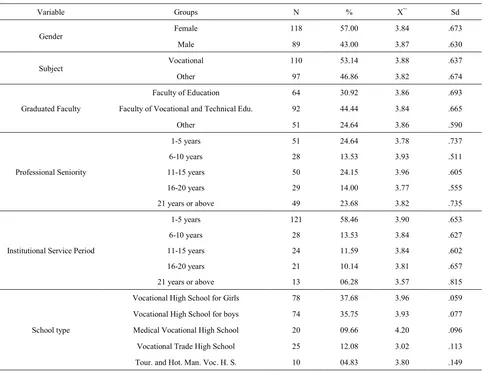
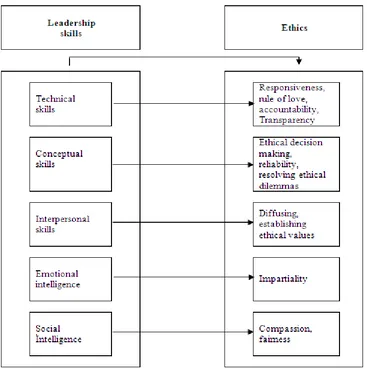
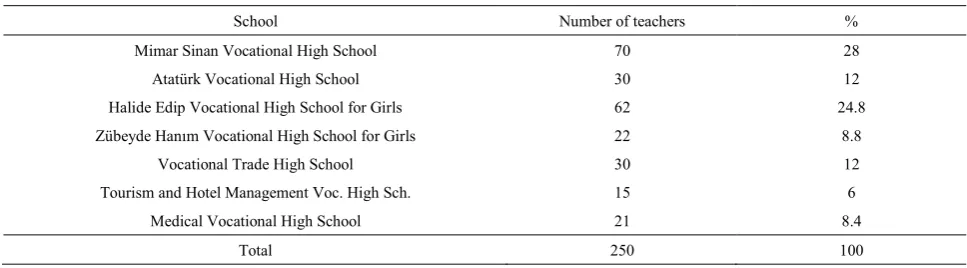
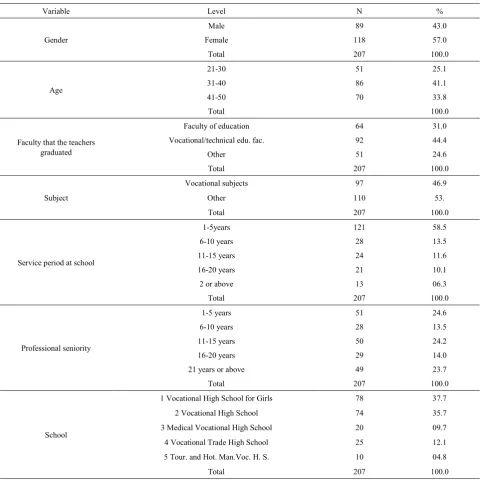
Teachers' Perceptions about the School Principals' Ethical Leadership Behaviours: A Study from Turkish Vocational High Schools
Full text
Figure
Related documents
We addressed the impact of radiation on glioblastoma evolution and potential treatment implications by examining the influence of intratumoral heterogeneity (ITH) on
For so many governments within the region, such failures to address these and other problems and their inability to provide their nations with good governance that can boost
Controller Data Plane Applications Vendor- specific APIs OpenFlow, PCEP, I2RS Traditional SDN Vendor Specific (e.g. onePK) Controller Data Plane Applications
For example, the configuration may include a few (perhaps plywood models of) racks and a single CRAC (Computer Room A/C) unit. The laboratory configuration will necessarily
Based on the fact that three identical cards (same product, same moment and place of purchase, same expiry date, same purchase transaction), which should only differ in their UID’s
Now, the Classifiers are used which are trained using the computed features.In the previous sub-section that coiflet wavelet transform’s D 4 coefficient of the EMG signals
This evaluation examined the extent to which the weight loss initiative presented barriers to participation, aligned with the goals of its members, provided access to staff
A side-channel is an information leakage channel that can be used by the attacker to gain insight into the victim application. An access-driven side- channel attack consists of