
Privacy trust access control infrastructure using XACML
Full text
Figure




Related documents
Methods: We present a sensitive surface-enhanced Raman scattering (SERS) biosensor based on the combination of vancomycin-modified Ag-coated magnetic nanoparticles (Fe 3 O 4 @Ag-
Our key findings, which are elaborated upon in section 4 are as follows: (1) The variation in infection risk and contacts budget across regions is huge, much more than may be
receipt of all vaccines such as: an original signed certificate of immunization, a New York State Immunization Information System (NYSIIS); or New York Citywide
For ideas that become innovation projects, the innovation management process works well, and successful idea proposers commend the project group and the support they provide in
In our implementation we have used wavelet packet transform followed by GLCM Unit as Feature Extractor (FE) for iris pattern and Gabor filter for palm print pattern. The
You are invited to participate in a research study because you are a student in a Georgia State University choral class. The purpose of the study is to investigate
Hotchkins, Bryan; Hotchkins, Nedra; Bellot, Bianca; and Parker, Laurence (2019) "First year college student success for Black and other students of color: A Village initiative