Performance Analysis of Key Establishment Protocols for Secure System
Full text
Figure
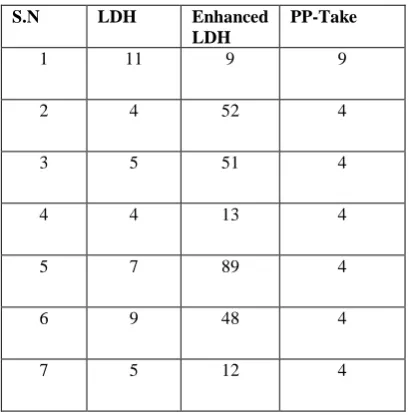
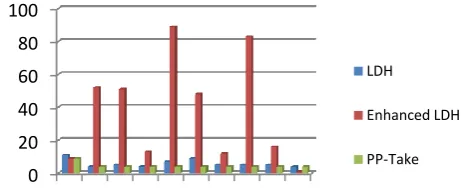
Related documents
( 2007 ) tested the bond properties of Glass Fiber Reinforced Polymer (GFRP) bars and concrete with sticky sand, the results show that the bond strength decreases with the
exterminate all of the Jews. Mordecai persuaded Esther to speak to the king on behalf of the Jewish people. This was a dangerous thing for Esther to do, because anyone who came
Abstract: Intelligent sys tems based on machine learning techniques. such as classification. are gaining Wide spread popularity in real world applications. This paper presents work
To illustrate the performance of the proposed approach for real-world problems, we seek the geometry optimal solution for the 21-bar truss shown in Figure 2.. Node locations of 11
Note: Remember that there are only 30 channels available to store frequencies, whether you program them directly or while using the Chain Search mode....
Note If you did not check the Print Credit Card Number on Statement field on the Settings screen, the Credit Card Number field on this screen is not active. ...or click Off to stop
In this respect, solid pineapple waste has an interesting potential for selenium sorption to remove selenium from wastewater, as well as a means for enrichment
Although the data we have analysed so far show clear tendencies in the way abstract pronominal reference occurs in Danish and Italian and confirm some of the observations done by